by Josef Weiss
September 17, 2025
The Cyber Essentials is a UK government-backed framework which is designed to assist organisations in protecting themselves against common threats. The Cyber Essentials provides a basic cyber security foundation that can serve as a stepping stone to a more comprehensive zero-trust approach. The Cyber Essentials is built on 5 key components that, when implemented correctly, can reduce cyber risk. The five key components are:
- Firewalls and Boundary Devices
- Secure Configurations
- Access Control
- Malware Protection
- Patch Management
Tenable has released a series of dashboards, that focuses on each of the five basic technical controls, which organisations can use to help strengthen their defences against the most common cyber threats.
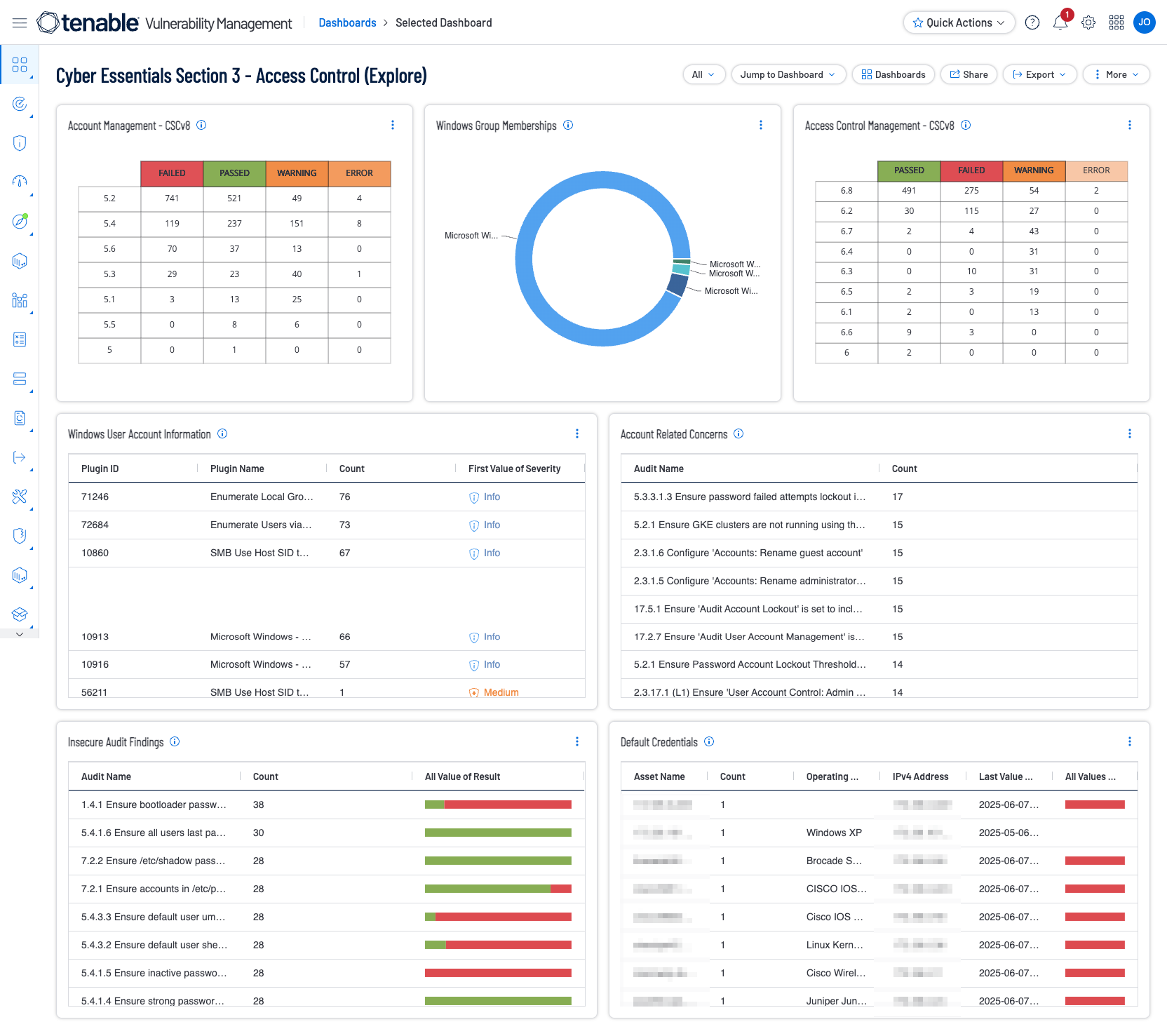
The focus of this dashboard is Section 3 - Access Control. This key requirement supports the goal of reducing an organisation’s risk from the most common cyber threats. The Cyber Essentials focuses on preventing high impact attacks, such as phishing, malware infection, and unauthorized access. Strong access control can limit the number of accounts which attackers can compromise, ensuring that individuals only have access which is required to perform job functions.
This key component applies to all the following in scope devices: Boundary Firewalls, Desktop Computers, Laptops, Routers, Servers, Iaas, PaaS, and SaaS devices. Some items to focus on within this key component are:
- Administrative privileges are tightly controlled and monitored
- No shared accounts, every user must have their own unique account for auditing
- Access is granted on the principles of least privilege
- Users should have the minimum level of privileges to carry out their duties
- Strong passwords must be enforced
- Stale accounts are removed
- User accounts should be reviewed regularly
- Use multi-factor authentication (MFA)
Widgets
Account Management - CSCv8 - This widget provides organizations with information which specifically measures against the compliance standards related to the Center for Internet Security (CIS), Critical Security Controls, Version 8
Windows Group Memberships - The Windows Group Memberships (Explore) widget displays information for Windows default groups such as administrators, server operators, account operators, backup operators, print operators, and replicator groups.
Access Control Management - CSCv8 - This widget provides organizations with information which specifically measures against the compliance standards related to the Center for Internet Security (CIS), Critical Security Controls, Version 8
Windows User Account Information - This widget displays information derived from enumeration of Windows accounts via Windows Management Instrumentation (WMI).
Account Related Concerns - This table displays the top compliance issues related to audit results related to 'account' data. Note that in order for data to appear in this table, appropriate audit/compliance scans must first be run on the network.
Insecure Audit Findings - The Insecure Audit Findings table lists known insecure audit findings which may induce weaknesses in the environment, such as weak password policies.
Default Credentials - The Default Credentials table lists known default credentials in the environment.