by Josef Weiss
September 17, 2025
The Cyber Essentials is a UK government-backed framework which is designed to assist organisations in protecting themselves against common threats. The Cyber Essentials provides a basic cyber security foundation that can serve as a stepping stone to a more comprehensive zero-trust approach. The Cyber Essentials is built on 5 key components that, when implemented correctly, can reduce cyber risk. The five key components are:
- Firewalls and Boundary Devices
- Secure Configurations
- Access Control
- Malware Protection
- Patch Management
Tenable has released a series of dashboards, that focuses on each of the five basic technical controls, which organisations can use to help strengthen their defences against the most common cyber threats.
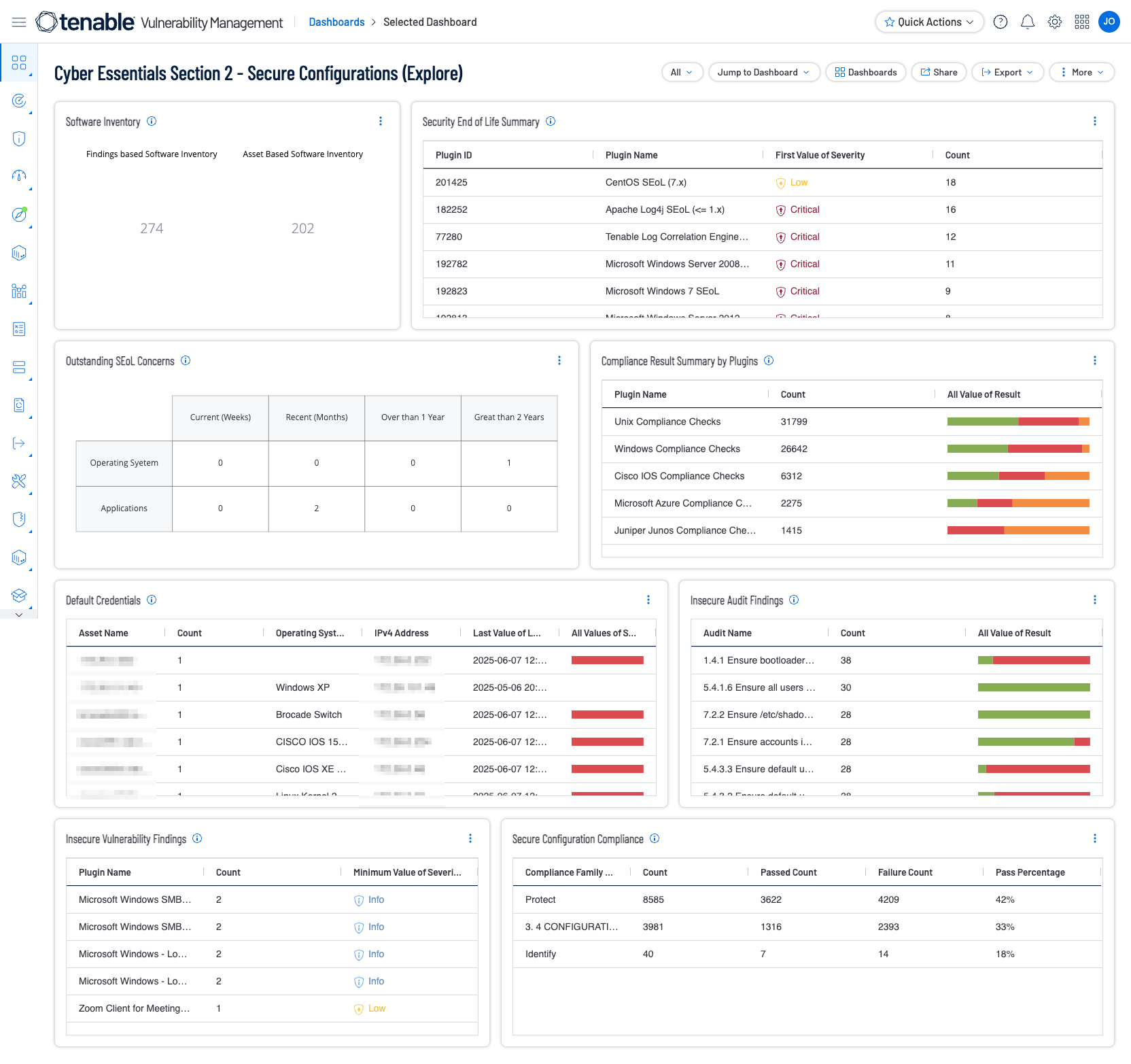
Misconfigured systems are often easy targets for attackers. The focus of this dashboard is Section 2 - Secure Configurations which focuses on ensuring that computers and network devices are set up in the most secure method to reduce vulnerabilities and reduce organisations risk of exposure.
Secure Configuration (also called security hygiene) is ensuring that devices and software are configured in the most secure way possible to reduce vulnerabilities and exposure to cyber threats. Unused software or services can introduce exploitable vulnerabilities. Default accounts and passwords are widely known and easy to exploit. The focus of this section applies to: servers, desktop computers, laptops, tablets, thin clients, mobile phones, IaaS, PaaS and SaaS.
A secure configuration is your first line of defense. Default configurations and installations are not always secure. Secure configuration begins with the identification and removal/disabling of unnecessary accounts, applications, and services, organisations can minimize vulnerabilities.
Widgets
Software Inventory - The Software Inventory widget displays findings from Tenable software enumeration plugins.
Security End of Life Summary - The Security End of Life Summary table displays products that have entered the Security End of Life state of the Security Maintenance Lifecycle.
Outstanding SEoL Concerns - The Outstanding SEoL Concerns widget displays assets counts by two categories, Operating System and Application.
Compliance Result Summary by Plugins - The Compliance Result Summary by Plugins (Explore) widget provides a list of the most scanned compliance plugins.
Default Credentials - The Default Credentials table lists known default credentials in the environment.
Insecure Audit Findings - The Insecure Audit Findings table lists known insecure audit findings which may induce weaknesses in the environment, such as weak password policies.
Insecure Vulnerability Findings - The Insecure Vulnerability Findings table lists known insecure vulnerability findings, which may include items such as plain text usernames and passwords.
Secure Configuration Compliance - The Secure Configuration Compliance table displays details related to a number of checks related to other known compliance frameworks, such as the CSF, 800-53, 800-171, and more. Where the focus is secure configurations.