by Josef Weiss
October 9, 2024
The Payment Card Industry Security Standards Council (PCI SSC) maintains, evolves, and promotes Payment Card Industry standards for the safety of cardholder data across the globe. The PCI SSC provides organizations with technical and operational requirements for organizations accepting or processing payment transactions, and for software developers and manufacturers of applications and devices used in those transactions.
The Payment Card Industry Data Security Standard (PCI DSS) helps entities understand and implement standards for security policies, technologies and ongoing processes that protect their payment systems from breaches and theft of cardholder data. The standards have historically been revised on a 2-3 year cycle, but the PCI SSC is transitioning to a posture of revising the PCI DSS as required based on changes to the current threat landscape. The current standard revision is PCI DSS Version 4.x. Any organization that handles payment card information must comply with the PCI DSS and must demonstrate compliance annually. Tenable Vulnerability Management is able to help organizations monitor ongoing PCI DSS compliance.
Users of all access control levels play an important part in all organizations. Some users ensure the security of an organization whereas others further the business goals. Regardless of the user account, if the user account is active and has permissions, there could be a possibility of compromise. Analysts need to ensure that care is taken to protect all user accounts and monitor for suspicious activity. Many organizations have a sense of belief that all user accounts are trusted within the network boundaries and are performing authorized activities. Attackers use various techniques to get credentials of any user account possible to get a foothold into the inside of the organization. Tenable has products such as Nessus, and NNM to provide organizations with a continual view into the network. Using these products within Tenable Vulnerability Management analysts can help detect threats to user accounts with tools such as this dashboard.
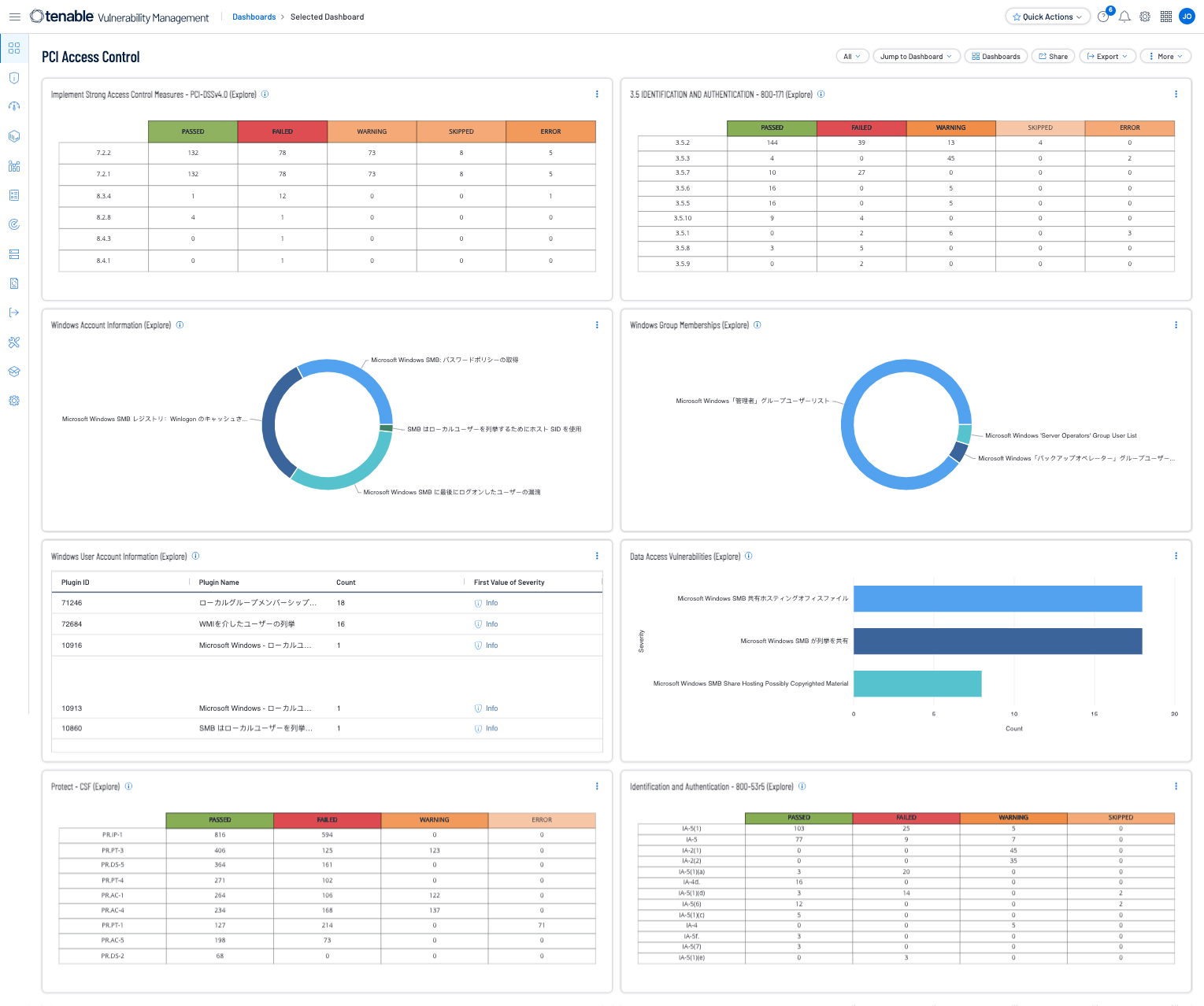
With this dashboard, organizations can assess their level of adherence with PCI security requirements focusing on access control. The widgets in this dashboard are focused on PCI Control Objective 4, Implement Strong Access Control Measures. The widgets in this dashboard cover elements within PCI Requirements 7, and 8.
Within this dashboard, user account focused widgets are provided to help analysts see activities detected in the organization around user accounts. All user accounts such as regular user accounts and administrative accounts should be monitored for unusual activity. Multiple industry recommendations from standards such as PCI and NIST CyberSecurity Framework (CSF) are provided to help analysts see potential malicious indicators around user accounts. Examples of these indicators, such as privilege changes and group membership changes, alert analysts as changes may not be expected and should be validated. Analysts can use these widgets to help determine what typical activity should be on a network and then be more aware of when abnormal activity takes place within the organization.
Organizations can configure repositories or asset lists in order to tailor the focus of the dashboard. After the dashboard is added from the Template Library, the appropriate assets can be specified for each widget on the dashboard. By creating tags and target groups that include all systems in the Cardholder Data Environment (CDE), each widget can be filtered to display results directly related to ongoing PCI security.
Tenable provides several solutions for organizations to better understand vulnerability management. Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable Vulnerability Management (formerly Tenable.io) discovers and analyzes assets continuously to provide an accurate and unified view of an organization's security posture. The requirements for this report are: Tenable Vulnerability Management.
Widgets:
- Implement Strong Access Control Measures - PCI DSSv4.0 (Explore) - This widget provides organizations with information which specifically measures against the compliance standards related to the Payment Card Industry Data Security Standard (PCI DSS).
- 3.5 Identification and Authentication - 800-171 (Explore) - This widget provides organizations with information which specifically measures against the compliance standards related to the 800-171 standards which represent a set of security controls and guidelines established by NIST.
- Windows Account Information (Explore) - This widget displays counts related to Microsoft Windows SMB plugins that focus on user account information.
- Windows Group Memberships (Explore) - This widget displays information for Windows default groups such as administrators, server operators, account operators, backup operators, print operators, and replicator groups.
- Windows User Account Information (Explore) - This widget displays counts for user accounts and security identifiers (SID).
- Data Access Vulnerabilities (Explore) - The Data Access Vulnerabilities chart lists the top ten vulnerabilities related to data access by count.
- Protect - CSF (Explore) - This widget provides organizations with information which specifically measures against the compliance standards related to the Cybersecurity Framework (CSF or Framework) established by NIST.
- Identification and Authentication - 800-53r5 (Explore) - This widget provides organizations with information which specifically measures against the compliance standards related to the Identification and Authentication (IA) family of 800-53r5.