by Cesar Navas
April 23, 2024
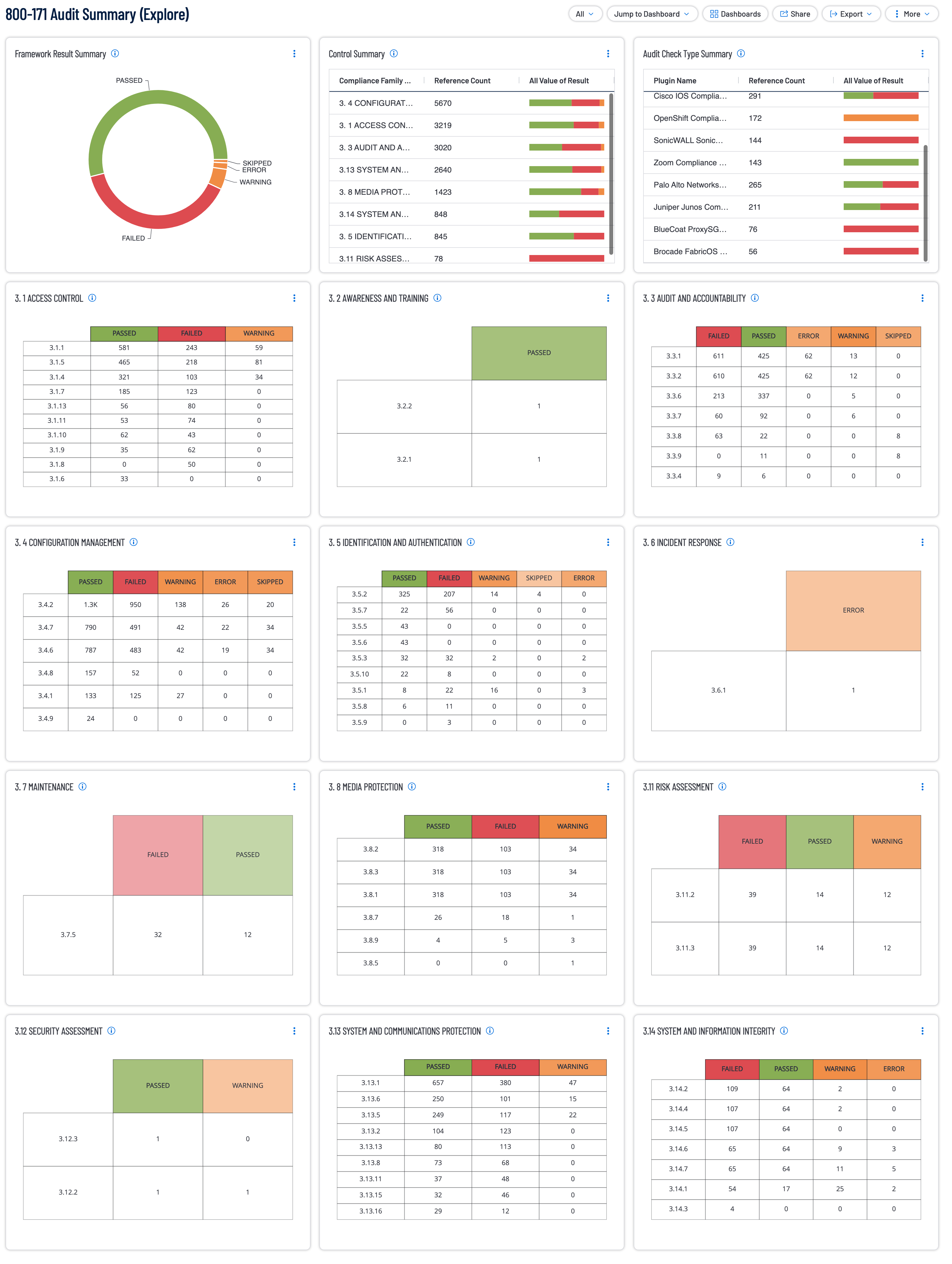
This dashboard provides organizations with information which specifically measures against the compliance standards related to the 800-171 standards which represent a set of security controls and guidelines established by National Institute of Standards and Technology (NIST). NIST 800-171 is a special publication that provides the recommended requirements for protecting the confidentiality of Controlled Unclassified Information (CUI), that is processed, stored, or transmitted by Department of Defense (DoD) government contractors and subcontractors.
CUI categorized as unclassified information that is created or possessed by the US Government, or an entity on behalf of the Government, requires safeguarding from unauthorized disclosure. DoD contractors who process, store, or transmit CUI for the DoD, GSA, NASA, or other federal or state agencies, including subcontractors are required, at the very least, to complete a basic self-assessment in reference to the controls in NIST 800-171.
NIST 800-171 contains 14 key areas: Access Control, Awareness and Training, Audit and Accountability, Configuration Management, Identification and Authentication, Incident Response, Maintenance, Media Protection, Physical Protection, Personnel Security, Risk Assessment, Security Assessment, System and Communications Protection, and System and Information Integrity. The US government relies heavily on external service providers and contractors to assist in carrying out a wide range of federal missions. Sensitive but unclassified federal information is routinely processed by, stored on, or transmitted through nonfederal information systems. Failing to properly protect this CUI could impact the ability of the federal government to successfully carry out required missions and functions. The NIST created Special Publication 800-171 'Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations' to provide recommended requirements for protecting the confidentiality of CUI.
Federal agencies should use these requirements when establishing contracts and agreements with non federal entities that process, store, or transmit CUI. This dashboard helps organizations align with NIST 800-171 recommendations.
Tenable provides several solutions for organizations to better understand vulnerability management. Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable Vulnerability Management (formerly Tenable.io) discovers and analyzes assets continuously to provide an accurate and unified view of an organization's security posture. The requirements for this dashboard are: Tenable Vulnerability Management.
Widgets:
- Framework Result Summary: This widget provides compliance results (Passed, Warning, Error, Failed) results for NIST 800-171.
- Control Summary: This widget provides compliance results for each control family within the compliance standard.
- Audit Check Type Summary: This chapter provides compliance results for hosts within the compliance standard.
- 3. 1 ACCESS CONTROL: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 3. 2 AWARENESS AND TRAINING: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 3. 3 AUDIT AND ACCOUNTABILITY: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 3. 4 CONFIGURATION MANAGEMENT: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 3. 5 IDENTIFICATION AND AUTHENTICATION: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 3. 6 INCIDENT RESPONSE: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 3. 7 MAINTENANCE: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 3. 8 MEDIA PROTECTION: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 3.11 RISK ASSESSMENT: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 3.12 SECURITY ASSESSMENT: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 3.13 SYSTEM AND COMMUNICATIONS PROTECTION: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.
- 3.14 SYSTEM AND INFORMATION INTEGRITY: This widget provides details on each of the compliance controls for the compliance family group being referenced. The compliance control reference number is followed by a count, and compliance result for the compliance control.