Cybersecurity Snapshot: 6 Things That Matter Right Now

Topics that are top of mind for the week ending Sept. 23 | A digital trust disconnect between theory and practice | Don’t ignore attack surface management | An SBOM 101 | Report finds hackers targeting small businesses | And much more!
1 – For digital trust, organizations talk the talk but don’t walk the walk
A global survey shows a disconnect between what businesses say and what they actually do regarding digital trust.
For its “State of Digital Trust 2022” report, IT governance professional association ISACA polled 2,755 business and IT professionals about their policies, practices and beliefs for digital trust, which it defines as “the confidence in the integrity of relationships, interactions and transactions among providers and consumers within an associated digital ecosystem.”
Among the findings were:
- Almost all respondents (98%) acknowledge that digital trust is important but only 12% have a dedicated staffer in this role.
- Only 50% said there’s sufficient collaboration at their organization among security, data integrity and privacy professionals – digital trust’s most important roles.
- Eighty-two percent of respondents say digital trust will grow in importance in the next five years, but only 29% provide digital trust training to staff.
- Only 66% say their organization sufficiently prioritizes digital trust.
- Just 23% say their organization measures the maturity of its digital trust practices.
There’s also strong awareness among those polled about the downsides of weak digital trust, including reputational harm (cited by 62% of respondents), more privacy breaches (60%), increased cybersecurity incidents (59%) and customer loss (56%.)

(Source: ISACA’s “State of Digital Trust 2022” North America infographic, Sept. 2022)
Among the obstacles that prevent organizations from boosting digital trust are lack of skills and training and misalignment with business goals. It also doesn’t help if leadership support for digital trust initiatives is weak, and if financial and technological resources are insufficient.
Some of ISACA’s recommendations for beefing up digital trust include:
- Understand how digital trust can contribute to the organization’s goals, measure the current state and compare it against industry best practices.
- Outline digital trust goals, identify priorities and develop a road map.
- Establish a mindset of continuous improvement in areas such as cybersecurity, quality, reliability, compliance and customer experience.
For more information:
- Read the full report
- Read the blog from ISACA’s CEO and the press release
- View infographics tailored for different regions
2 – Towards a secure Open RAN for 5G services
With the advent of 5G, mobile network operators see a benefit in moving away from traditional, proprietary radio-access networks (RANs) and towards open RANs that can provide them with more flexibility and reliability.
To help operators ensure the security of open RANS, the Cybersecurity and Infrastructure Security Agency (CISA) and the National Institute of Standards and Technology (NIST) just published the guide “Open Radio Access Network Security Considerations.”

CISA Acting Assistant Director Mona Harrington said in a statement that open RAN is “an exciting concept” that could boost innovation, network performance and competition. “However, with those benefits come the potential for additional security concerns,” she said.
For more information:
- “Top 5 security risks of Open RAN” (CSO)
- “How Open RAN Can Bring Security Advantages” (Open RAN Policy Coalition)
- “Open RAN so easy to hack it's 'scary,' says top security boffin” (Light Reading)
- “Private networks gradually get to know open RAN” (FierceWireless)
- “NSA and CISA Publish Open RAN Adoption and Cybersecurity Assessment” (MeriTalk)
3 – Analyst: “Ignore attack surface management at your own peril”
Attack surface growth has accelerated, thanks to remote work, distributed computing, API usage, IoT deployments, cloud adoption and shadow IT – in short, anything that increases an organization’s internet-facing assets.
In a recent column, Enterprise Strategy Group (ESG) analyst Jon Oltsik cited results from an ESG survey of 376 security pros who reported these effects of an expanded attack surface:
- Collaboration and communication between the software development and security teams must be tightened as organizations develop more cloud-native apps and release software continuously.
- Existing security tools and processes need to be re-evaluated as organizations seek to discover and manage attack surface assets. According to the survey, trying to manually collate and analyze data from disparate systems doesn’t work:
- 43% of respondents said it takes them 80-plus hours to do a full attack surface management inventory
- 69% said they suffered a security incident due to an unknown, unmanaged or mismanaged attack surface asset
- Be prepared to manage more vulnerabilities and deploy more patches.
- Anticipate an increase in blind spots.
For more information:
- “Finally Finding the 'Unknown Unknowns' Across Your Entire Attack Surface” (Tenable)
- “What is attack surface management and why is it necessary?” (TechTarget)
- “The Right Way to do Attack Surface Mapping” (Tenable)
- “Look for attack surface management to go mainstream in 2022” (CSO)
- “How to implement an attack surface management program” (TechTarget)
4 – Cyber insurer: Hackers hit small businesses hard; ransomware attacks drop
Cyber insurance provider Coalition has released its mid-year report, based on an analysis of claims from 160,000 of its policyholders, and salient findings include:
- Small businesses – those with annual revenue below $25 million – reported a claim cost average of $139,000, up from $88,000 in the first half of 2021, which highlights their increased vulnerability to cyberattacks.
- Phishing ranked first among primary triggers for cyber incidents, accounting for 58% of reported claims – up 41% in the first half of 2021 – and putting the spotlight on employee vulnerability to this form of email social-engineering attack.
- Regarding ransomware incidents specifically, there was a drop in the average cost of claims; the frequency of claims; the median ransom payment; and the average ransom demand, all compared to the first half of 2021. Coalition attributes this trend to factors such as:
- Companies with security controls such as offline data backups may refuse to pay ransoms because they can restore operations.
- Large organizations in particular are increasingly unwilling to enter into ransom negotiations.
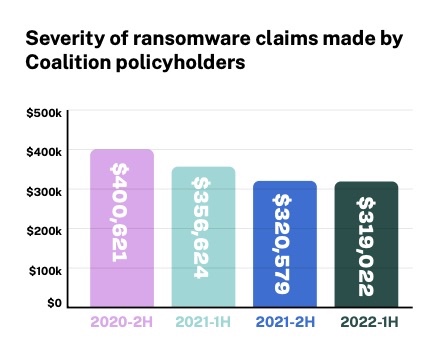
(Source: Coalition’s “2022 Cyber Claims Report Mid-year Update,” Sept. 2022)
For more information:
- “Ransomware is (slightly) on the decline, cyberinsurance company says” (CSO)
- “Cyber Insurance Premium Hikes to Support Returns Amid Rising Claims” (Fitch Ratings)
- “Cyber-Insurance Firms Limit Payouts, Risk Obsolescence” (Dark Reading)
- “Cyber insurance needs an industry-wide security standard” (Security Magazine)
- “Advice from an expert on cyber insurance coverage” (Journal of Accountancy)
5 – An SBOM primer, with a “how to” for developing a program
Global management consulting firm McKinsey & Co. has published a clear and comprehensive overview about the basics of software bills of materials (SBOMs), which are very much in the spotlight as a key element of software supply chain security.
In the piece, titled “Software bill of materials: Managing software cybersecurity risks,” the authors define the SBOM, explain its benefits and include the following recommendations for developing a program:
- Use existing software composition analysis (SCA) tools as a foundation and either buy or develop in house the other necessary tools, ensuring they fit smoothly with software development lifecycle processes (SDLC).
- Ensure that a cross-functional team is involved with the SBOM program, including participants from software development, security, procurement, legal, risk, privacy and compliance.
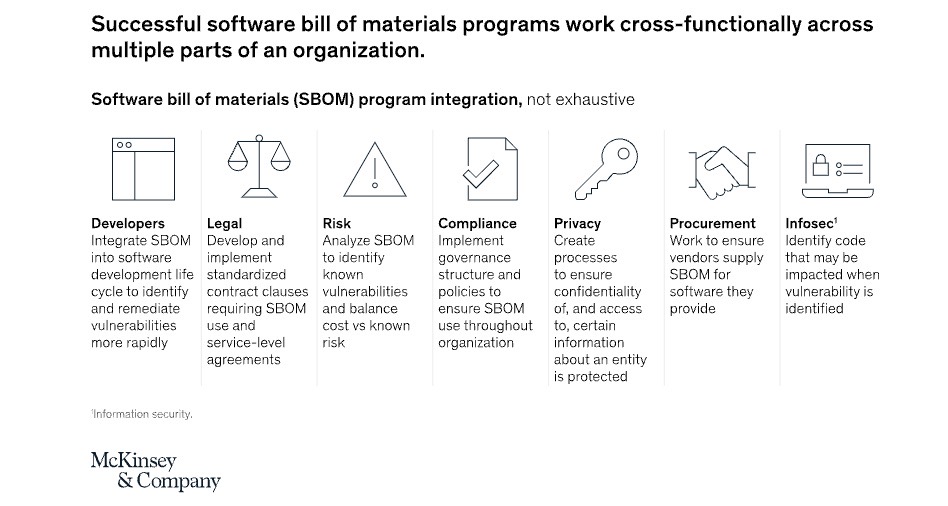
(Source: “Software bill of materials: Managing software cybersecurity risks,” McKinsey & Co., Sept. 2022)
- Build automated SBOM generation and review capabilities throughout the SDLC.
- Create a governance structure for SBOM-related tasks.
For more information:
- “The State of Software Bill of Materials (SBOM) and Cybersecurity Readiness” (Linux Foundation)
- “The Minimum Elements For a Software Bill of Materials (SBOM)” (U.S. National Telecommunications and Information Administration)
- “Securing the Software Supply Chain: Recommended Practices for Developers” (U.S. National Security Agency)
- “Software Bill of Materials (SBOM) Pros & Cons” (Enterprise Networking Planet)
- “The White House wants new transparency into software components” (Protocol)
6 – Cloud visibility still, er, cloudy?
Visibility into cloud assets remains a challenge for quite a few security teams out there, as an ad-hoc poll we conducted at a recent Tenable webinar shows.
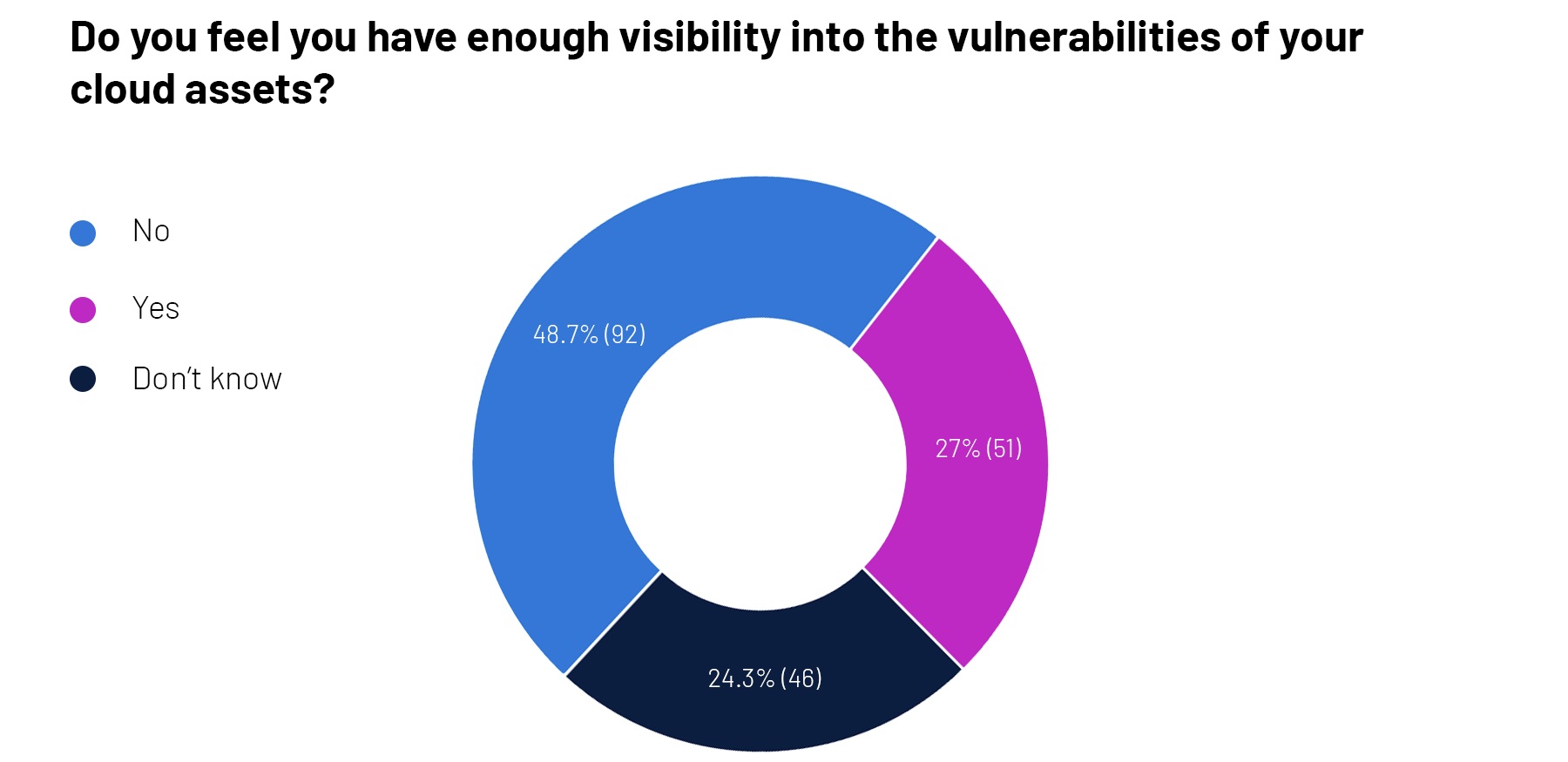
Interested in learning more about this topic? Check out these Tenable resources:
- “Full IT Visibility Requires Business Risk Context” (blog)
- “You’ve Migrated Business-Critical Functions to the Cloud…Now What?” (blog)
- "Extend Vulnerability Management from Code to Cloud" (eBook)
- “Cloud Security Roundtable: Scaling Cloud Adoption without Sacrificing Security Standards” (On-demand webinar)
- “4 Steps to Achieving Comprehensive Kubernetes Security” (white paper)
- “DevOps Guide to Terraform Security” (white paper)
- Attack Surface Management
- Cloud
- Cybersecurity Snapshot
- Mobile Security
- Phishing
