by Carole Fennelly
August 23, 2023
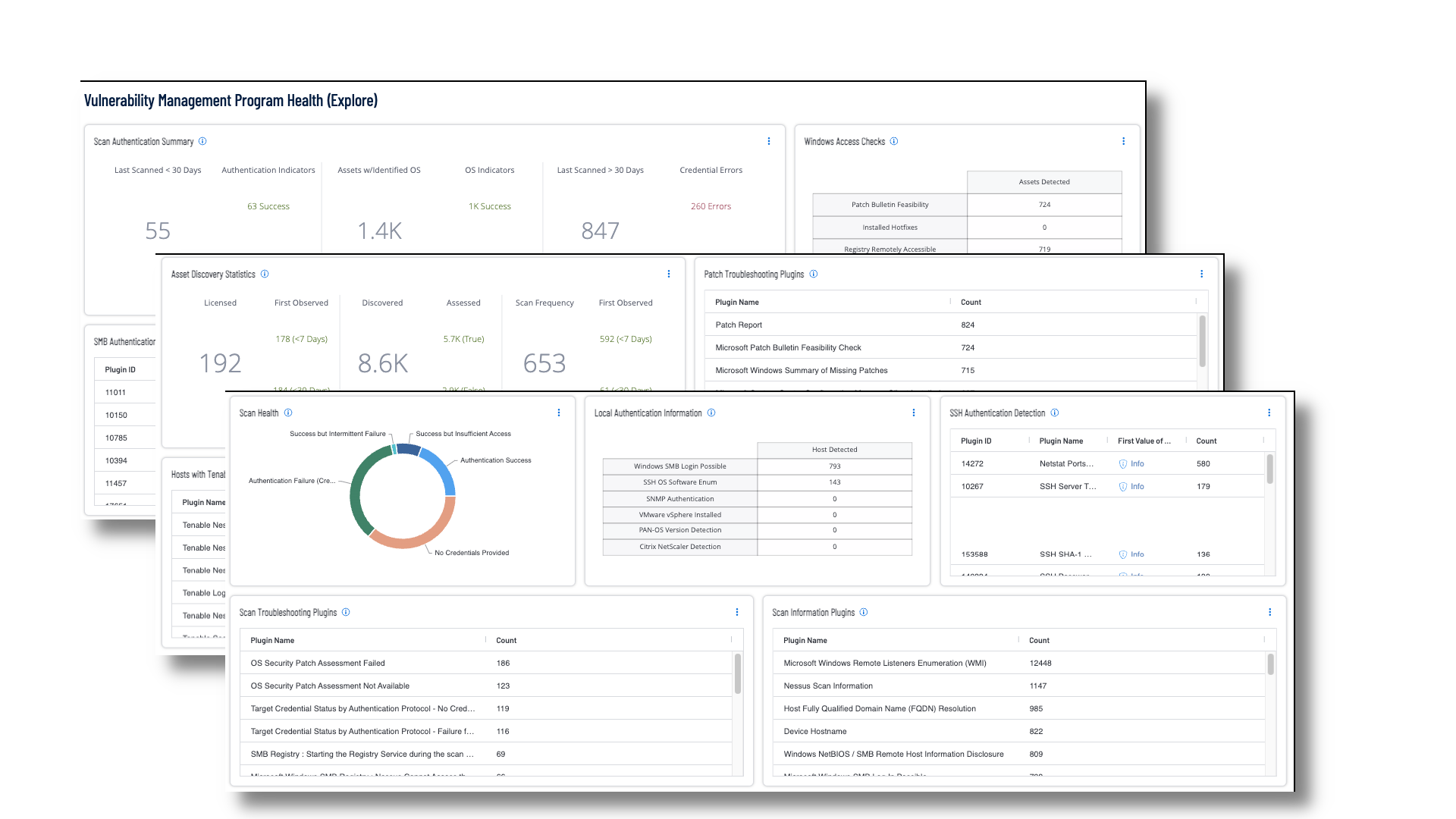
Security operations teams need to ensure their scanning program is appropriately maintained for an evolving operational technology landscape aligned with business strategy. There are many factors that can adversely affect the scope and accuracy of scan data, such as failed credentials, network problems or license limitations. This dashboard provides security analysts comprehensive information to monitor the health of their scanning program.
Credentialed or agent scanning with privileged access provides the most comprehensive and accurate scanning results. Credentialed scans originate from a Tenable Nessus scanner that reaches out to the hosts targeted for scanning, while agent scans run on hosts regardless of network location or connectivity and then report the results back to the manager. Credentialed scanning is more complicated than agent scanning and requires authentication with sufficient privileges to enumerate software, installed applications, patch status, and identify configuration problems. Tenable uses multiple protocols, such as SMB, SSH, HTTPS, and SNMP, to conduct authenticated scans against assets. Analysts can drill into the summary information displayed in the dashboard to troubleshoot upstream scanning problems that can adversely impact downstream reporting to stakeholders.
The Tenable licensed asset limit determines the number of assets that can be scanned for vulnerabilities. Comparing this finding to the number of discovered assets in the environment can help analysts determine if the scanning scope is too narrow. Very often critical business assets are added to the environment without the knowledge of the security or IT teams. Drilling into the data for assets that are discovered but not scanned can reveal assets with a high criticality rating that are not being scanned.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable Vulnerability Management discovers and analyzes assets continuously to provide an accurate and unified view of an organization's security posture. The requirement for this dashboard is: Tenable Vulnerability Management (Nessus, NNM).
Widgets
Scan Authentication Summary – This widget provides a summary of scan health in relation to authentication success and failures. System and network devices must be routinely scanned to ensure they are operating in compliance with organizational and regulatory requirements for vulnerability and configuration management. Evidence of scanning activities is often required by regulatory frameworks and Service Level Agreements (SLAs). Credentialed scanning, which requires authentication to the device, provides the most accurate scanning results. The widget is divided into 3 sections: The Last Scanned within 30 days section displays counts of successful or failed authentications. The Assets with identified Operating Systems section displays counts of successful and failed operating system identification. The Last Scanned older than 30 days section displays counts credential errors. The requirements for this widget are: Tenable Vulnerability Management (Nessus, NNM).
Windows Access Checks – This widget provides an indication of the scan health of Windows systems. The plugins used in the matrix report on the tests Nessus requires to perform the detailed checks on systems. These plugins check for permission and access to various aspects of Windows and set required entries that enable Nessus to perform local checks. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
SMB Authentication Detection – This widget provides a summary view of all the informational SMB plugins, which are used to determine the success of Windows asset scans. SMB is the primary protocol used when scanning a Windows device. There are several plugins that use SMB to report on software installation, BIOS enumeration, and many more core attributes. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Summarize Local Checks Status – This widget provides summaries of local checks status. These local check plugins provide a list of the issues Nessus detects when running a scan. The errors are logged along with the reporting plugin and protocol, if available. The plugins also provide summaries of particular types of authentication local check problems that have been reported by other plugins and report the plugins that encountered these issues. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Authentication Searches – This widget provides a series of useful queries to help troubleshoot authentication problems. Tenable.io uses multiple protocols, such as SMB, SSH, HTTPS, and SNMP, to conduct authenticated scans against assets. Each of the plugins could be triggered on each protocol used during the scan, so an asset can have an authentication success and authentication failure. Use these queries as a first step in troubleshooting scan success and the overall health of vulnerability collection activities. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Scan Health – This widget provides a summary of scan health in relation to authentication success and failures. System and network devices must be routinely scanned to ensure they are operating in compliance with organizational and regulatory requirements for vulnerability and configuration management. Evidence of scanning activities is often required by regulatory frameworks and Service Level Agreements (SLAs). Credentialed scanning, which requires authentication to the device, provides the most accurate scanning results. The five columns display asset counts related to: Authentication Success - Scans authenticate successfully with full administrator/root privileges. Scan results will be the most comprehensive. Success but Insufficient Access - Scans authenticate successfully, but do not have privileged access. Scan results will be limited to what a local non-privileged user could see. Success but Intermittent Failure - Scan credentials intermittently fail, which could be caused by session rate limits, session concurrency limits, or other issues preventing consistent authentication success. Authentication Failure (Credentials) - The credentials provided were incorrect. No Credentials Provided - No credentials were provided. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Local Authentication Information – This widget brings focus to the plugins used to authenticate to a remote host, gathers the information necessary for local checks, and enables local checks. Information enumerated includes Windows SMB Login Possible, SSH OS Software Enumeration, SNMP Authentication, VMware vSphere Installed, PAN-OS Version Detection, and Citrix NetScaler Detection. The output and audit trails provide details of any problems that may have occurred during the scan. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
SSH Authentication Detection – This widget provides a summary view of all the Secure Shell (SSH) plugins, which are used to determine the success of Linux or network device Asset Scanning. Results are sorted by count for each respective SSH plugin. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Scan Troubleshooting Plugins – This widget assists in finding upstream scanning problems or symptoms that point to upstream scanning problems - especially with credentialed/authenticated scans.
Scan Information Plugins – This widget provides details on your scans to determine what is working and also to allow you to dig into helpful results such as the 19506 Scan Information plugin, which includes such details as the scan type, duration and whether or not it was able to perform Local Checks (indicated by a Credentialed checks: Yes line item.)
Asset Discovery Statistics – This widget displays statistics for Tenable.io licensed assets that were first observed less than 7 days ago and less than 30 days ago. The Tenable.io licensed asset limit determines the number of assets that can be scanned for vulnerabilities. The first section displays the total number of licensed assets. The middle column displays the total number of newly discovered assets that are not counted against the license. The last column displays the number of licensed assets that were successfully authenticated with credentials and scanned. More license count details can be viewed on the License page in Settings in Tenable.io. The requirements for this widget are: Tenable.io Asset Data from Tenable.io Vulnerability Management, Tenable Web Application Security (WAS), Tenable.cs, Tenable Lumin.
Patch Troubleshooting Plugins – This widget leverages plugins set related to patch auditing/validation as well as to identify issues, such as where an asset needs to be rebooted to apply a patch.
Hosts with Tenable Applications Installed – This widget lists the Windows, Linux and macOS hosts where the most recent scan results confirmed that a Tenable application was installed. When scanning with Agents, verify that all Agents belong to an Agent Group and that the Agent Group has an associated scan job.
Outdated Tenable Sensors and Applications – This widget lists Tenable applications that are out-of-date and need to be updated to keep them secure and operational.