Cybersecurity Snapshot: SEC Wants More Cybersecurity Transparency from Public Companies

Find out what’s in the SEC’s new cybersecurity disclosure rules. Plus, CISA analyzes the cyber risks impacting critical infrastructure organizations. Also, check out guidance for shadow IT and tips to boost your security awareness program. And much more!
Dive into six things that are top of mind for the week ending July 28.
1 – SEC issues cybersecurity disclosure rules
This week, the U.S. Securities and Exchange Commission adopted new rules requiring publicly traded companies to disclose material information about their cybersecurity incidents, risk management, strategy and governance.
The goal is to make cybersecurity disclosures more consistent, comparable and useful for decision-making, which will benefit companies, their investors and the markets, the agency said in a statement.
“Whether a company loses a factory in a fire – or millions of files in a cybersecurity incident – it may be material to investors,” SEC Chair Gary Gensler said.

Some of the rules’ specifics include:
- Companies will have to disclose any cyber incident they deem to be material, and describe its nature, scope and timing, as well as its actual or potential impact on the business. The disclosure will be due four business days after a company determines an incident is material.
- Annually, companies will have to detail how they assess, identify and manage material risks from cyberthreats, and state what actual or potential effects these risks from cyberthreats or from previous cyber incidents could have on their business.
- Companies will also have to describe their boards’ oversight over cyber risks, as well as management’s “role and expertise in assessing and managing material risks from cybersecurity threats.”
The new rules go into effect 30 days after they’re published on the Federal Register.
“For a long time, the largest and most powerful U.S. companies have treated cybersecurity as a nice-to-have, not a must have. Now, it’s abundantly clear that corporate leaders must elevate cybersecurity within their organizations,” Tenable Chairman and CEO Amit Yoran told the Associated Press. He shared more of his thoughts in this LinkedIn post.
To get more details, check out this FAQ by Tenable Chief Legal Officer and General Counsel Michelle VonderHaar and Tenable VP and Deputy General Counsel David Bartholomew, as well as coverage from The Verge, Dark Reading, Help Net Security, CRN and CNBC.
2 – CISA analyzes critical infrastructure risks and vulnerabilities
Are you tasked with protecting critical infrastructure? If so, you’ll want to check out a post-mortem on the main cyber risks and vulnerabilities that impacted critical infrastructure operators and facilities in fiscal year 2022.
In an 18-page analysis published this week, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) outlined findings from 121 risk and vulnerability assessments (RVAs) conducted throughout multiple critical infrastructure sectors.

Key highlights from the analysis include:
- Common methods, such as phishing and using default credentials, were the preferred vehicle for hackers to launch successful attacks
- Attackers used a constantly changing assortment of tools and techniques
- The same vulnerabilities were observed across many critical infrastructure organizations
The document includes a sample attack path that illustrates the steps and tactics an attacker would employ, based on the weaknesses identified in the RVAs, which loosely map to 11 of the 14 tactics in the MITRE ATT&CK framework cyber actors can use to access a network or system.
To get all the details, check out CISA’s announcement, the full document and a set of accompanying infographics.
For more information about protecting critical infrastructure from cyber threats, check out these Tenable blogs:
- “CVE-2023-3595, CVE-2023-3596: Rockwell Automation ControlLogix Vulnerabilities Disclosed”
- “OT Maritime Security: Stormy Waters or Smooth Sailing Ahead?”
- “CISA program helps critical infrastructure orgs fend off ransomware attackers”
- “7 Regulatory and Compliance Frameworks with Broad Cloud Security Implications”
- “ETHOS: Bringing the OT Security Community Together for Threat Information Sharing”
3 – U.K. cyber agency shines lights on shadow IT
Shadow IT, those apps, devices, cloud services and other assets employees use without notifying — nor getting authorization from — the IT and security teams represent a major and continued risk to organizations. This week, The U.K. National Cyber Security Centre announced it has updated its guidance on shadow IT, and the recommendations are worth a look.

“The guidance helps system owners and technical staff to better mitigate the presence of unknown (and therefore unmanaged) IT assets within their organisation,” reads a blog announcing the guidance updates.
Here are some key takeaways:
- Chances are your organization has shadow IT, so focus on organization mitigations, such as having a simple process for fielding users’ requests for assets they want to use
- Recognize most instances of shadow IT aren’t motivated by malicious purposes, but rather by employees wanting to get tasks completed
- Implement technical solutions, such as asset management and network access controls
- As you discover shadow IT assets, try to learn what user needs prompted employees to adopt them
- Don’t reprimand employees for using shadow IT, but rather focus on educating them about security, so that the lines of communication remain open
To get all the details, read the updated guidance.
For more information about shadow IT security:
- “Policies for SaaS Apps, Shadow IT Prove Difficult to Manage” (ITPro Today)
- “The New Shadow IT – The Importance of Having Visibility Into Your SAAS Usage” (CPO Magazine)
- “Shadow IT is increasing and so are the associated security risks” (CSO Online)
- “The shadow IT fight — 2023 style” (Computerworld)
4 – SANS publishes 2023 report on security awareness
Looking for the latest trends and best practices to boost your security awareness program? Check out the “2023 SANS Security Awareness Report,” released this week. Now in its eighth year, the free report is based on a global survey of almost 2,000 security awareness pros.
Leveraging the survey data, the report provides “findings and data-driven action items you can use to mature your security program and increase your cybersecurity team’s skills and confidence,” reads a SANS blog about this year’s edition.
Key findings and recommendation include:
- Using the “SANS Security Awareness Maturity Model,” make an annual assessment of your security awareness program
- The top factor for program maturity is the number of full-time employees on the security awareness program, because people are needed to manage human risk
- To increase your program’s headcount, highlight the value and cost savings it generates, not how many training sessions it conducts
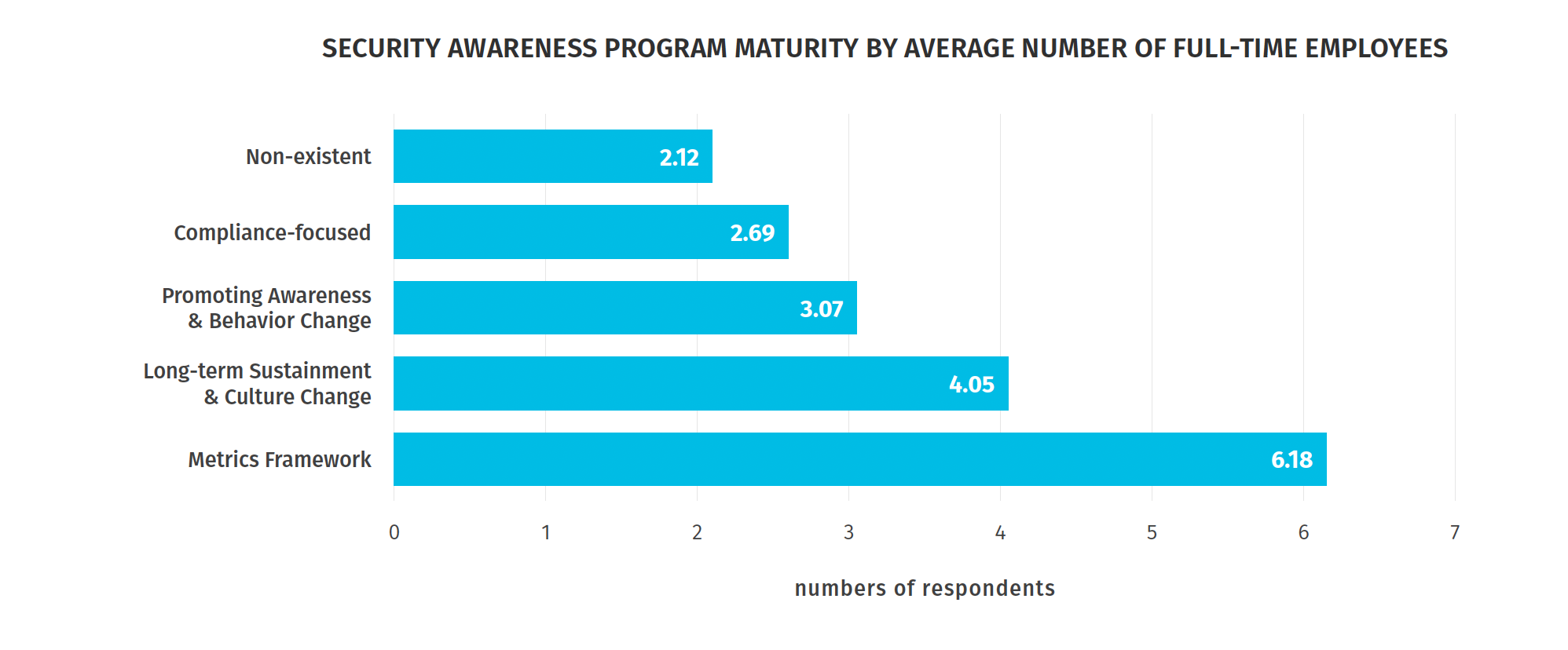
(Source: SANS Institute’s “2023 SANS Security Awareness Report,” July 2023.)
- Respondents overwhelmingly identified social engineering attacks as their organization’s top human cyber risk
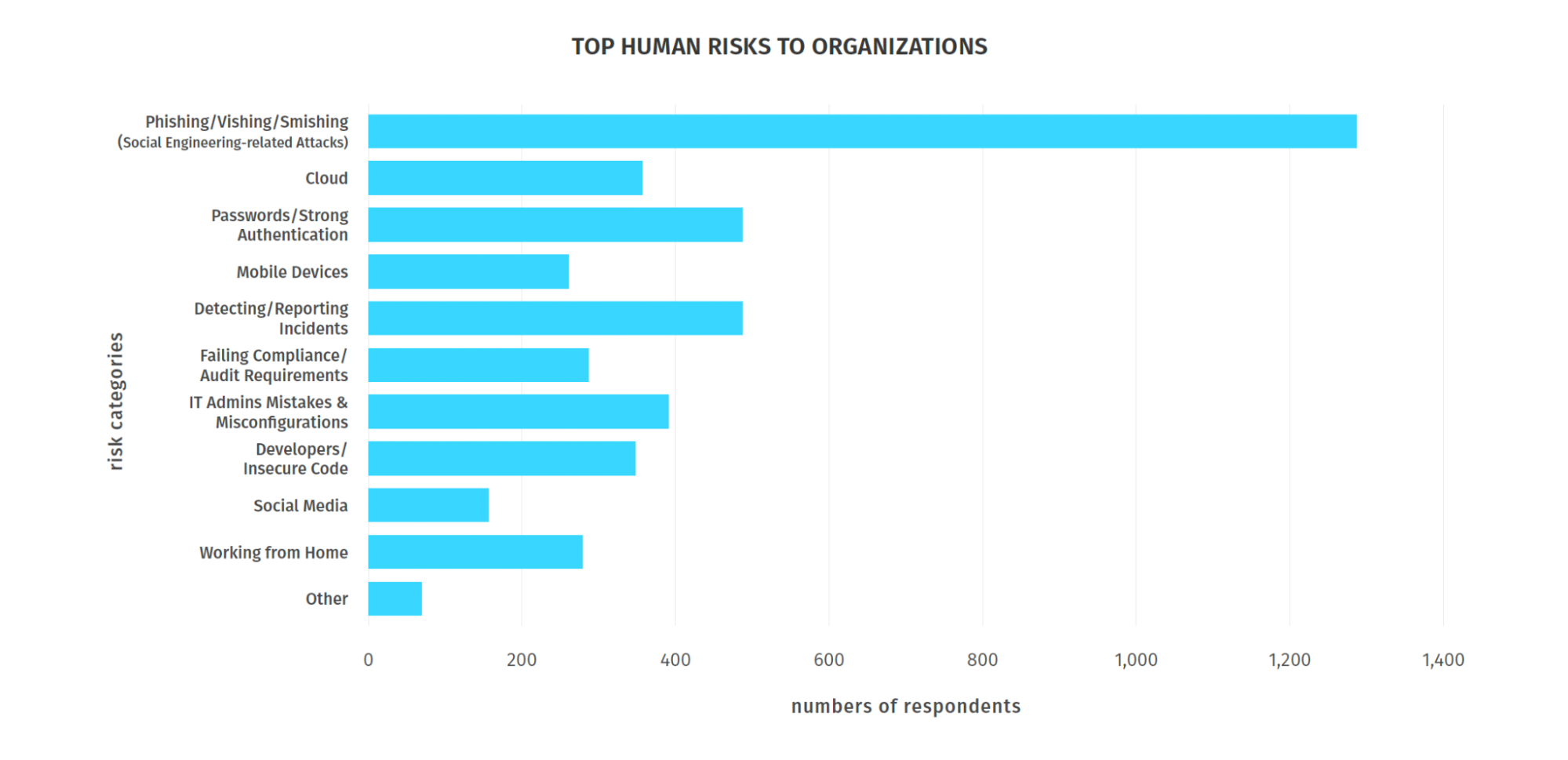
(Source: SANS Institute’s “2023 SANS Security Awareness Report,” July 2023.)
To get more details, download the report.
5 – NCC Group: Ransomware attacks on the upswing
Ransomware attacks spiked in June, climbing a whopping 221% year-on-year, an increase driven in part by the CL0P ransomware gang’s exploitation of vulnerabilities in Progress Software’s MOVEit Transfer product.
So said the NCC Group’s Global Threat Intelligence team in its “Monthly Theat Pulse” report for June. CL0P attacks made up 21% of ransomware attacks in June, followed by LockBit 3.0 (14%) and newcomer 8base (9%).

“The considerable spike in ransomware activity so far this year is a clear indicator of the evolving nature of the threat landscape,” Matt Hull, Global Head of Threat Intelligence at NCC Group, said in the report.
“It’s imperative that organisations should remain vigilant and adapt their security measures to stay one step ahead,” he added.
To get all the details, read the full report.
For more information about ransomware protection:
- “FAQ for MOVEit Transfer Vulnerabilities and CL0P Ransomware Gang” (Tenable)
- “7 Steps to Help Prevent & Limit the Impact of Ransomware” (Center for Internet Security)
- “Ransomware Preparedness: Why Organizations Should Plan for Ransomware Attacks Like Disasters” (Tenable)
- “Tips & Tactics: Ransomware” (NIST)
- “Mitigating malware and ransomware attacks” (U.K. NCSC)
VIDEO
Anatomy of a Threat: MOVEIt (Tenable)
6 – White House gets AI vendors to commit to responsible AI
The Biden administration secured voluntary commitments from seven major AI companies to develop their artificial intelligence products safely, securely and transparently to protect people’s rights and safety.
The companies – Amazon, Anthropic, Google, Inflection, Meta, Microsoft and OpenAI – agreed, among other things, to:
- Ensure their AI products are safe before releasing them to the public by, for example, submitting them not only to internal but also to independent, external testing
- Build systems whose priority is to be secure, through measures including investing in cybersecurity and insider threat safeguards and by facilitating third-party discovery of vulnerabilities
- Earn the public’s trust, by, for instance, ensuring people know when content has been generated by AI and prioritizing research on societal risks
This initiative is in addition to the U.S. government’s pursuit of AI guardrails via legislation and regulation.
This week, four of those companies – Google, OpenAI, Microsoft and Anthropic – formed the Frontier Model Forum, an industry group whose aim is ensuring the safe and responsible development of “frontier AI models,” which it defines as “large-scale machine-learning models that exceed the capabilities currently present in the most advanced existing models.”
To get more details, read the White House announcement and the Frontier Model Forum’s announcement.
For more information about responsible AI development and use:
- “What is responsible AI?” (TechTarget)
- “AI Risk Management Framework” (U.S. National Institute of Standards and Technology)
- “Why we need to care about responsible AI in the age of the algorithm” (World Economic Forum)
- “Building Robust RAI Programs as Third-Party AI Tools Proliferate” (MIT Sloan Management Review)
- Cloud
- Cybersecurity Snapshot
- Executive Management
- Federal
- Government
- OT Security
- Public Policy
- Shadow IT


