Cybersecurity Snapshot: 6 Things That Matter Right Now
Key vulnerabilities you can’t ignore. Best practices to improve operational technology (OT) cybersecurity. A reality check on shift left, DevSecOps and cloud security. Tackling the security skills gap. Healthcare data breaches. And much more!
The cybersecurity world is perennially noisy. Security pros must continually process headline-grabbing hacks, vulnerability disclosures, stern regulations and expert recommendations. To do our bit to help, every two weeks we’ll provide this quick at-a-glance view of the cybersecurity landscape, highlighting essential information and emerging trends, anchored by data points and best practices. Read on!
1 -- Five vulnerabilities to absolutely, positively have on your radar
With thousands of vulnerabilities disclosed so far this year, Tenable Senior Research Manager Giuliana Carullo has handpicked these five as ones that you should definitely have pinned on your map.
| CVE | Description |
|---|---|
| CVE-2022-1096 | Google Javascript V8 Chrome Engine Vulnerability |
| CVE-2022-0847 | Dirty Pipe - Linux Kernel Vulnerability |
| CVE-2022-26809 | Zero-click - Microsoft RPC Vulnerability |
| CVE-2022-22965 | Spring4Shell - Spring Core Framework Vulnerability |
| CVE-2022-1388 | F5 BIG-IP Vulnerability |
As she explains in her recent blog “So Many CVEs, So Little Time: Zero In and ‘Zero Click’ into the Current Vulnerability Landscape,” these vulnerabilities, while only the proverbial tip of the iceberg, exemplify the variety of challenges and complexities that a proactive security team must be aware of and prepared for. Read Giuliana’s blog for a deep dive on each one of these important vulnerabilities.
2 -- Forrester: Anywhere work is here to stay, but cyberattacks are a consistent challenge
The recently published Forrester report “The Anywhere-Work Guide For Tech Pros, 2022” states that the “work from anywhere” model has by now become widely adopted, with two-thirds of U.S. firms moving to it. While ripe with benefits both for employers and employees, the model faces a number of challenges, including, unsurprisingly, cybersecurity, as cyberattacks against remote workers have increased. Some salient data points:
- Forrester’s 2021 data shows that 21% of security decision-makers indicated that their organization’s sensitive data was potentially compromised three to five times in the past 12 months, up from 15% who said the same in 2019.
- While actors carry out attacks via multiple methods — software vulnerabilities, phishing, or ransomware — anywhere workers are a common target.
- Factors that make remote workers targets for cyberattacks include a rise in bring-your-own-device (BYOD) policies, lack of home network security, and an increase in socially engineered attacks.
Separately, a recent Forrester Consulting study commissioned by Tenable found that 67% of business-impacting cyberattacks targeted remote workers.
More information:
- Read “Beyond Boundaries: The Future of Cybersecurity in the New World of Work,” a commissioned study conducted by Forrester Consulting on behalf of Tenable
- View the infographic “Beyond Boundaries: Rethinking risk in the new world of work”
- Read the blog “Protecting the Atomized Attack Surface: Cybersecurity in the New World of Work”
- Read the blog “You’ve Migrated Business-Critical Functions to the Cloud…Now What?”
3 -- Having trouble finding cybersecurity pros? You’re not alone
With only about two thirds of U.S. cybersecurity jobs currently staffed, the Cyberspace Solarium Commission 2.0 has just released a report that’s chock-full of recommendations for tackling this issue. Aimed primarily at the federal government — and specifically at the National Cyber Director and the U.S. Congress — it also offer suggestions for private sector employers, specifically:
- Increase their investment in the cyber workforce, especially those starting their careers
- Develop shared resources, such as training programs sponsored by a group of companies, and apprenticeship programs done in collaboration with educational institutions
For more information:
- Read the report: “Workforce Development Agenda for the National Cyber Director”
- Read “Latest Cyberspace Solarium Commission 2.0 Report focuses on cyber workforce” (CSO Magazine)
- Read “Solarium successor wants the White House to lead on cyber workforce strategy” (FCW)
- Read: “700K more cybersecurity workers, but still a talent shortage” (TechBeacon)
- Read: “How Can We Get More Women in Tech — and Support Their Growth?” (Government Technology)
4 -- What’s the state of critical infrastructure security?
A year after the Colonial Pipeline’s ransomware attack shone a blinding spotlight on the cybersecurity risks facing critical infrastructure operators, what can we do to better protect these facilities’ IT and OT systems? Quite a bit, according to Tenable VP of OT Security Marty Edwards, who outlines a number of concrete recommendations for the U.S. government, CISOs, cybersecurity vendors and the public at large in his blog “How Can We Strengthen the Cybersecurity of Critical Infrastructure?”
To dig deeper, check out these resources:
- “The State of OT Security, a Year Since Colonial Pipeline” (blog)
- “The State of OT Security, a Year Since Colonial Pipeline” (podcast)
- “Colonial Pipeline One Year Later: What Have (and Haven’t) We Learned?” (LinkedIn Live)
5 -- Tens of millions impacted by health data hacks
Fifty million. That’s how many people in the U.S. were victims of health data breaches in 2021, a number that has tripled in three years. The finding comes from Politico, which analyzed six years’ worth of data from the U.S. Health and Human Services Department.
The reasons for the spike in breaches?
- Health care organizations’ fast digitization of processes
- The rise in telecommuting and the related increase in employees’ use of personal devices for work, which broadens the attack surface
- The financial attractiveness of health care information for data thieves
- Increased reporting of incidents
Citing the Politico study, U.S. Senators Bill Cassidy, M.D. (R-LA) and Jacky Rosen (D-NV) introduced on March 23 the Healthcare Cybersecurity Act, which they said would direct CISA and the Department of Health and Human Services (HHS) to collaborate on improving cybersecurity in hospitals and other healthcare centers.
Tenable’s “2021 Threat Landscape Retrospective” identified healthcare as the top sector targeted by ransomware groups, with ransomware attacks accounting for almost 25 percent of all breaches in this vertical last year.
More information:
- “Improving the Cybersecurity Posture of Healthcare in 2022” (U.S. Health & Human Services Department)
- “Healthcare Cybersecurity: The Challenges of Protecting Patient Data” (IT Business Edge)
- “A high-level guide for hospital and health system senior leaders” (American Hospital Association)
- “Healthcare Ransomware Attacks Increased by 94% in 2021” (HIPAA Journal)
- “A new approach to healthcare cybersecurity” (Security Magazine)
- “Nurses Are Vital to Maintaining Healthcare Cybersecurity” (HealthTech Magazine)
- “2 million patients’ data exposed in cyberattack on New England health services provider” (Healthcare Dive)
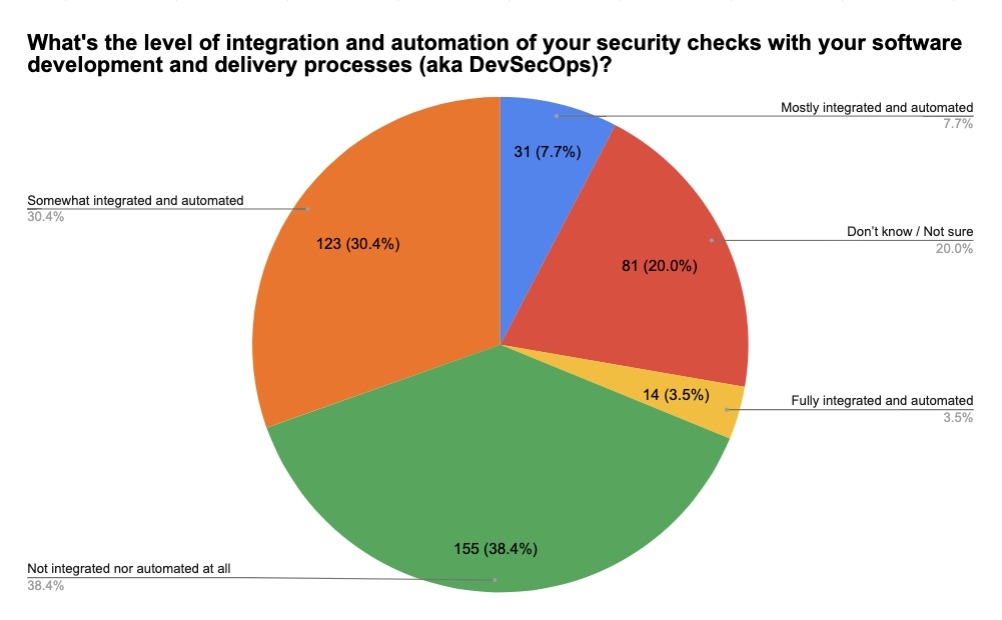
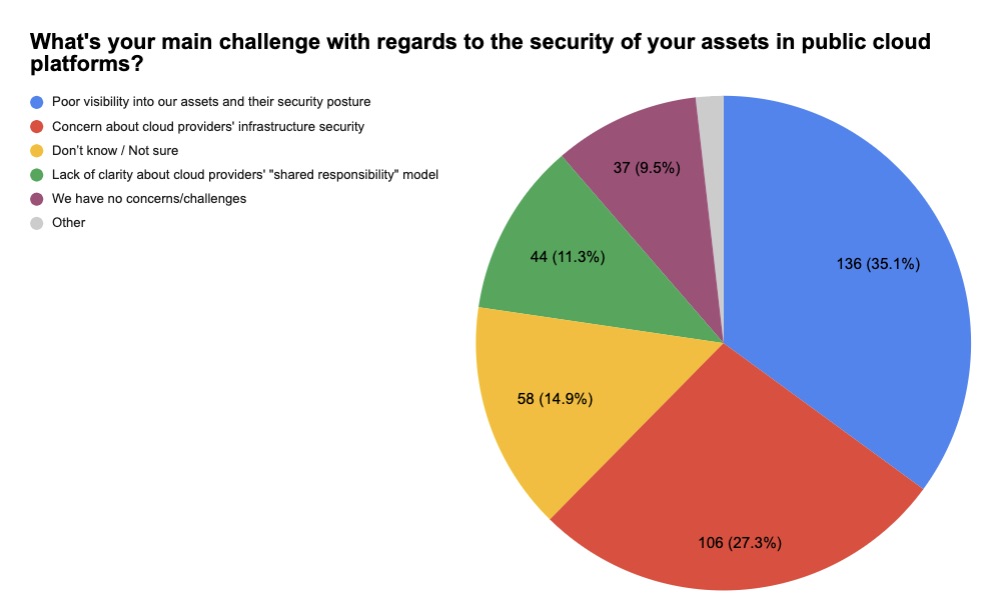
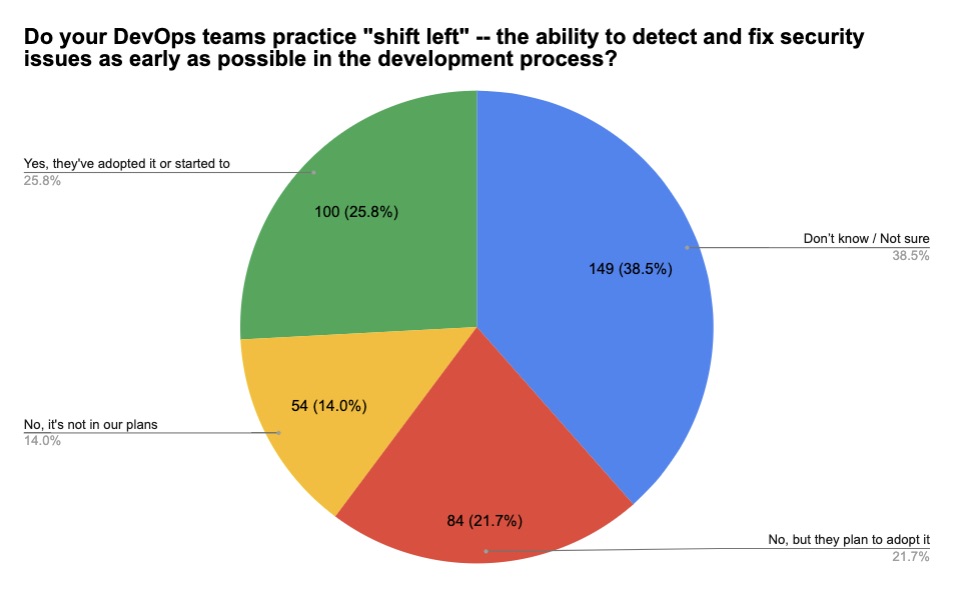
6 -- A reality check on “shift left,” DevSecOps and cloud security
For years we’ve been hearing about the importance of certain cybersecurity practices, particularly:
- “Shift left” to start security checks early in the software development process
- DevSecOps to embed security into DevOps
- Cloud security to properly protect those environments
Curious about how these practices are being adopted in the real world, we polled attendees at several recent Tenable webinars on these topics. While these were admittedly ad-hoc, unscientific polls, we believe the results offer an interesting temperature check on where organizations are at in these three areas. Check it out.
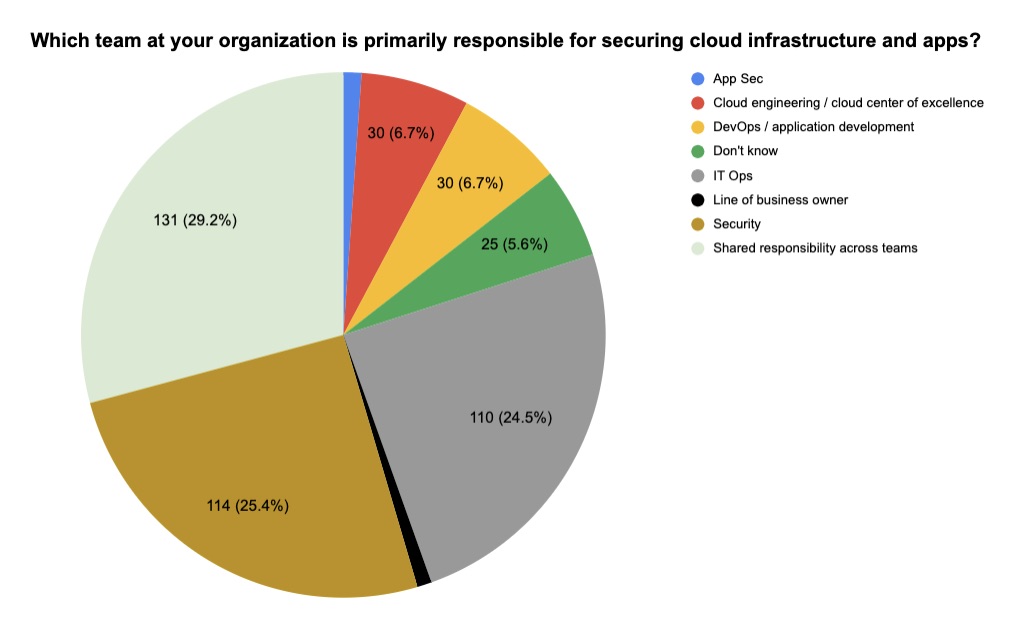
Interested in these topics? You’ll find these recent blogs useful:
- “Mind the (Communication) Gap: How Security Leaders Can Become Dev and Ops Whisperers”
- “A Practical Approach for Shifting Left”
- “3 Ways Security Leaders Can Work With DevOps to Build a Culture of Security”
And check out the on-demand webinar “The Four Phases of Cloud Security Maturity” by Tenable Chief Security Strategist Nathan Wenzler.
- Cloud
- Cybersecurity Snapshot
- OT Security
- Recruiting
- Remote Workforce
- Risk-based Vulnerability Management
- Vulnerability Management


