How Exposure Management Has Helped Tenable Reduce Risk and Align with the Business

Todas as segundas-feiras, a Tenable Exposure Management Academy fornece a orientação prática e real de que você precisa para mudar do gerenciamento de vulnerabilidades para o gerenciamento de exposição. In the second of a two-part blog series, Tenable CSO Robert Huber shares how exposure management has helped him reduce risk and better align with the business. Você pode ler a série completa da Academia de gerenciamento de exposição aqui.
Last week, I explored the critical shift from traditional vulnerability management to a comprehensive exposure management approach. I explored the limitations of siloed security tools and the overwhelming deluge of data that often leaves security teams and business leaders wondering what they can do.
In this post, I’ll dig deeper on the practical application of exposure management, illustrating how, as CSO for Tenable's own information security organization, I have implemented this philosophy internally to drive tangible improvements in risk reduction and business alignment.
My team can tell you not only the revenue associated with a particular product but also the aggregated risk posed to it by various security issues across multiple tools.
It’s all about prioritization
The core challenge for any organization grappling with cybersecurity is prioritization. Imagine a CISO presented with hundreds of tickets across various security domains. If you’re a CISO (or know one), you probably don’t really have to imagine it because it happens every day. You probably see countless alerts about everything from vulnerabilities and misconfigurations to cloud security and beyond.
But without a unified view and a clear understanding of business impact, all that data is useless. You simply can’t take action.
This is where exposure management can be a real help in figuring out the interconnectedness and any potential impact on critical business assets and functions.
At Tenable, we’ve learned this lesson firsthand. Here are some of the ways we use exposure management in our own security practices:
- Tenable’s security team tags extensively to contextualize assets. This enables us to understand which assets belong to specific business units, product lines or even revenue-generating streams. The granularity transforms raw security data into actionable business intelligence.
- Internally, my team can tell you not only the revenue associated with a particular product but also the aggregated risk posed to it by various security issues across multiple tools.
- We use a visualization of how security used to look. I call it the "spaghetti chart" (see below) because that’s what it looks like, with a chaotic array of inputs from every corner of the enterprise, each with unique workflows. The only thing it’s missing is a side salad. As startling as the image is, it represents real life for those of us in cybersecurity, including everything from endpoint detection and response (EDR) vendors and bug bounty programs to vulnerability management scans, SOC findings and penetration test results.
Before: Each constituent needed specific tools
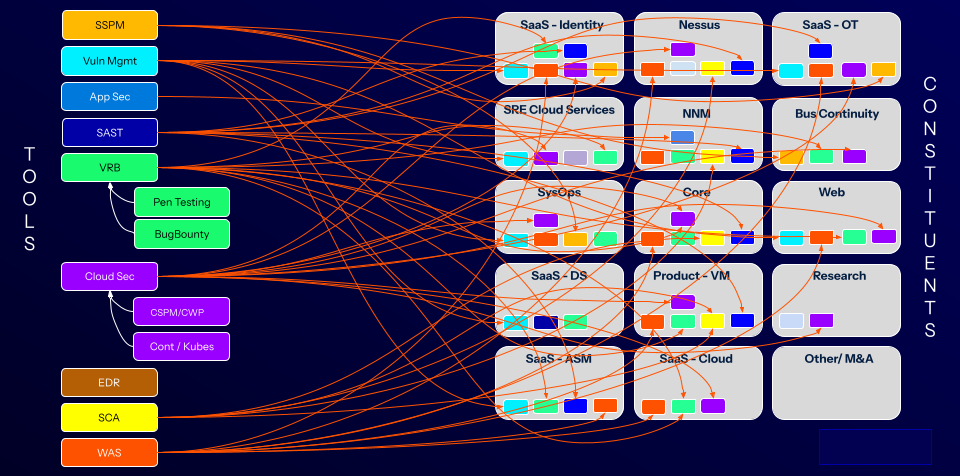
Fonte: Tenable, 2025
Next, you can see the after picture. It just eases the mind looking at it. It’s order, not chaos; calming, not frightening. That’s because an exposure management platform doesn't just collect this security data. Nope. It does a lot more. It normalizes, deduplicates and integrates every bit and byte.
After: Order from chaos
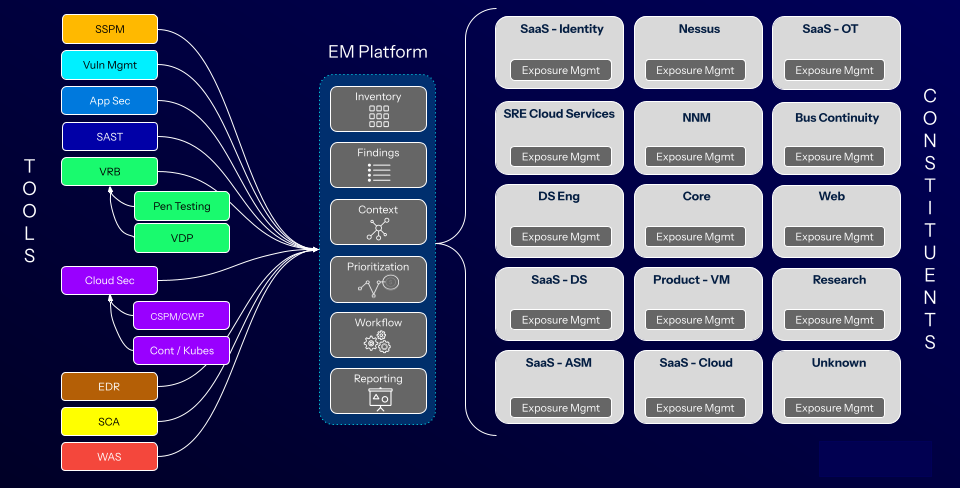
Fonte: Tenable, 2025
Although I work for Tenable, I want to emphasize a point: I’m not talking solely about our solutions. Internally, we pull in data from about 50 different inputs to determine the Red, Yellow, Green status of an asset.
Although I work for Tenable, I want to emphasize a point: I'm not talking solely about our solutions. Internally, we pull in data from about 50 different inputs to determine the Red, Yellow, Green status of an asset. We then feed this centralized data into a powerful prioritization engine. Although most organizations still prioritize within their individual silos (e.g., a vulnerability management team using Tenable Vulnerability Priority Rating [VPR] or asset criticality rating specifically for their platform), we extend this prioritization logic across all capabilities within our exposure management platform. This is a significant leap beyond simply using common vulnerability scoring system (CVSS) scores, which, without temporal inputs or business context, offer no real way to prioritize.
More than a name change
Our overarching goal using exposure management in our internal security practices is to shrink the tool sprawl problem or the resulting data overload and fragmented reporting. By proactively taking in more data and performing better prioritization, we significantly reduce the number of reactive incidents. As security professionals, we know incidents will never go to zero, but a robust exposure management strategy helps us minimize the "firefighting" and shift resources towards more strategic, proactive security initiatives.
A key internal evolution at Tenable has been the transformation of our vulnerability management policy into an exposure management policy. More than just a name change, it represents a fundamental shift in scope for our vulnerability management team, which transformed into the exposure management team. That team manages and owns the collaboration and workflows with the lines of business teams that need to fix issues. Alongside that, our exposure management policy now encompasses all inputs that produce stateful information from every security tool. We’re talking misconfigurations, vulnerabilities, weaknesses and more.
This comprehensive approach, which might overwhelm you because of the sheer volume of data, is made manageable by the Tenable One Exposure Management Platform's ability to handle data deduplication, normalization and centralized reporting. But I think the most important things the platform does are automated prioritization and workflows that meet the users where they are, no matter their workflow. This frees our security teams from the manual burden of these tasks so they can focus on in-depth analysis and asking the right questions.
Our internal journey has also redefined the roles of our security teams. Specialized teams like cloud security and application security still exist, but their focus has shifted. Instead of chasing down colleagues to fix specific issues, they can now concentrate on their core business functions, like securely deploying infrastructure in new environments. I knew we needed to unify policy and data reporting, so the redefined exposure management team handles the legwork of tracking SLAs and ensuring remediation, a process that is largely automated within the platform. This saves significant time and enables us to efficiently scale security resources.
Bob’s simple metrics
The manifestation of this internal journey within our own Tenable One platform is evident in what’s become known as "Bob's simple metrics" — the Red, Yellow, Green I mentioned earlier. This direct visualization helps bridge the gap between technical security findings and business understanding. We can also set target SLAs, customizable by region or other tags, so teams can track their performance against these targets and make data-driven adjustments.
A significant area of focus for us is the automated identification of what I call "big rocks" or the underlying reasons for security posture deviations.
For example, if we can’t patch a system running Amazon Linux 2 with ContainerD because of system instability, the platform should ideally flag this systemic issue rather than just listing individual vulnerabilities. This level of insight helps us present a clear picture to leadership, highlighting the root causes of risk and enabling strategic decisions on how to address them.
Acquiring and deploying Vulcan
The recent acquisition of Vulcan Cyber, and the integration into Tenable One, has been instrumental in furthering our exposure management capabilities. As I mentioned, Tenable's internal security relies on data from a lot of different inputs, only a handful of which are Tenable solutions. The ability to ingest and integrate third-party data (including manual inputs like PDF pen test results or bug bounty reports) was a critical requirement for us. We can now centralize and prioritize data from a vast array of sources, providing a truly holistic view of risk.
The internal deployment of this capability was remarkably swift: We integrated 15 different third-party feeds within 48 hours and we built most of our custom reporting in the 24 hours after that. This rapid integration and automation drastically reduced manual report creation and prioritization. It delivered immense value.
This doesn’t just benefit those of us at Tenable. The integration of Vulcan into the Tenable One platform, as Tenable Connectors, is now rolling out in phases to customers, currently supporting 300 third-party integrations, which will further enhance their exposure management capabilities.
The aim of exposure management is to change the conversation with stakeholders.
Instead of presenting overwhelming reports of unaddressed issues, we can now provide a clear process, workflow and data-driven expectations. Planning will be easier and business leaders will be able to ask that crucial question: "What do you want me to do?" Only now they’ll receive a concise, prioritized list of actions that genuinely reduce risk.
conclusões
Our internal experience with exposure management has been a no BS journey. We’re working through this internally and it’s evolving how we operate.
Some regulations and industry requirements are very specific about vulnerability management policies and CVSS usage, so we do face a few challenges. Nonetheless, we are actively working to shift the conversation from mere SLA compliance to a comprehensive risk reduction approach. You're never going to fix everything and you'll miss some SLAs. But are you effectively managing risk? That’s the critical question.
The board reporting I discussed in the first part of this series, How Tenable Moved From Siloed Security to Exposure Management, now reflects this shift. We present a clear, Red, Yellow, Green status of our critical areas, with concise notes explaining the transitions. This context is crucial, especially when factors like company acquisitions can temporarily impact security posture. Our goal is to uplevel all our conversations to align with the business, demonstrating the impact of security on revenue, services and overall business objectives.
More than a mere buzzword, exposure management is a necessary evolution of how organizations approach cybersecurity.
Saiba mais
Check out the Tenable exposure management resource center to discover the value of exposure management and explore resources to help you stand up a continuous threat exposure management program.
- Exposure Management
- Exposure Management Academy


