Detecting Bad Rabbit Ransomware

A new ransomware dubbed Bad Rabbit has hit several targets and began spreading across Russia and Eastern Europe on Tuesday, October 24, 2017. The ransomware exploits the same vulnerabilities exploited by the WannaCry and Petya ransomware that wreaked havoc in the past few months. As new versions of ransomware using Shadow Brokers exploits run wild, Tenable.io Vulnerability Management (VM) users are equipped with tools to stay ahead of the game.
What is Bad Rabbit and what does it do?
According to early reports, Bad Rabbit Ransomware uses a fake Flash update to lure unsuspecting users into installing the ransomware, resulting in the encryption of their data. Whether the attackers honor the payment or just keep asking for more money, the best approach is to patch your systems today and avoid the issue altogether.
Identifying Vulnerable Assets
Tenable.io users are ahead of the game. By using active scanning and agent-based scanning, customers will be able to easily identify the vulnerable assets across the exposed attack surface. Existing Petya and WannaCry plugins will display systems that are vulnerable to MS17-010, and these assets should be patched immediately.
Tenable.io™ Vulnerability Management has the following two plugins, released earlier this year, to detect vulnerable systems:
- 97737 - MS17-010: Security Update for Microsoft Windows SMB Server (4013389) (ETERNALBLUE) (ETERNALCHAMPION) (ETERNALROMANCE) (ETERNALSYNERGY) (WannaCry) (EternalRocks) (Petya)
- 97833 - MS17-010: Security Update for Microsoft Windows SMB Server (4013389) (ETERNALBLUE) (ETERNALCHAMPION) (ETERNALROMANCE) (ETERNALSYNERGY) (WannaCry) (EternalRocks) (Petya) (uncredentialed check)
Malware Scanning
By scanning using the Malware plugins such as Malicious Process Detection (59275) and others, you can better detect and eliminate cyber risks across all assets. Other plugins that are useful to enable during scanning are:- Web Site Hosting Malicious Binaries (71024)
- Linux Malicious Process Detection (71261)
- Mac OS X Malicious Process Detection (71263)
- Malicious File Detection (88961)
In the image below, we can see the result of a scan of a system with running processes that are considered malware. These systems should be quarantined and analysed forensically to ensure that compromise has not occurred.
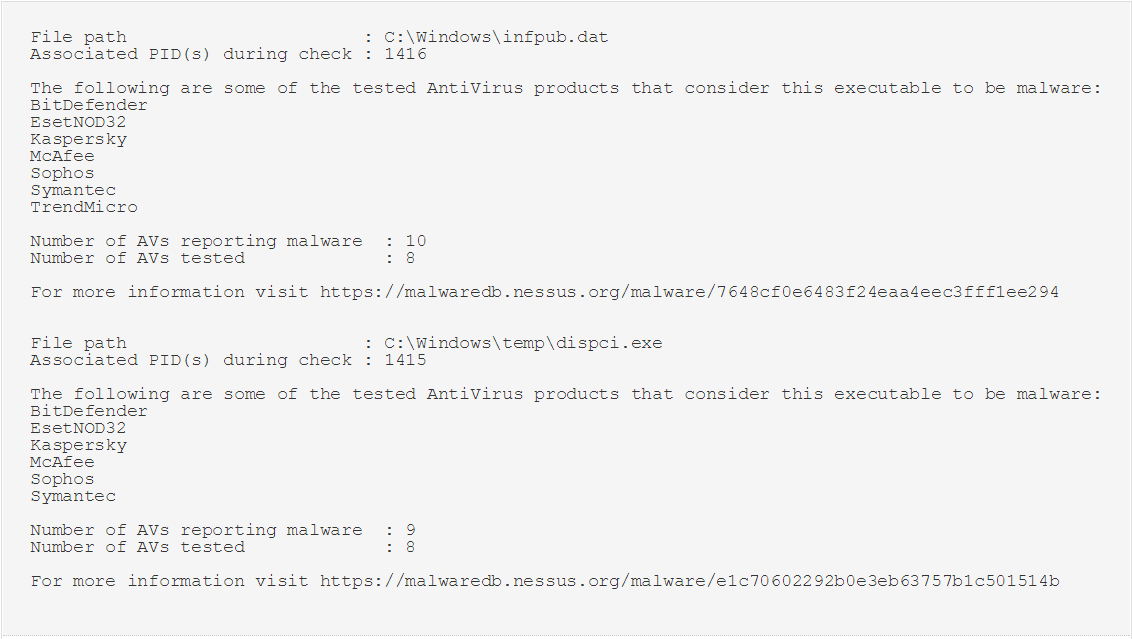
How to find Assets
You will need to assess and analyze assets to understand and ultimately mitigate your cyber risk. You can use the VM Vulnerabilities workbench in Tenable.io to close in on vulnerabilities and reduce your overall exposure. To use the workbench, you will need to create an advanced search and apply the following filters:
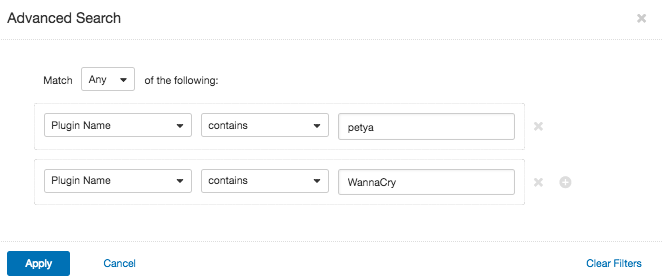
After you apply the search, you will see the affected assets and you can take the first steps in mitigating your cyber risk.
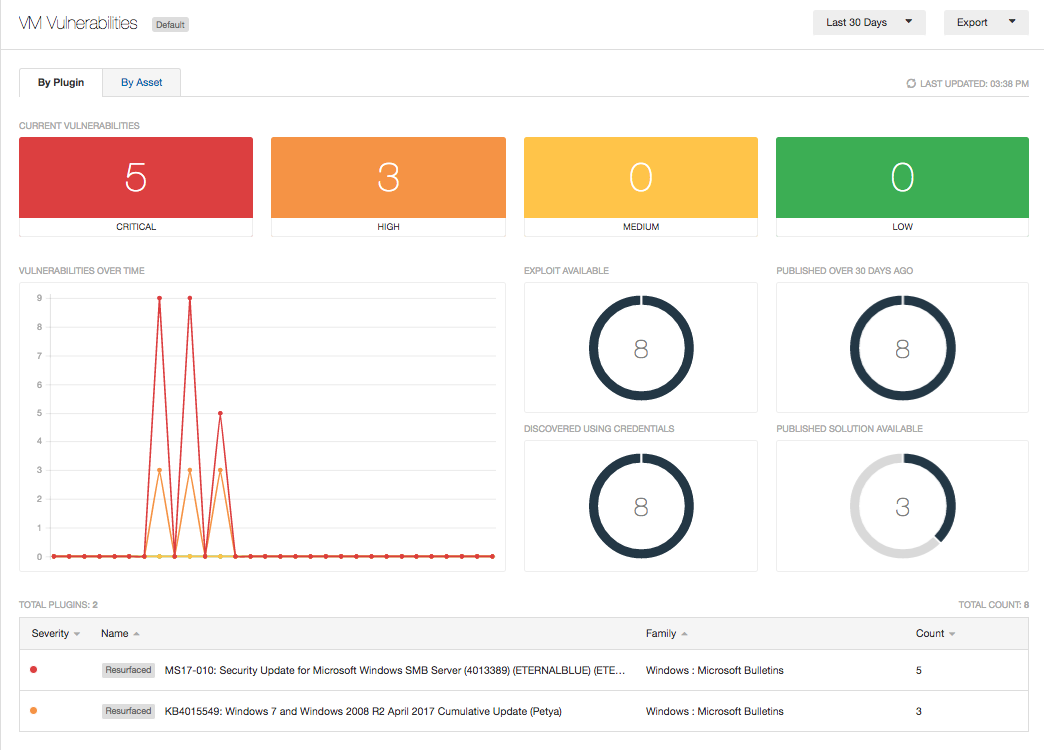
As your modern attack surface changes, you must set up vulnerability scanning to collect data using active scanning and agent scanning. This assessment process allows you to detect changes in the network and establish the state of your network against your previously defined baseline. A good baseline tracks indicators such as hardening standards, known assets and the locations of critical assets. Tenable.io allows you to put assets in the correct context to better understand and establish the priority of mitigation efforts. If the WannaCry or Petya vulnerabilities are still in your network, assets with these vulnerabilities need to be moved to the top of your priority list.
Wrap up
Most ransomware exploits well-known vulnerabilities that already have patches available. Implementing a proactive security program that includes regular patching and system updating is one of the best strategies you can use to prevent malware from infecting your systems. Make it a regular habit to patch and protect your assets.
For more information
- Learn more about Tenable.io, the first vulnerability management platform for all modern assets
- Get a free 60-day trial of Tenable.io
Many thanks to the Tenable research team for their contributions to this blog.
- Malware

