Cybersecurity Snapshot: CISA Calls on Software Makers To Use Memory Safe Languages, as OpenSSF Issues Secure Software Principles

CISA is urging developers to stamp out memory vulnerabilities with memory safe programming languages. Meanwhile, the OpenSSF published 10 key principles for secure software development. Plus, malware used in fake browser-update attacks ballooned in Q3. In addition, a new program aims to boost the cyber defenses of critical infrastructure orgs. And much more!
Dive into six things that are top of mind for the week ending December 8.
1 - CISA: Adopt memory safe programming languages, pronto!
Calling memory vulnerabilities a “major problem,” the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a clarion call for software makers to use so-called “memory safe” programming languages.
CISA urged both C-level executives and tech leaders at software companies to prioritize memory safe coding in its new “The Case for Memory Safe Roadmaps” document, released this week.
“Memory safe programming languages (MSLs) can eliminate memory safety vulnerabilities. Therefore, transitioning to MSLs would likely greatly lessen the need to invest in activities aimed at reducing these vulnerabilities or minimizing their impact,” reads the 23-page guide.

Jointly issued with several international cyber agencies and with other U.S. law enforcement agencies, the document details steps software makers can take to create memory safe roadmaps and eliminate memory vulnerabilities.
It also includes a list of memory safe languages: C#, Go, Java, Python, Rust and Swift.
For more details, check out:
- The CISA alert “CISA Releases Joint Guide for Software Manufacturers: The Case for Memory Safe Roadmaps”
- The CISA announcement “CISA, NSA, FBI and International Cybersecurity Authorities Publish Guide on The Case for Memory Safe Roadmaps”
- “The Case for Memory Safe Roadmaps” document
To get more information about memory safe programming:
- “The Move to Memory-Safe Programming” (IEEE Spectrum)
- “Shift to Memory-Safe Languages Gains Momentum” (Dark Reading)
- “Efforts to improve memory safety in software gain momentum” (TechTarget)
- "Automated Code Repair to Ensure Memory Safety" (Software Engineering Institute, Carnegie Mellon Univ.)
VIDEO
How can memory safe code stop hackers? (Low Level Learning)
2 - OpenSSF issues key principles for secure software development
And speaking of secure software development, anyone involved with building software – commercial vendors, enterprise developers, open source collaborators – should check new guidance from the Open Source Security Foundation (OpenSSF).
This week, the group published version 1.0 of its “Secure Software Development Guiding Principles” list, which it describes as core security practices for software producers and suppliers.

The 10 principles touch on areas such as:
- Secure software development and design methods
- Vulnerability prevention, detection, disclosure and mitigation
- Software supply chain transparency
To get more details and see the list, check out:
- The blog “OpenSSF Releases Top 10 Secure Software Development Guiding Principles”
- The Github page “Secure Software Development Guiding Principles version 1.0”
- The blog “Join Us in Adopting the Open Source Consumption Manifesto”
For more information about secure software development practices:
- “Secure Development” (Software Engineering Institute, Carnegie Mellon Univ.)
- “Secure Software Development Framework” (NIST)
- "Top security-by-design frameworks" (TechTarget)
- “Secure development and deployment guidance” (UK NCSC)
- “Top 4 best practices to secure the SDLC” (TechTarget)
3 - U.S. gov’t offers free cyber services to critical infrastructure orgs
Good news for critical infrastructure facilities that lack sufficient cybersecurity resources. CISA has launched a no-cost pilot program to help them shore up their defenses.
As part of the program, critical infrastructure organizations that are “target rich” but “resource poor” can request to receive managed cybersecurity services, CISA said in an announcement.
Specifically, the program now offers CISA’s “Protective Domain Name System (DNS) Resolver” service, which is designed to help prevent systems from connecting to malicious domains.

CISA is working with critical infrastructure organizations in healthcare, water and education. It plans to deliver program services to up to 100 entities in the coming year, as well as expand the menu of services available.
Critical infrastructure operators interested in participating in the program should contact a security advisor at their region’s CISA office.
In addition to helping critical infrastructure organizations, the program is expected to boost national security and expand the government’s insight into evolving threats against these facilities, CISA said.
To get more details:
- Read CISA’s announcement “Piloting New Ground: Expanding Scalable Cybersecurity Services to Protect the Broader Critical Infrastructure Community”
- Check out the page for the “Protective Domain Name System Resolver” service
For more information about protecting critical infrastructure from cyberattacks, check out these Tenable resources:
- “Securing Critical Infrastructure: The Essential Role of Public-Private Partnerships” (blog)
- “Experts Share Ways To Improve Manufacturing Sector IT/OT Security” (on-demand webinar)
- “Securing Critical Infrastructure: What We've Learned from Recent Incidents” (blog)
- “Understanding the Key Principles, Challenges, and Solutions of Securing OT and ICS” (on-demand webinar)
- “How Can We Strengthen the Cybersecurity of Critical Infrastructure? Here Are My Suggestions” (blog)
- “ETHOS: Bringing the OT Security Community Together for Threat Information Sharing” (blog)
VIDEO
Anatomy of a Threat: Rockwell Automation Vulnerabilities (CVE-2023-3595) and (CVE-2023-3596)
4 - Sidestep the risks of “lift and shift” cloud migrations
Taking a “lift and shift” approach to cloud migration is generally not recommended, but if you must, the U.K.’s cyber agency has some advice so you avoid common pitfalls.
“Lift and shift,” in which you replicate an on-premises system in the cloud, often yields inefficient, insecure and costly deployments that fail to take advantage of the benefits of cloud computing.

However, it is a common practice, and a good option in some cases, so the U.K. National Cyber Security Centre just published recommendations for those taking the “lift and shift” road.
“Our new guidance explains how by going beyond a simple ‘lift and shift’ implementation, you can avoid the worst problems of the migration strategy,” reads the NCSC blog announcement.
NCSC recommendations in the “How to ‘lift and shift’ successfully” guide include:
- Before migrating, securely configure the chosen platform
- Plan the migration by, for example, taking inventory of assets, avoiding unnecessary customization and simplifying the existing permissions model
- Avoid exposing legacy management protocols on the internet
- Automate maintenance for things such as patching and logging
- Migrate applications to a cloud-native approach
To get more details, check out:
- The blog “New cloud guidance: how to 'lift and shift' successfully”
- The “How to ‘lift and shift’ successfully” guide
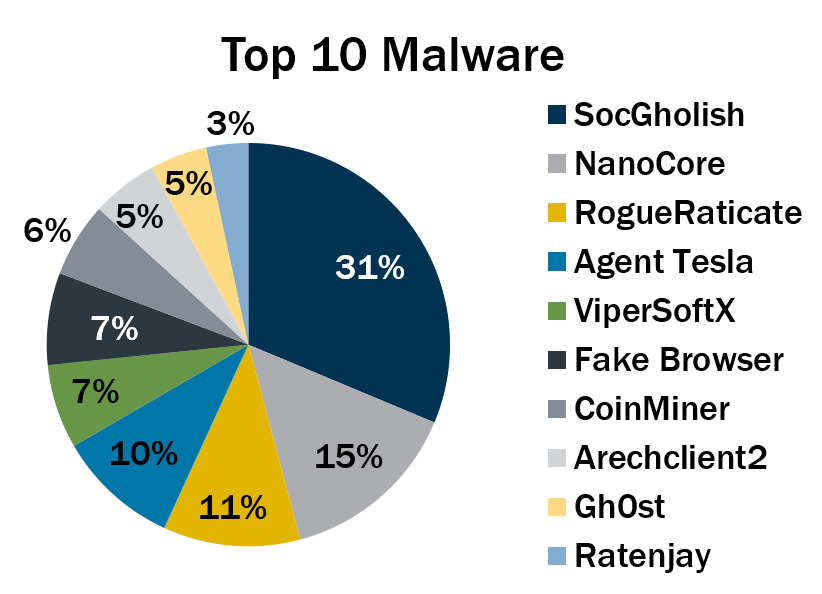
5 - Malware used in fake browser attacks surges in Q3
The third quarter saw a rise in malware that infects systems after users are duped into installing a fake browser update.
That’s according to the Center for Internet Security (CIS), which this week released its “Top 10 Malware Q3 2023” list.
SocGholish, which didn’t make the list last quarter, shot up to the top spot, accounting for 31% of malware incidents in the third quarter. Its success was due to a recent campaign pushing fake browser updates for initial access to compromised systems.
Fake browser update attacks also propelled two other malware variants into the third quarter’s list: RogueRaticate and Fake Browser.
(Source: Center for Internet Security)
Here’s the full list, in descending order:
- SocGholish, a downloader distributed through malicious websites that tricks users into downloading it by offering fake software updates
- NanoCore, a remote access trojan (RAT) that spreads via malspam as a malicious Excel spreadsheet
- RogueRaticate, a downloader distributed through malicious or compromised websites using fake browser updates.
- Agent Tesla, a RAT that captures credentials, keystrokes and screenshots
- Fake Browser, a downloader distributed through malicious or compromised websites using fake browser updates
- ViperSoftX, a multi-stage crypto stealer that's spread within torrents and file sharing sites
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI)
- Arechclient2, also known as SectopRAT, is a .NET RAT whose capabilities include multiple stealth functions
- Gh0st, a RAT designed to control infected endpoint devices
- Ratenjay, a RAT that's dropped by other malware, executes remote commands and has keylogging capabilities
To get more information, check out the CIS blog report, which offers details, context and indicators of compromise for each malware strain.
For details on fake browser update attacks:
- “The Fake Browser Update Scam Gets a Makeover” (Krebs on Security)
- “Atomic Stealer malware strikes macOS via fake browser updates” (Bleeping Computer)
- “Hackers Use Fake Browser Updates for AMOS Malware Attacks Targeting Mac Users” (MSSP Alert)
- “New ‘Big Head’ ransomware displays fake Windows update alert” (Bleeping Computer)
- “Hackers have been spreading malware via fake Chrome updates” (TechRadar)
VIDEO
Fake Chrome Update Malware (The PC Security Channel)
Apple Mac OS users falling for fake browser update that installs malware (Windows, Computers and Technology)
6 - Checking in on vulnerability management practices
During our recent webinar “Tenable Vulnerability Management Customer Update - December 2023,” we took the opportunity to poll attendees about their vulnerability management dashboards. Here’s what they said when we asked them how often they check their dashboards and what dashboard features are most important to them.
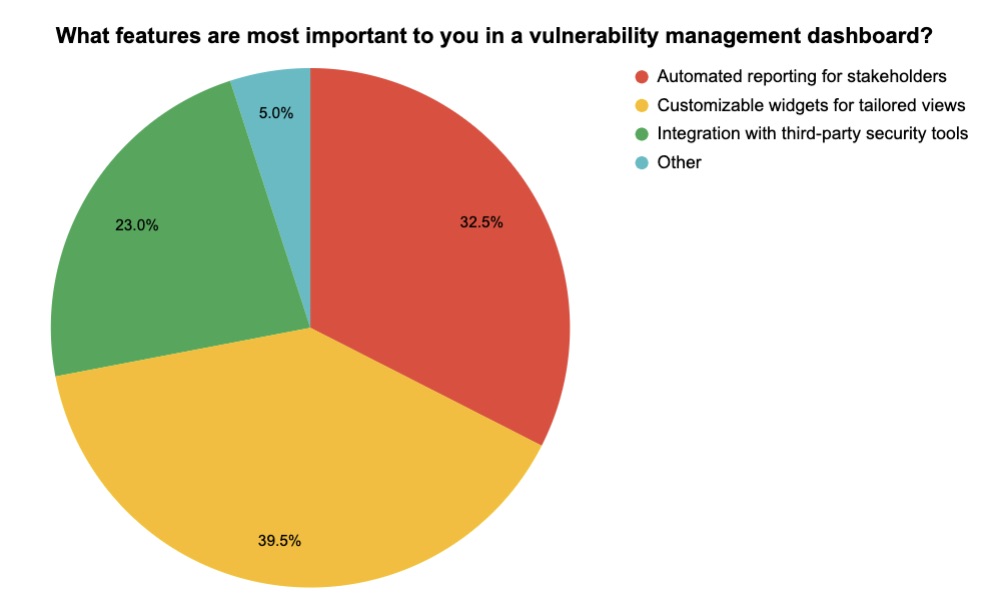
(200 respondents polled by Tenable in December 2023)
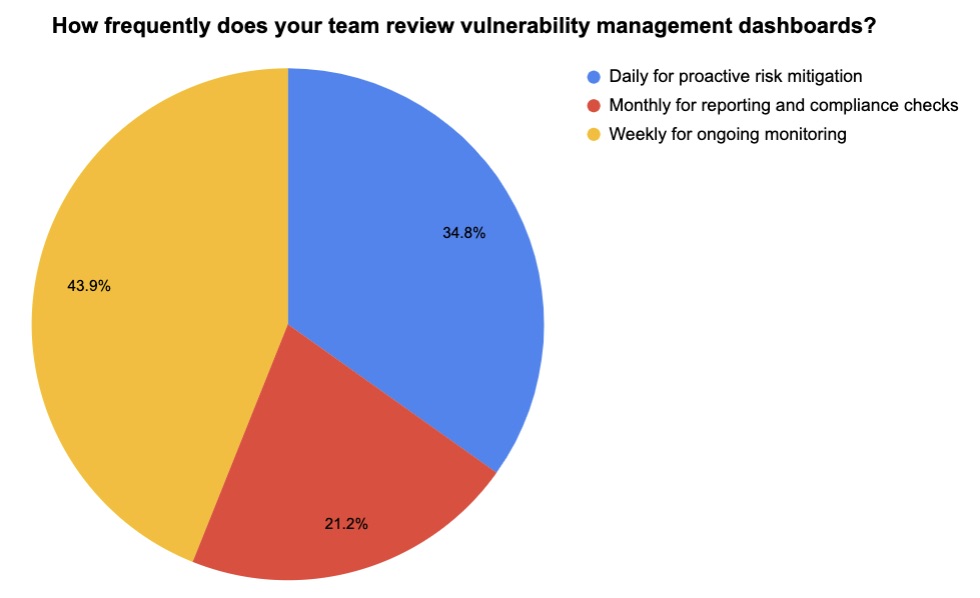
(198 respondents polled by Tenable in December 2023)
Want to learn what was discussed during the webinar “Tenable Vulnerability Management Customer Update - December 2023”? Watch it on demand!
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- OT Security
- Vulnerability Management


