Cybersecurity Snapshot: 6 Things That Matter Right Now

Topics that are top of mind for the week ending Aug. 26 | The “platformization” of hybrid cloud security. Budgeting guidance for CISOs. Tackling IT/OT cybersecurity challenges. Tips for complying with HIPAA’s cybersecurity rule. A roundup of patches, trends and incidents to keep an eye on. And much more!
1 - IDC sees shift to “platformization” of hybrid cloud security
Expect cloud workload security offerings to evolve from being siloed products into becoming integrated components of broader security and IT platforms in the next two years. That’s according to IDC’s “Worldwide Cloud Workload Security Forecast, 2022-2026.”
What’s driving this “platformization” shift? A search for simplicity by security teams, as digital transformation extends organizations’ attack surface, complicating the protection of increasingly hybrid and multi-cloud IT environments.
“Separate and disconnected offerings to support applications developers, security practitioners, or cloud operations will give way to comprehensive solutions to address the complexity that customers bring upon themselves,” reads the report.
IDC predicts that the “platform reality” will materialize by 2024 in this market, which it defines as products that protect three software-defined compute environments – virtual machine software, containers and cloud system software.
Meanwhile, organizations will spend $5.1 billion globally on cloud workload security software in 2026, up from $2.2 billion last year, a compound annual growth rate of 18.5%, according to IDC.
(Source: IDC “Worldwide Cloud Workload Security Forecast, 2022-2026: Complexity Drives the Market Up and to the Right”, Doc # US49522022, August 2022.)
More information about cloud security:
- “Cloud Security Definition (TechTarget)
- “Top Threats to Cloud Computing Pandemic Eleven” (Cloud Security Alliance)
- “Cloud security in 2022: A business guide to essential tools and best practices” (ZDNet)
- “CNAPP: What Is It and Why Is It Important for Security Leaders?” (Tenable)
- “Cloud Security for Beginners: Part 1 - Starting Off in the Cloud” (SANS Institute)
2 - Survey: Cyberattacks are #1 business risk
It wasn’t that long ago that CEOs and board directors viewed cybersecurity as one of many technology areas with a somewhat weak and unclear impact on the business. Not anymore.
The latest proof comes from a PwC survey of 722 U.S. business leaders in which respondents ranked cybersecurity as – wait for it – the top business risk for their organizations.
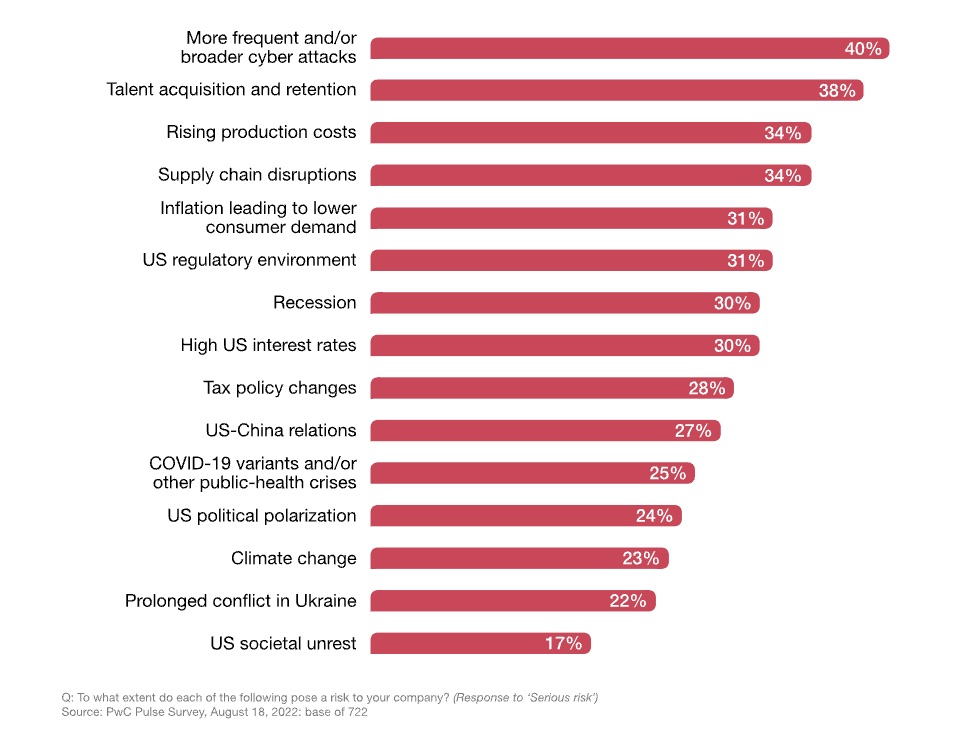
Specifically, 40% of all respondents listed it as a “serious” risk, while 38% labeled it a “moderate” risk.
Among the different categories of business leaders, board members are the most worried about cybersecurity: 51% of them ranked it as a “serious” risk.
Moreover, 84% of respondents said they’re either acting on or closely monitoring policy areas related to cybersecurity, while 79% are revising or enhancing their cyber risk management.
Recommendations include:
- Incorporate cybersecurity into the agendas of the C-suite and the board, and view it as a business issue, not purely a technology one.
- Have a security awareness program in place to train employees on cybersecurity practices.
- Ensure cybersecurity considerations and plans are part of all business initiatives.
- Use data to regularly assess and analyze your cybersecurity risks.
More information:
- “Manage the business risks behind cybersecurity” (Grant Thornton)
- “Leaders agree that cybersecurity is a business risk, but are they acting on that belief?” (TechRepublic)
- “The SEC Is Serious About Cybersecurity. Is Your Company?” (Harvard Business Review)
- “Cybersecurity Isn't an IT Risk, It's a Business Risk” (CMSWire)
- “Creating a technology risk and cyber risk appetite framework” (McKinsey & Co.)
3 - Cybersecurity help for healthcare companies
Healthcare organizations looking for guidance on how to comply with the security rule in the U.S. Health Insurance Portability and Accountability Act (HIPAA) now have a new resource, at a time when this industry faces intensifying attacks from cybercriminals.
A new draft publication from the National Institute of Standards and Technology (NIST) goes deep into how to protect patients’ electronic records in accordance with the HIPAA security rule.

Specifically, this document, which revises a NIST guide from 2008, maps the HIPAA security rule to NIST’s Security and Privacy Controls for Information Systems and Organizations (NIST SP 800-53) framework.
Readers will find guidance, templates, tools and more, on topics including:
- Risk assessment and risk management
- Telehealth/telemedicine guidance
- Mobile device security
- Cloud services
- Ransomware and phishing
- Education, training and awareness
- Medical device and medical Internet of Things (IoT) security
More information:
- “NIST revises cybersecurity guidelines specifically for HIPAA” (FCW)
- “NIST Updates Guidance for Health Care Cybersecurity” (NIST)
- “NIST Updates Guidance on HIPAA Security Rule Compliance” (HIPAA Journal)
- “NIST revises healthcare guidance to improve HIPAA Security Rule compliance” (Healthcare IT News)
- “Data of Nearly 2M Patients Exposed in Ransomware Attack on Healthcare Debt Collection Firm” (DarkReading)
4 - Forrester: Budget guidance for CISOs
Budget planning season is here for many organizations, so what should CISOs and other security and risk management leaders be focusing on for 2023? Forrester has some suggestions for them on how to best allocate their cybersecurity budgets.
For example, among the key cybersecurity areas Forrester recommends prioritizing are:
- API security
- Cloud workload security
- Multifactor authentication
- Security analytics
- Zero Trust network access
- Crisis simulation exercises
It also suggests evaluating and experimenting with emerging technologies such as extended detection and response, attack surface management and privacy-preserving technology.
For more details, check out the blog “New Security & Risk Planning Guide Helps CISOs Set 2023 Priorities” and the full report “Planning Guide 2023: Security & Risk,” which is available to Forrester subscribers and for purchase.
More information about cybersecurity budgeting:
- “5 key considerations for your 2023 cybersecurity budget planning” (CSO)
- “Cybersecurity budget breakdown and best practices” (TechTarget)
- “Cybersecurity Budget Process” (video by Steve Murphy)
5 - Good news and bad news about IT/OT convergence
The draft report about the cybersecurity issues of IT and OT convergence from the U.S. National Security Telecommunications Advisory Committee (NSTAC) is out. Good news or bad news first?
Ok, the bad news: There’s plenty to do to properly protect the converged IT/OT systems of critical infrastructure facilities. The good news? The U.S. has the technology and the knowledge to fix the problems. All that’s missing is a sense of urgency.
Key findings from the report, which has been sent to the White House:
- IT/OT convergence cybersecurity challenges aren’t new. But this would be new: Prioritizing the allocation of required resources to implement solutions.
- Organizations are confused about what cybersecurity protections they need. Why?
- The government hasn’t provided clear guidance.
- They lack visibility into their OT environments.
- Some lack enough staff and money, especially smaller ones.
- There’s essential legacy OT equipment that wasn’t designed to be connected to the internet.
- IT and OT teams are often siloed. They must be brought together to better secure converged IT/OT environments.
- The government and the private sector rarely include cybersecurity capabilities among the requirements of OT products they’re shopping around for.
- There’s not enough cybersecurity education and training available to the staff of critical infrastructure providers.
So what can be done? Recommendations include:
- The Cybersecurity and Infrastructure Security Agency (CISA) should require civilian branch departments and agencies of the U.S. government to maintain a real-time, continuous inventory of all OT assets.
- CISA should ensure that agencies include cybersecurity provisions in their OT procurement requirements.
- CISA and the National Security Council should develop and implement “interoperable, technology-neutral and vendor-agnostic” mechanisms for sharing sensitive information.
For more information:
- “President’s NSTAC advisory committee proposes real-time monitoring of operational technology across federal agencies” (FedScoop)
- “Smart factories unprepared for cyberattacks” (CSO)
- “Proactive OT Cyber Maintenance Practices” (S4 Events)
- “Why ICS/OT Infrastructure is Insecure” (International Society of Automation)
- “How Can We Strengthen the Cybersecurity of Critical Infrastructure?” (Tenable)
6 - Quick takes
And finally, a roundup of vulnerabilities, trends, news and incidents you might be interested in.
- Vulnerabilities in Mozilla Firefox and Mozilla Thunderbird could open the door for arbitrary code execution by attackers.
- Common configuration errors are at the root of more than 80% of ransomware attacks, according to Microsoft.
- Cybercriminals are leveraging legitimate red teaming tool Brute Ratel for attacks.
- The BlackByte ransomware group has added a tiered payment system to its data leak site.
- A ransomware attack hobbled a French hospital to such an extent it had to transfer patients and cancel scheduled surgeries due to the impact to its operations.
- Beware that DDoS alert: It could be an attempt to infect you with a RAT malware.
- Google said it blocked the largest HTTPS DDoS attack on record. Launched in June, it reportedly peaked at 46 million requests per second.
- Twitter’s former head of security is alleging that the company is plagued by significant cybersecurity problems. Twitter brushed off the allegations, saying they’re inconsistent and inaccurate.
- A researcher is warning about possible keylogging by TikTok.
- Cybersecurity Snapshot
