CVE-2023-27997: Heap-Based Buffer Overflow in Fortinet FortiOS and FortiProxy SSL-VPN (XORtigate)

Fortinet says a critical flaw in its SSL-VPN product may have been exploited in the wild in a limited number of cases. Organizations are strongly encouraged to apply these patches immediately.
Background
On June 12, Fortinet published an advisory (FG-IR-23-097) for a critical vulnerability in FortiOS and FortiProxy:
| CVE | Description | CVSSv3 | Severity |
|---|---|---|---|
| CVE-2023-27997 | FortiOS and FortiProxy Heap Buffer Overflow in SSL-VPN | 9.2 | Critical |
In addition to CVE-2023-27997, Fortinet patched several other vulnerabilities including:
| CVE | Description | CVSSv3 | Severity |
|---|---|---|---|
| CVE-2023-29181 | FortiOS - Format String Bug in Fclicense daemon | 8.3 | High |
| CVE-2023-29180 | FortiOS Null pointer de-reference in SSLVPNd | 7.3 | High |
| CVE-2023-22640 | FortiOS & FortiProxy Out-of-bound-write in SSLVPNd | 7.1 | High |
| CVE-2023-29179 | FortiOS Null pointer de-reference in SSLVPNd proxy endpoint | 6.4 | Medium |
| CVE-2023-22641 | FortiOS & FortiProxy Open redirect in SSLVPNd | 4.1 | Medium |
Analysis
CVE-2023-27997 is a heap-based buffer overflow vulnerability in the secure socket layer virtual private network (SSL VPN) functionality in FortiOS and FortiProxy in Fortinet devices including its FortiGate Next Generation Firewalls (NGFW). An unauthenticated, remote attacker could exploit this vulnerability by sending specially crafted requests to a vulnerable device. Successful exploitation would grant an attacker the ability to execute arbitrary code on the vulnerable device.
The vulnerability was discovered by security researchers Charles Fol and Dany Bach of LEXFO. On June 11, Fol tweeted about the availability of patches for the flaw, adding that it is “reachable pre-authentication, on every SSL VPN appliance.”
#Fortinet published a patch for CVE-2023-27997, the Remote Code Execution vulnerability @DDXhunter and I reported. This is reachable pre-authentication, on every SSL VPN appliance. Patch your #Fortigate. Details at a later time. #xortigate
— Charles Fol (@cfreal_) June 11, 2023
Fortinet has published a blog post providing additional information on CVE-2023-27997 as well as several other flaws that have been addressed as part of its recent firmware updates. In the blog, Fortinet notes that CVE-2023-27997 “may have been exploited in a limited number of cases.”
This disclosure is similar to past disclosures from Fortinet in October 2022 for CVE-2022-40684, a critical authentication bypass in FortiOS and FortiProxy, and December 2022 for CVE-2022-42475, a separate heap-based buffer overflow in FortiOS SSL VPNs.
CVE-2022-42475 was exploited in the wild by suspected Chinese threat actors to compromise a government entity in Europe and a managed service provider in Africa, while Fortinet says in its recent blog post about CVE-2023-27997 that CVE-2022-40684 was exploited by a recently discovered threat actor known as Volt Typhoon.
Nearly 260,000 Fortinet FortiGate firewalls are publicly accessible
According to a Shodan search query shared by BleepingComputer, there are nearly 260,000 Fortinet FortiGate firewalls that are publicly accessible. The United States tops the list with nearly 40,000 publicly accessible devices, followed by India (21,237) and Brazil (10,844).
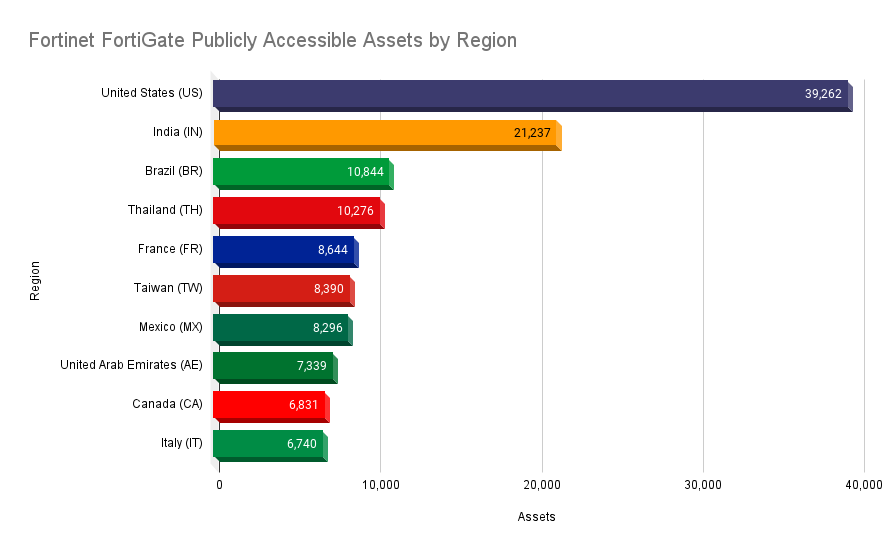
Image Source: Tenable, June 2023 | Data Source: Shodan, June 2023
A similar search query used on BinaryEdge showed that there are over 417,000 FortiGate firewalls publicly accessible.
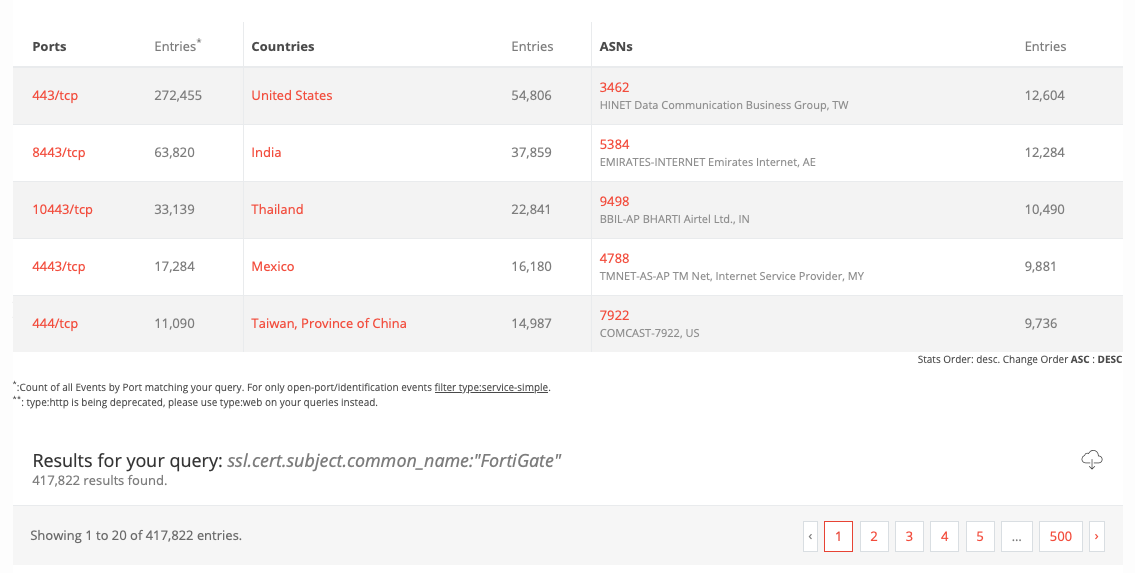
Image Source: Tenable, June 2023
SSL VPN flaws are an easy target for cybercriminals for initial access
Over the last five years, Tenable Research has observed several vulnerabilities in SSL VPNs from vendors like Citrix, Pulse Connect and Fortinet exploited in the wild by a variety of attackers including the now defunct Conti ransomware group. For instance, U.S. agencies including the Federal Bureau of Investigation (FBI) and Cybersecurity and Infrastructure Security Agency (CISA) have issued cybersecurity advisories highlighting flaws in Fortinet devices, and have warned about SSL-VPN flaws being exploited by nation-state groups aligned with Russia and the Iranian Islamic Revolutionary Guard Corps (IRGC).
The Tenable Security Response Team published a blog post in August 2021 underscoring the threat that unpatched SSL VPN vulnerabilities pose to organizations around the world and we’ve routinely covered them in each of our annual Threat Landscape Reports in 2020, 2021 and 2022.
Proof of concept
At the time this blog post was published, no proof-of-concept (PoC) exploit code was available for CVE-2023-27997.
Solution
According to Fortinet’s advisory, the following are the affected versions of FortiOS and FortiProxy and the relevant fixed versions:
| Product | Affected Versions | Fixed Versions |
|---|---|---|
| FortiOS-6K7K | 7.0.5, 7.0.10 | 7.0.12 or above |
| FortiOS-6K7K | 6.4.2, 6.4.6, 6.4.8, 6.4.10, 6.4.12 | 6.4.13 or above |
| FortiOS-6K7K | 6.2.4, 6.2.6 through 6.2.7, 6.2.9 through 6.2.13 | 6.2.15 or above |
| FortiOS-6K7K | 6.0.10, 6.0.12 through 6.0.16 | 6.0.17 or above |
| FortiOS | 7.2.0 through 7.2.4 | 7.2.5 or above |
| FortiOS | 7.0.0 through 7.0.11 | 7.0.12 or above |
| FortiOS | 6.4.0 through 6.4.12 | 6.4.13 or above |
| FortiOS | 6.0.0 through 6.0.16 | 6.0.17 or above |
| FortiProxy | 7.2.0 through 7.2.3 | 7.2.4 or above |
| FortiProxy | 7.0.0 through 7.0.9 | 7.0.10 or above |
| FortiProxy | 2.0.0 through 2.0.12 | 2.0.13 or above |
| FortiProxy | All versions of 1.1 and 1.2 | 2.0.13 or above |
Fortinet says if a customer has SSL-VPN enabled they should “take immediate action to upgrade” to the latest firmware version. While SSL-VPN functionality being disabled mitigates the issue, Fortinet still “recommends upgrading.”
Identifying affected systems
A list of Tenable plugins to identify this vulnerability can be found here. This link uses a search filter to ensure that all matching plugin coverage will appear as it is released. In addition, plugin ID 73522 can be used to identify Fortinet devices in your network. A Tenable audit with best practices for Fortigate FortiOS is also availablehere which can help with security hardening.
Get more information
- Fortinet PSIRT FG-IR-23-097 for CVE-2023-27997
- Fortinet Blog on CVE-2023-27997 and Clarifications on Volt Typhoon Campaign
- Tweet from Charles Fol on CVE-2023-27997
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management


