by Cody Dumont
February 17, 2015
Keeping up with compliance standards can be a difficult task, even more so when minor changes impact many devices in the network. The PCI Council released a special bulletin that says all versions of SSL/TLS are no longer acceptable; this was preceded by NIST making the same requirement. This dashboard provides a detailed view of SSL/TLS currently in use on the network.
The Payment Card Industry Security Standards Council (PCI SSC) released a special bulletin on February 13, 2015 announcing impending revisions to the Payment Card Industry Data Security Standard (PCI DSS) as well as the Payment Application Data Security Standard (PA-DSS). The stated purpose of this bulletin is to inform the payment card industry that the PCI SSC has determined that the Secure Sockets Layer (SSL) protocol is no longer an acceptable solution for the protection of data based on the PCI SSC’s definition of “strong cryptography.”
This dashboard helps identify several of the requirements that will be changed such as:
- 2.2.3 Implement additional security features for any required services, protocols, or daemons that are considered to be insecure.
- 2.3 Encrypt all non-console administrative access using strong cryptography.
- 4.1 Use strong cryptography and security protocols (for example, SSL/TLS, IPSEC, SSH, etc.) to safeguard sensitive cardholder data during transmission over open, public networks.
- 4.1.g For SSL/TLS implementations, examine system configurations to verify that SSL/TLS is enabled whenever cardholder data is transmitted or received.
The components in this dashboard provide a detailed view of SSL usage in the network. There are several components that analyze data collected using active, passively, and through event correlation. By separating out the different methods of detecting SSL traffic, the analysts is able to better identify systems that are not in compliance and focus remediation efforts.
The dashboard and its components are available in the Security Center Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Security Center Feed under the category Compliance & Configuration Assessments.
The dashboard requirements are:
- Security Center 4.8.2
- Nessus 8.5.1
- NNM 5.9.1
Organizations will likely have to demonstrate or prove that SSLv2 or SSLv3 is not used in any the services, protocols, or daemons used regarding cardholder data environment. Removing SSL will also impact the use of web-based interfaces for administrative access to servers, databases, or network devices. As the remediation plans are developed the primary focus will highlight the fact that all transmissions of cardholder data such as web server traffic or secure file transfers will no longer be able to use SSLv2 or SSLv3. In addition, any internal solutions such as secure communications from Point of Sale (POS) systems to payment switches will also no longer be allowed to use SSLv2 or SSLv3.
Security Center provides continuous network monitoring to identify vulnerabilities, reduce risk, and ensure compliance. Tenable has the largest installed based and best know-how, and quickly identifies security and compliance issues. Security Center enables the analysts to react to advanced threats, zero-day vulnerabilities, and new forms of regulatory compliance. With more supported technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure, Security Center users are more prepared for the dynamic chaining environment.
Components
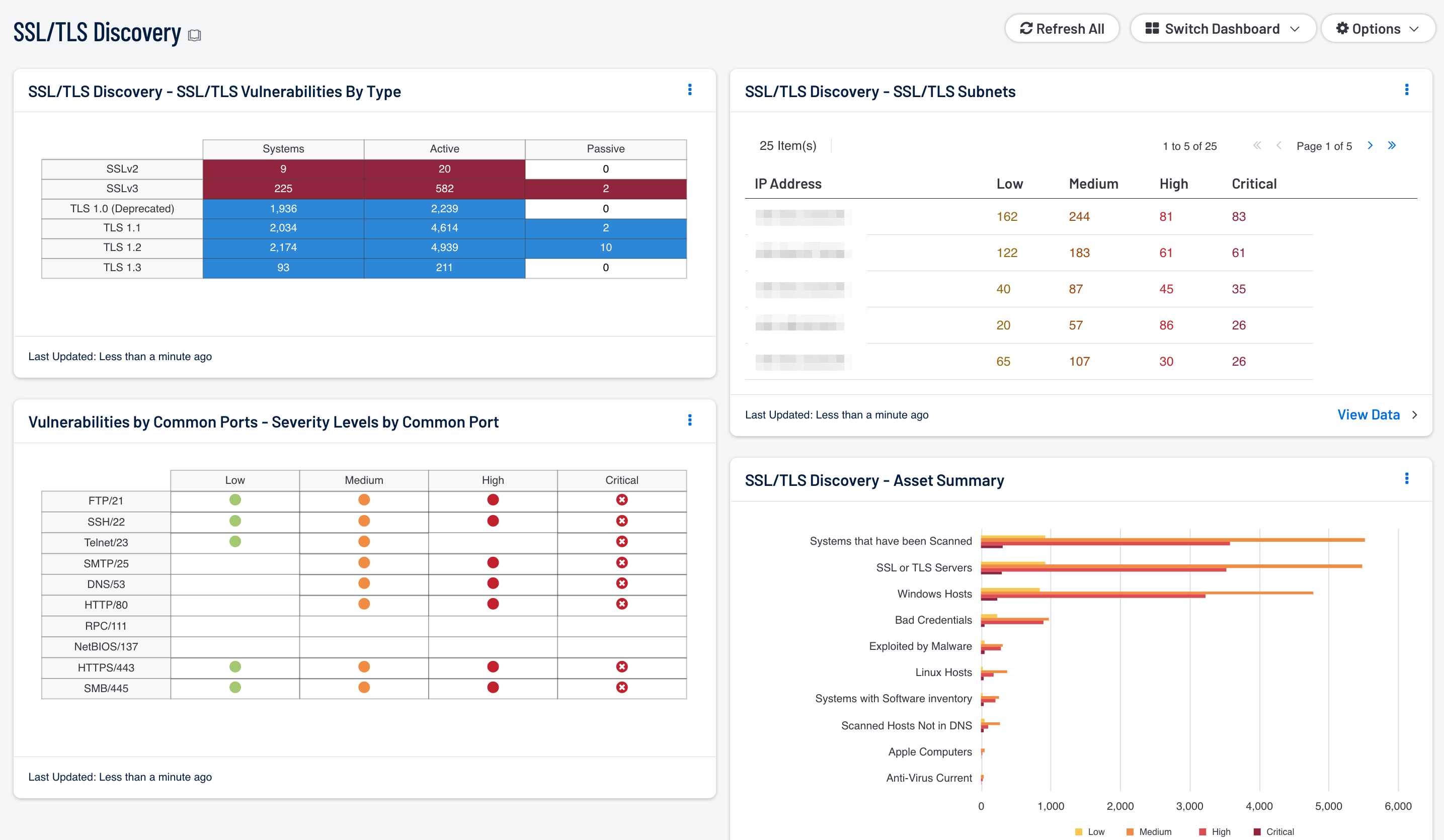
SSL/TLS Discovery - SSL/TLS Vulnerabilities By Type: This component provides an overview of systems and vulnerabilities related to SSL. By separating the view based on detection method and SSL version, the analysts can ensure that all SSL related PCI compliance issues are identified and can be mitigated. Also by identifying systems running TLS, the analyst is able to see which systems are in compliance.
Vulnerabilities by Common Ports - Severity Levels by Common Port: This component effectively uses color and empty space to convey information about vulnerabilities and risk severity. Each column is a severity level of low, medium, high, or critical. Each row is a common popular port chosen at random. Using this matrix as a template, a security administrator can modify the matrix to use assets, IP addresses, plugin families, repositories, and more. The icon colors can communicate risk: green for low severity, yellow for medium, and red for high severity. For the critical severities, the red icon with white 'X' is used. When no match is found, the default setting is an empty display text field.
SSL/TLS Discovery - Asset Summary: Using the Asset Summary tool, this bar chart provides a view of the top 10 most affected assets with SSL vulnerabilities. A separate bar for each severity starting with Low – Critical is displayed. The count is sorted using the vulnerability weight score. This data is used to help identify the assets requiring immediate attention.
SSL/TLS Discovery - SSL/TLS Subnets: Using the Class C Summary tool, this table provides a view of the top 10 most affected subnets with SSL vulnerabilities. A separate column for each severity starting with Low – Critical is displayed. The count is sorted using the vulnerability weight score. This data is used to help identify the subnets requiring immediate attention.