by Cody Dumont
August 23, 2016
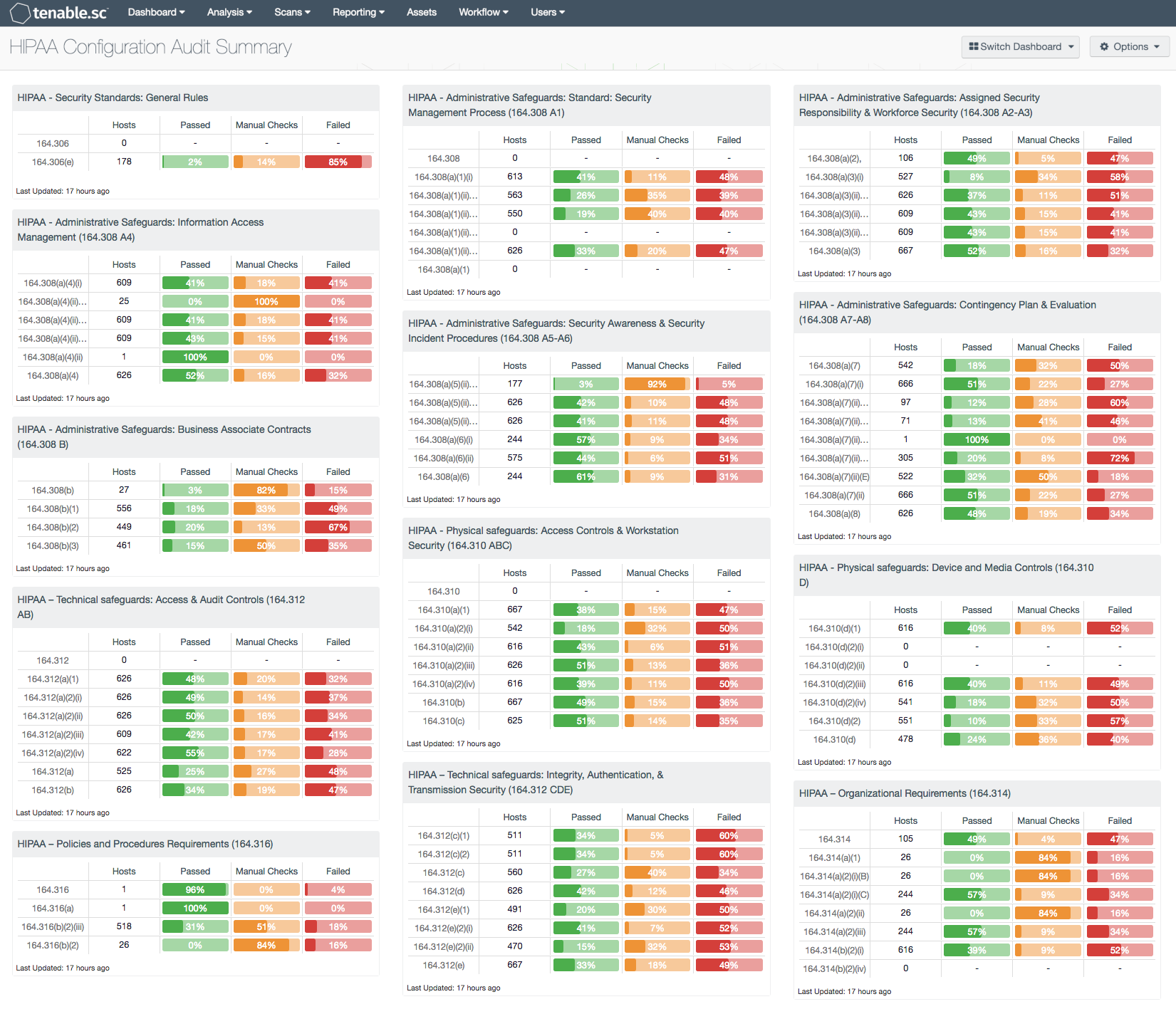
Healthcare providers involved in the transmission of protected health information (PHI) or electronic protected health information (ePHI) must comply with the Health Insurance Portability and Accountability Act (HIPAA) security rules. As system configuration complexity increases, the organization’s struggle to meet hardening standards continues to rise. This dashboard provides users with a simplistic view of HIPAA related configuration audit checks.
The Administrative Simplification provisions of the Health Insurance Portability and Accountability Act of 1996 (HIPAA, Title II) required the Department of Health and Human Services (HHS) to establish national standards for the security of electronic health care information. The final rule adopting HIPAA standards for security was published in the Federal Register on February 20, 2003. The legislation specifies a series of administrative, technical, and physical safeguards for covered entities to use to assure the confidentiality, integrity, and availability of electronic protected health information (ePHI). Each safeguard category consists of standards and implementation specifications. The Health Information Technology for Economic and Clinical Health (HITECH) Act was enacted as part of the American Recovery and Reinvestment Act of 2009. HITECH increases the scope of security and privacy protections for ePHI previously set forth by HIPAA. The HITECH Act also addresses liability and enforcement when violations or breaches occur.
This dashboard focuses on the configuration management aspect of HIPAA compliance. The configuration management auditing helps to ask and answer the questions:
- Do the policies and procedures specify the use of additional security measures to protect workstations with ePHI?
- If the organization has implemented a centralized configuration management technology, are the configurations enforced on all systems?
- Can the organization audit all workstations and demonstrate the successful implementation of standard policies, such as password length and complexity?
Tenable's Tenable.sc can measure compliance using audit files that cover a wide range of major regulations and other auditable standards. Tenable provides over 500 audit files, which are available within Tenable.sc, or can be downloaded from the Tenable Support Portal.
Tenable solutions can be used to audit systems based on Center for Internet Security (CIS) benchmarks and many other standards such as PCI DSS, CSF, NIST 800-53, 800-171, and many more. Using a field called a cross-reference, Tenable.sc has the ability to map compliance references from one standard (NIST 800-53) to HIPAA. The components in this dashboard use the cross reference from several well known standards, allowing for a more inclusive method of identifying configuration issues with that may be in violation of configuration guidelines. More information about audit files can be found in the Tenable Discussion Forums , Tenable Support Portal , Nessus Compliance Checks Guide , and Nessus Compliance Reference Guide.
Audit files can be customized to match the configuration settings defined by an organization's corporate policies. Audit files are easily created or modified to support the organization’s existing security policies. When an audit is performed with Nessus or the Log Correlation Engine (LCE), within each individual compliance check, the solutions attempt to determine if the host is compliant, non-compliant, or if the results are inconclusive and need to be verified manually. Unlike a vulnerability check that only reports if the vulnerability is actually present, a compliance check always reports a result. This way, the data can be used as the basis of an audit report to show that a host passed or failed a specific test, or if it could not be properly tested.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.2.0
- Nessus 8.5.1
- Tenable Audit Files with Cross References
Tenable's Tenable.sc provides continuous network monitoring to identify vulnerabilities, reduce risk, and ensure compliance. By frequently scanning systems, Tenable.sc can measure compliance in real-time with minimal human intervention. Tenable.sc easily identifies gaps in policy implementation; allowing for management to prioritize remediation actions. With more supported technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure; Tenable.sc can better assess the environment for compliance standards.
Components
HIPAA - Security Standards: General Rules: The audit checks in this component relate to general best practice security rules, such as confidentiality, integrity, and availability. The checks include protection against any reasonably anticipated threats or hazards, protection against any reasonably anticipated uses or disclosures, and other compliances related to the workforce.
HIPAA - Administrative Safeguards: Standard: Security Management Process (164.308 A1): The audit checks in this component relate to security management process, such as policy verification, risk analysis, risk management, sanction policies, and system activity review.
HIPAA - Administrative Safeguards: Assigned Security Responsibility and Workforce Security (164.308 A2-A3): The audit checks in this component relate to assigned security responsibility and workforce security. The enforcement policy controls help to monitor policies and procedures to ensure that all members of its workforce have appropriate access to electronic protected health information.
HIPAA - Administrative Safeguards: Information Access Management (164.308 A4): The audit checks in this component relates to information access management. These checks are in line with implementing policies and procedures for authorizing access to electronic protected health information that is consistent with the applicable requirements.
HIPAA - Administrative Safeguards: Security Awareness and Security Incident Procedures (164.308 A5-A6): The audit checks in this component relate to security awareness and training, with a focus on periodic security updates, login monitoring, password management, and incident procedures. These audit checks are all listed as addressable and focus less on the training of users and specifically setting for on periodic security updates, protection from malicious software, login monitoring, and password management.
HIPAA - Administrative Safeguards: Contingency Plan & Evaluation (164.308 A7-A8): The audit checks in this component relate to contingency planning. The audit checks support various aspects of contingency planning to include data backup plans, disaster recovery plans, emergency mode operation plans, testing and revision procedures, and applications and data criticality.
HIPAA - Administrative Safeguards: Business Associate Contracts (164.308 B): The audit checks in this component relate to business associate appropriately safeguarding information.
HIPAA - Physical safeguards: Access Controls and Workstation Security (164.310 ABC): The audit checks in this component relate to access controls, contingency operations, and workstation security. Workstation security policies include configuration policies that enforce the proper functions to be performed, and the manner in which those functions are to be performed. The legislation also covers the physical attributes of the surroundings of a specific workstation or class of workstation that can access electronic protected health information. Additionally, analysts need to deploy workstation security policies to implement physical safeguards for all workstations that access electronic protected health information, to restrict access to authorized users.
HIPAA - Physical safeguards: Device and Media Controls (164.310 D): The audit checks in this component relate to device and media controls. Analysts should implement policies and procedures that govern the receipt and removal of hardware and electronic media that contain electronic protected health information into and out of a facility, and track the movement of these items within the facility.
HIPAA – Technical safeguards: Access and Audit Controls (164.312 AB): The audit checks in this component relate to access control, unique user identification, automatic logoff, encryption and decryption, and audit controls. Analysts should implement technical policies and procedures for electronic information systems that maintain electronic protected health information to allow access only to those persons or software programs that have been granted access to health records.
HIPAA – Technical safeguards: Integrity, Authentication, and Transmission Security (164.312 CDE): The audit checks in this component relate to integrity and transmission security. Analysts should implement policies and procedures to protect electronic protected health information from improper alteration or destruction. Additional policies require analysts to implement technical security measures to guard against unauthorized access to electronic protected health information that is being transmitted over an electronic communications network.
HIPAA – Organizational Requirements (164.314): The audit checks in this component relate to the organizational requirements to reasonably and appropriately safeguard electronic protected health information created, received, maintained, or transmitted to or by the plan sponsor on behalf of the group health plan.
HIPAA – Policies and Procedures Requirements (164.316): The audit checks in this component relate to policies, procedures, and documentation requirements. The entity or business associate must implement reasonable and appropriate policies and procedures to comply with the standards, implementation specifications, or other requirements in HIPAA regulations.