by Cesar Navas
December 23, 2019
A vital step in the Cyber Exposure Life Cycle is assessing the configuration of systems within the network. Using automated tools to collect configuration information can greatly reduce the time needed to verify systems with proper configuration. This dashboard provides organizations with several data points related to configuration information collected during a vulnerability scan.
The CIS ControlsTM are a prioritized set of actions that collectively form a defense-in-depth set of best practices that mitigate the most common attacks against systems and networks. These controls were developed by IT professionals using operational experiences and generally accepted best practices; this dashboard will focus on Control 4 (Controlled Use of Administrative Privileges) & Control 5 (Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers).
Historically CIS has referred the first six CIS controls as cyber hygiene to focus an organization’s cybersecurity activities. The designation of cyber hygiene brought up the fact that these practices may be difficult for organizations with resource and/or expertise limitations. To address any resource or expertise limitation, CIS now recommends following Implementation Groups (IG) to help prioritize CIS control utilization. There are three IG’s, which describe organization by size. The IG specifies a subset of the controls that have been assessed to have a similar risk profile and resources to implement. The IG’s are also meant to be prioritized in IG order regardless of the IG organization size; for example, organizations should implement Sub-Controls in IG1, followed by IG2 and then IG3. The IG’s are described as organizations with limited resources and cybersecurity expertise (IG1); Organizations with moderate resources (IG2); Organizations with significant resources (IG3).
Control 4 requires organizations to verify users with high-privileged accounts do not use such accounts for day-to-day web surfing and email reading. Essentially tracking group memberships and determining if elevated groups have unnecessary privileges. Within the various sub controls there are two that apply to all IG’s, they are:
- Change Default Passwords
- Ensure the Use of Dedicated Administrative Accounts
To assist in implementing the various sub controls, the security operations team can use Tenable.sc to analyze group membership in local and domain groups. In addition to plugins that help monitor for group membership, there are also plugins to track the running processes, services, and other related indicators of elevated privileges.
Control 5 requires organizations to establish, implement, and actively manage the security configuration of mobile devices, laptops, servers, and workstations. The sub controls for Control 5 are mostly focused towards IG 2 & 3 with the exception of Sub Control 5.1, Establish Secure Configurations. This sub control requires using an established and documented configuration policy across all systems in the network. Using the CIS Benchmarks and Tenable.sc, the organization can verify the established configuration policies are followed. Taking advantage of implementing the first sub control, the operations team can be sure they are following security best practices and, in most cases, begin to implement to the other sub controls. In addition to Control 5, Controls 6.2 & 6.3 require the enabling of audit logs. This dashboard provides useful component that uses several key words to track common configuration issues, one of them being Logging configuration. Through the use of audit files and Informational plugins, Tenable.sc is able to report on and identify configuration issues and possible resolutions.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Executive.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.8.0
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provides the ability to Access assets for a compliance with security standards and related misconfigurations. By using active scanning with Nessus, Tenable.sc is able to collect and analyze systems for misconfiguration and hardening configuration. Tenable.sc provides customers with a full and completed Cyber Exposure platform for completing an effective Cyber Hygiene program prescribed by CIS Controls framework.
This dashboard contains the following components:
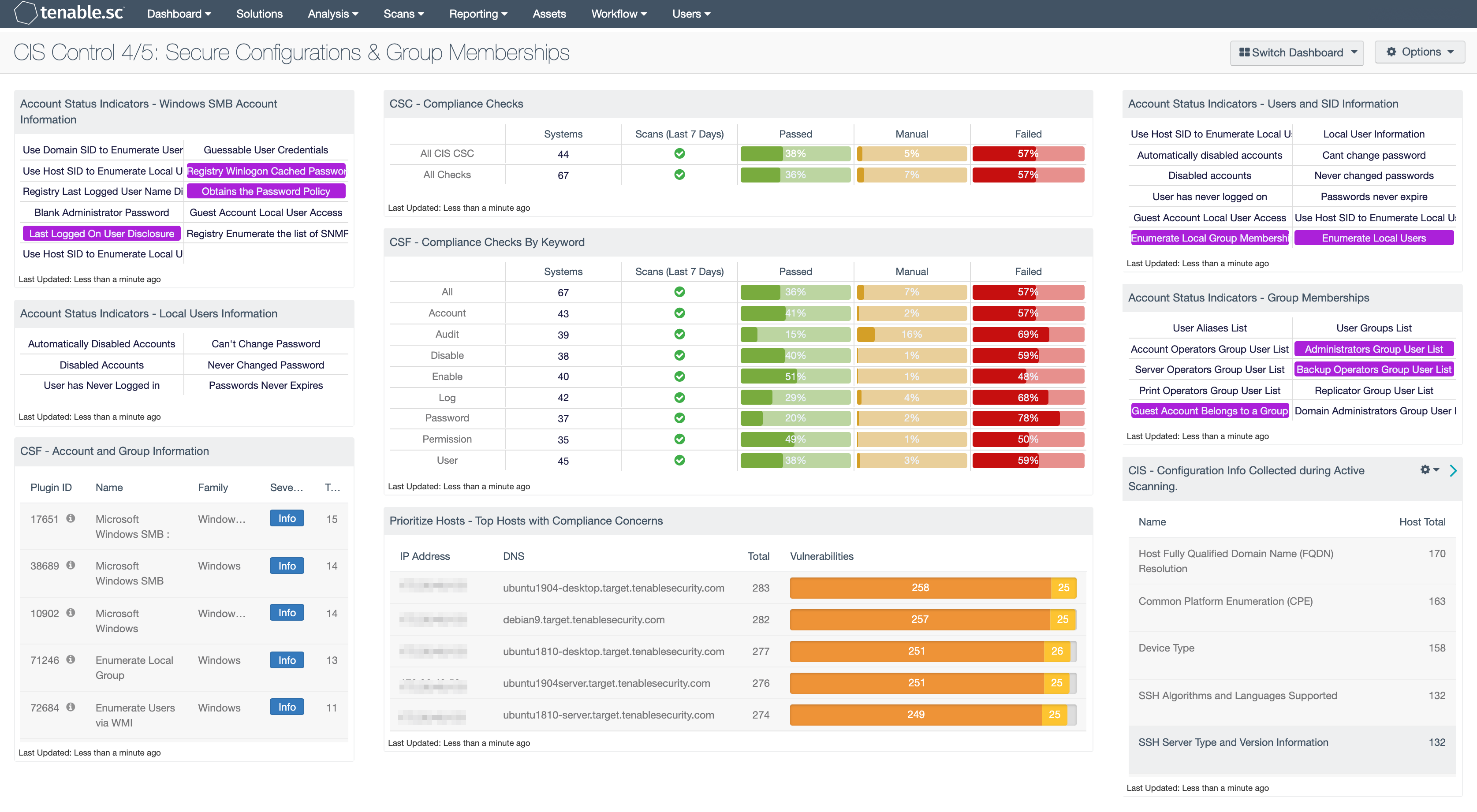
Account Status Indicators - Windows SMB Account Information: This component provides indicators for several Microsoft Windows SMB plugins that focus on user account information.
Account Status Indicators - Local Users Information: This component provides information on user accounts such as disabled accounts, unused accounts, ability to change password, passwords that have never been changed, and if passwords have expired. There are two series of plugins, one looks at the local SAM database, the second looks at Active Directory. Plugins 10895 to 10900 have the prefix Microsoft Windows - Users Information, these enumerate user account information from Active Directory. Plugins 10911 to 10916 have the prefix Microsoft Windows - Local Users Information, and collect data from local SAM database. The matrix cell turns blue when a match of the plugins is found.
CSF - Account and Group Information: This table displays detections of account and group information, such as accounts that have never been logged into, disabled accounts, and group user lists. This information is obtained through Nessus credentialed scans. Most of these detections will contain lists of accounts in their output. The Obtains the Password Policy detection will contain the retrieved password policy in its output. Clicking on the Browse Component Data icon on the component will bring up the vulnerability analysis screen to display the detections and allow further investigation. In the analysis screen, setting the tool to Vulnerability Detail List will display the full details for each detection, including its description and output.
CSC - Compliance Checks: This component presents the results of compliance audits to verify secure system configurations. There are two rows, one for compliance checks specific to the CIS Critical Security Controls and one for all compliance checks. Each row includes the system count, whether scans were performed in the last 7 days, and the percentage of checks that passed, failed, or require manual verification. Passed checks are displayed in green, failed checks are in red, and checks that require manual verification are in orange. Clicking on a highlighted indicator will bring up the vulnerability analysis screen to display details on the compliance checks and allow further investigation. In the vulnerability analysis screen, setting the tool to IP Summary will display the systems on which the compliance checks are present. Setting the tool to Vulnerability Detail List will display the full details on each compliance check, possibly including further information such as the expected and actual policy values and the specific sections of the various standards to which the compliance check relates.
CSF - Compliance Checks By Keyword: This component uses results from the compliance audit to trigger on specific plugin keywords. Each column includes the respective keyword along with the host count, scans performed in the last 7 days, and whether the checks have passed, failed, or require manual verification. Passed checks are green, failed are red, and checks that require manual verification are in orange. This component will allow the analyst to readily identify specific compliance vulnerabilities. The keywords can be modified to suit organizational needs.
Prioritize Hosts - Top Hosts with Compliance Concerns: This table displays the top hosts on the network that have either compliance failures or compliance checks that must be performed manually. The list is sorted so that the host with the worst compliance concerns is at the top. A count of compliance concerns and a bar graph indicating the severity of the concerns are given for each host. Use this table to determine the hosts most out of compliance on the network.
Account Status Indicators - Users and SID Information: This component provides easy access to several plugins used to collect information about user accounts and security identifiers (SID).
Account Status Indicators - Group Memberships: There are several default groups such as the administrators, server operators, account operators, backup operators, print operators, and replicator.
CIS - Configuration Info Collected during Active Scanning: This component is a summary of informational plugins that assist with configuration verification. By excluding port scan plugins, and other plugins related to services, the Vulnerability Summary tool provides a list of all other informational plugins. These plugins contain several system configuration attributes that are useful in assessing the configuration or detecting misconfigurations.