Proactive protection built for federal cybersecurity risk
Tenable’s FedRAMP authorized solutions measure, prioritize and eradicate cyber risk- across IT infrastructure, cloud environments, identities, critical infrastructure and everywhere in between.

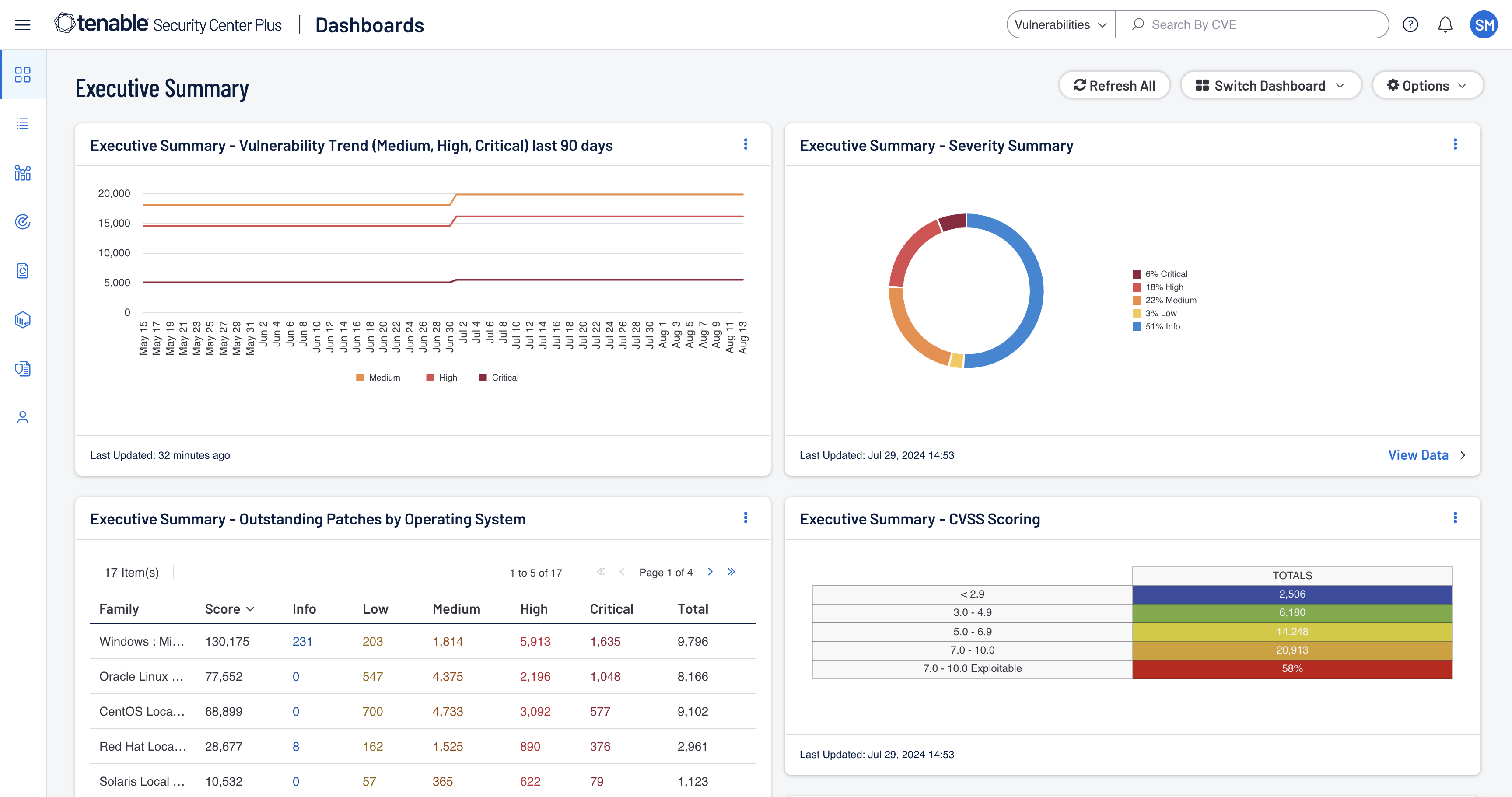
Tenable One and Tenable Cloud Security are now FedRAMP Authorized
Unify security visibility, insight and action across the attack surface with our FedRAMP moderate authorized cyber risk solutions.

Unified protection for mission-critical systems
Tenable One FedRAMP replaces siloed tools with a single, unified platform—cutting costs, increasing efficiency, and delivering clear, risk-based insights. Simplify operations and secure the mission with streamlined protection for your most vital systems.
Discovery that delivers on Zero Trust and executive mandates
Identify and assess every asset across IT, OT, cloud, and identity systems—supporting EO 14028, Zero Trust architecture, and CDM requirements—so you can eliminate blind spots and stop threats before they spread.
Read the eBookSafeguard critical infrastructure with unified IT/OT security
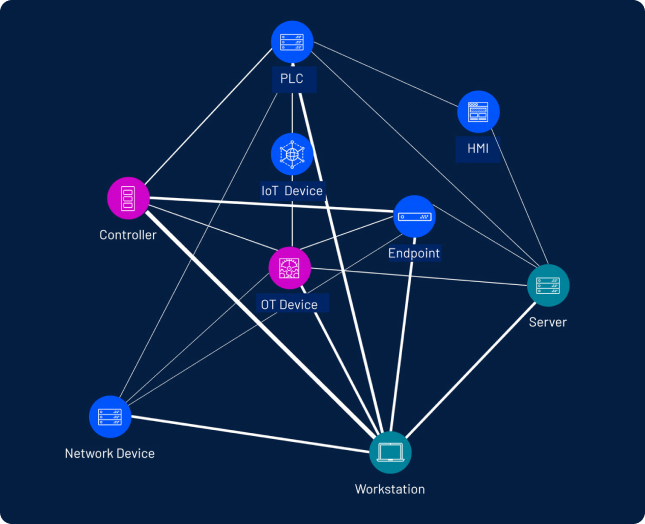
Legacy OT systems are now connected—but rarely secure. Tenable’s unified IT/OT platform helps federal agencies close visibility gaps, ensure compliance with federal mandates, and maintain the safety, resilience, and availability of critical infrastructure.
Download the white paper View the infographicCloud security for the federal government
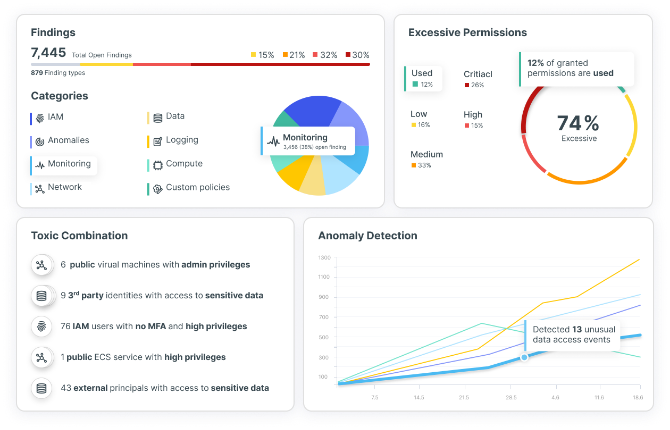
From development to runtime, Tenable Cloud Security FedRAMP continuously analyzes your cloud resources to find the most important risks, spot unknown threats and deliver actionable insight within minutes.
View the web pageStop identity-based attacks before they threaten the mission
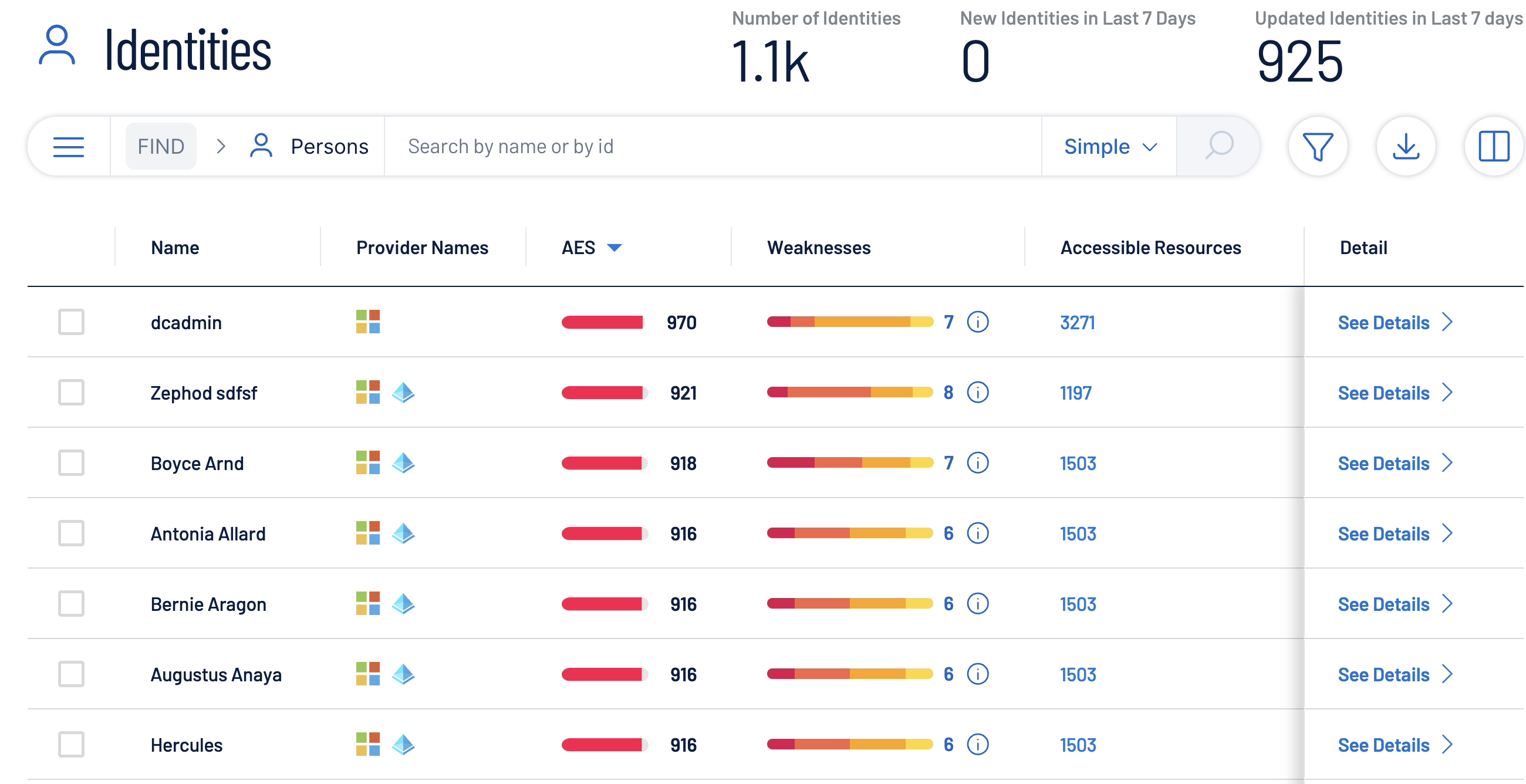
Federal agencies face rising risks from compromised credentials and insider threats, making identity security key to Zero Trust. Tenable One FedRAMP analyzes identity weaknesses and risky permissions so you can prevent attacks before they occur and maintain mission integrity.
Tenable Enclave Security
Purpose-build for the most secure federal environments
Built for classified, air-gapped, and FedRAMP High/IL5 environments, Tenable Enclave Security delivers scalable vulnerability management and container image scanning—purpose-built for isolated, mission-critical systems.
Department of Defense
selected platform
Tenable was selected by DISA to power the Assured Compliance Assessment Solution (ACAS) program, protecting all DoD networks with vulnerability assessment and management, contextual insight, risk assessment and configuration and compliance auditing.
View the solution overview
Federal agency trusted partner
Tenable has a deep understanding of federal government needs and a history of transforming networks and reducing risk to federal agencies.
Industry leader in vulnerability research
Threat intelligence, data science insights, alerts and security advisories from the Tenable Research team integrated into all Tenable products.
Federal agency custom built templates
Generate preconfigured reports to prove compliance with federally mandated regulations and policies.
Accelerate
Zero Trust
Get visibility and assess risk across the five pillars of the Zero Trust Maturity Model.
Meet compliance mandates
Adhere to strict compliance mandates including Executive Orders, CISA Binding Operational Directives, NIST guidelines and more.
Related products
Related resources
See Tenable in action
Want to see how Tenable can help your team expose and close the priority cyber weaknesses that put your business at risk?
Complete this form for more information.
- Tenable Enclave Security
- Tenable Vulnerability Management
- Tenable Web App Scanning