Aplique privilégios mínimos a nuvem. Ajuste as permissões de forma adequada em escala.
Reduza os privilégios permanentes excessivos, que viabilizam a perda de dados e o movimento lateral silenciosos, e possibilite a aplicação do privilégio mínimo com o Tenable Cloud Security. Analise padrões de acesso, sinalize perfis superprivilegiados e automatize o acesso Just-In-Time sem atrasar o desenvolvimento de código.
A segurança deve seguir o ciclo de vida de identidade
Mude do acesso permanente para permissões Just-In-Time.
Gerencie a governança de identidade com o Tenable Cloud Security
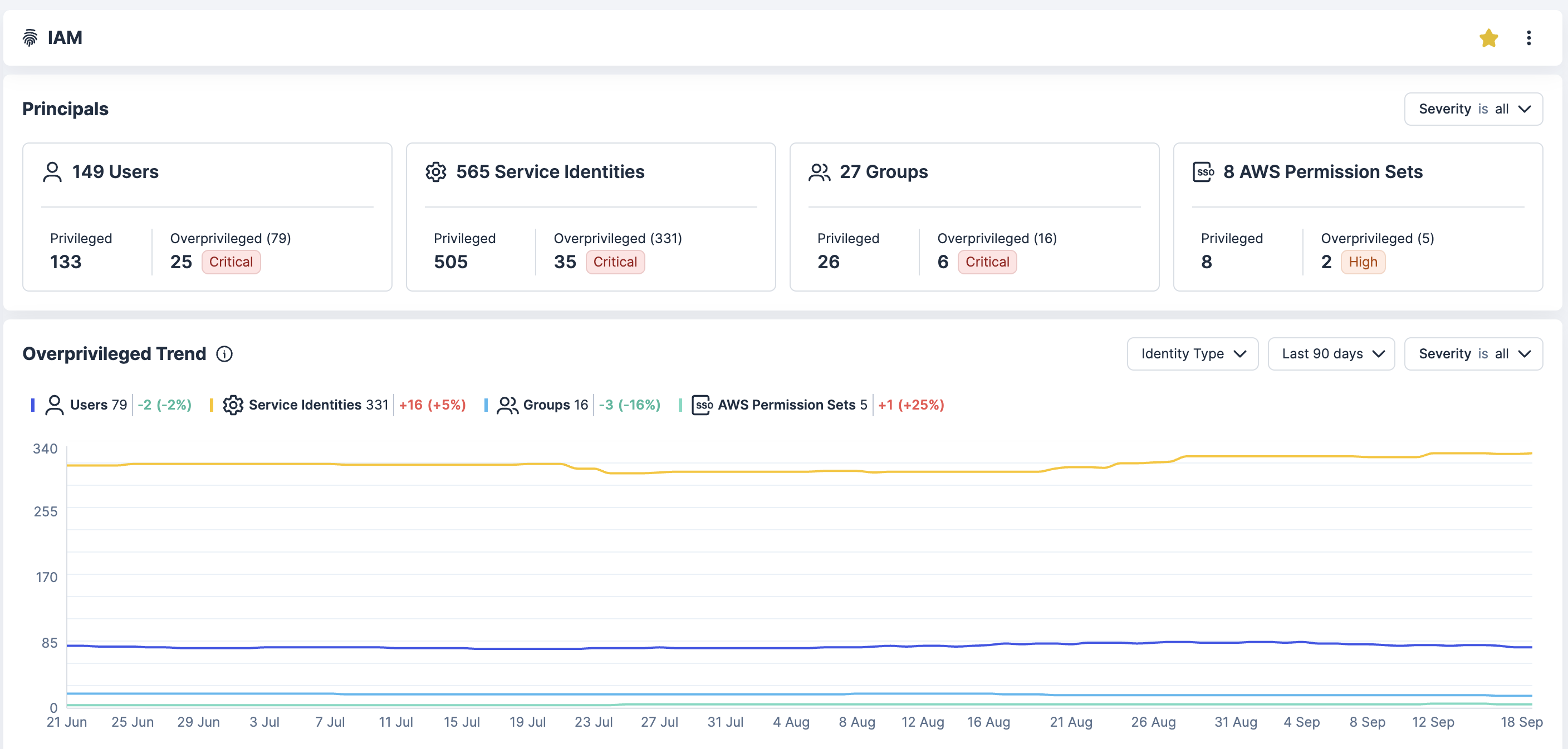
Reduza permissões excessivas na nuvem, uma das grandes causas de violações e não aprovação em auditorias. Reduza o raio de explosão de identidade com visibilidade, automação e aplicação de políticas alinhadas às práticas recomendadas de privilégios mínimos.
Descubra identidades e direitos
Obtenha visibilidade total de todas as identidades na AWS, Azure, GCP e Kubernetes, incluindo usuários humanos, contas de serviço e integrações de terceiros. Detecte contas órfãs, perfis não utilizados e direitos excessivos.
Analise risco proveniente de privilégios
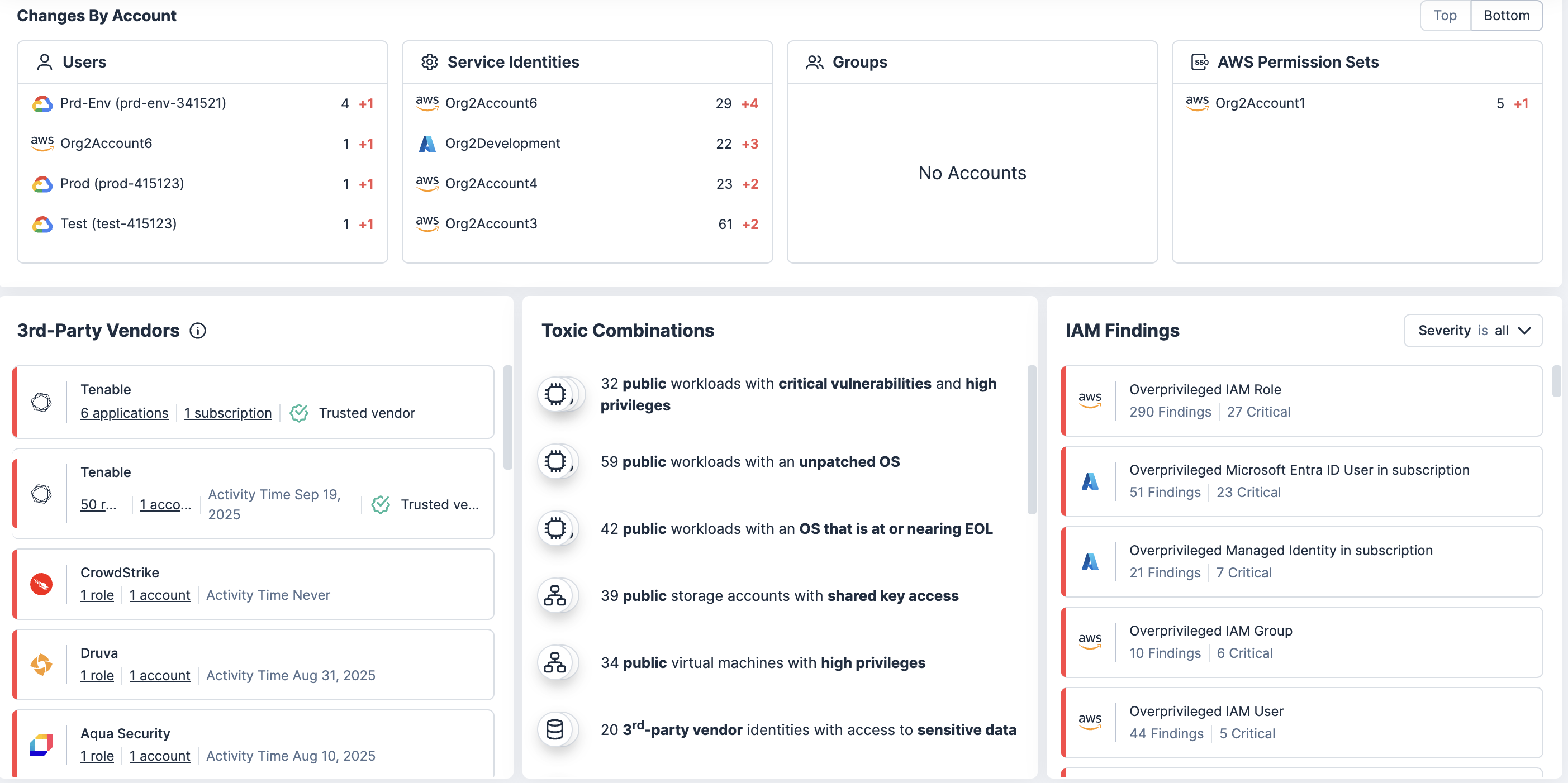
Analise políticas, associações de grupos e suposições de perfis para descobrir riscos de escalonamento de privilégios e oportunidades de movimentação lateral. Esse contexto ajuda suas equipes a eliminar vias de alto risco.
Obtenha priorização e correlação contextual
Correlacione permissões excessivas com vulnerabilidades, configurações incorretas e dados confidenciais para ver onde o uso indevido de privilégios pode ter o maior impacto.
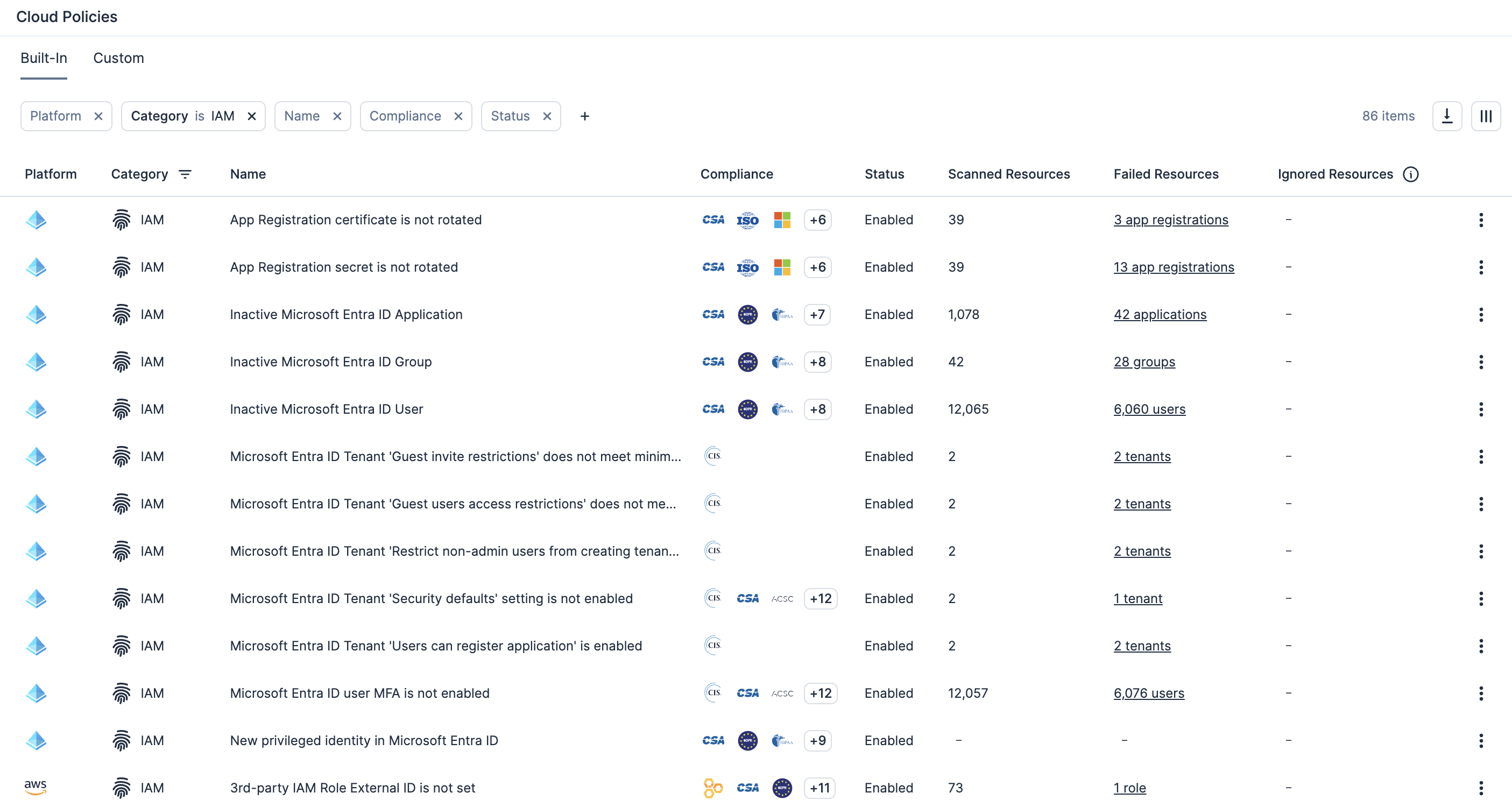
Aplique políticas personalizadas e correção automatizada
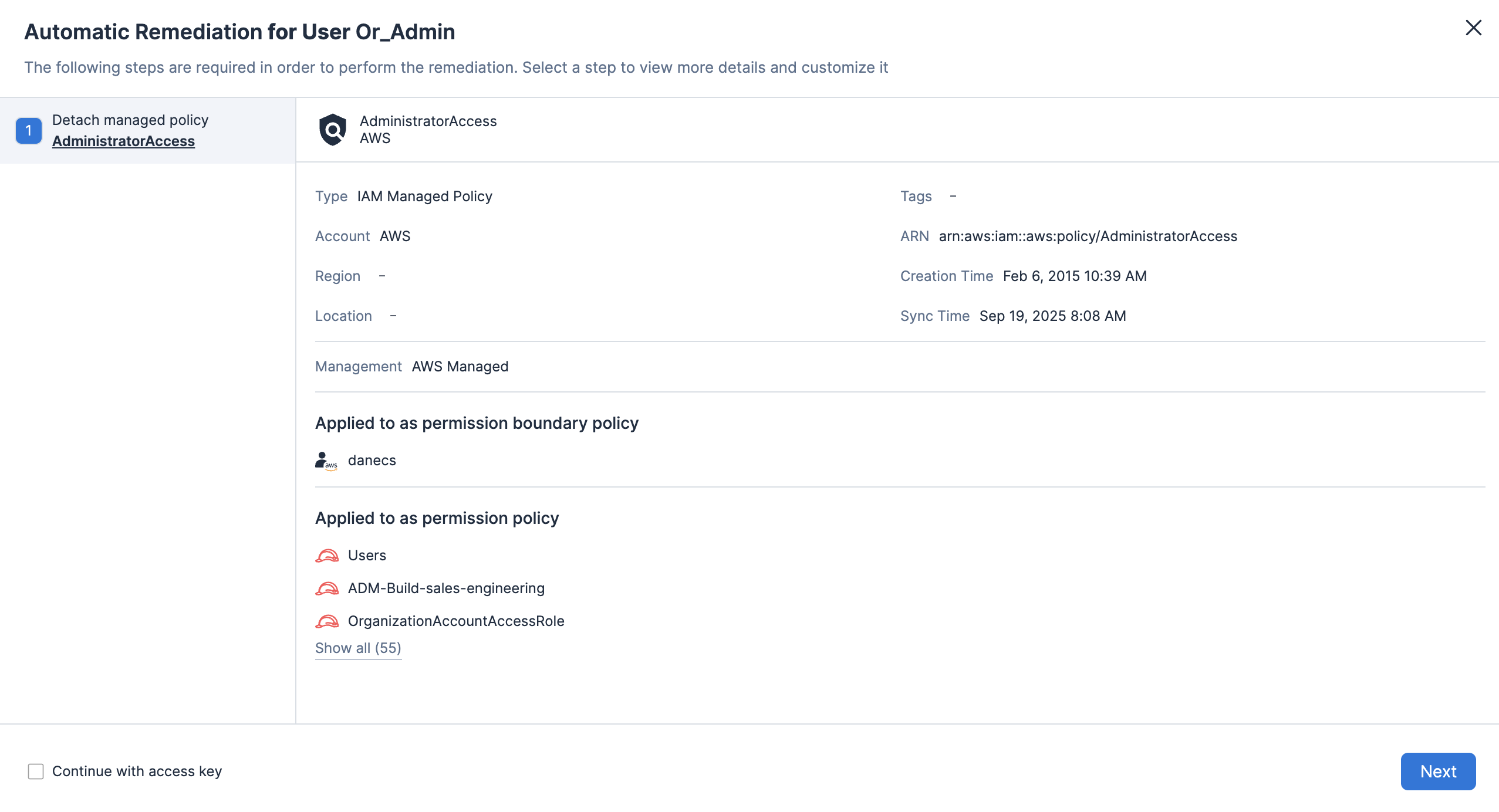
Habilite a definição de política personalizada para detectar permissões excessivas ou configurações arriscadas em recursos e acionar automaticamente fluxos de trabalho de correção.
Integre o CIEM ao Tenable One
Aplique continuamente o privilégio mínimo com o gerenciamento de direitos da infraestrutura de nuvem (CIEM) para garantir que as permissões sejam suficientes, na hora certa e nunca excessivas.
Saiba mais sobre o Tenable Cloud Security
O uso da automação [do Tenable Cloud Security] nos permitiu eliminar processos manuais exaustivos e fazer em minutos o que dois ou três profissionais de segurança levariam meses para conseguir.
- Tenable Cloud Security