Scanning and Patch Auditing VMware Using Nessus
The Revolution Will Be Virtualized
I've worked in IT since my first computer programming job while still in college. I've visited several data centers and server rooms over the years, and I agree with the statement, "If you've seen one data center, you've seen them all." However, I've noticed a significant shift in the last several years – more and more data centers are virtual. This translates to smaller server rooms, less racks, and less servers generating heat and making freight train-like sounds with their cooling fans. Even in my own home computer lab, I use virtualization. In fact, my laptop is a traveling data center, housing at least half a dozen or more virtual machines for various purposes (penetration testing, demonstrations for presentations, and purpose-built virtual machines "just because I needed it one day").
Of course, virtual machines (VMs) are essentially the same as real machines, but they present some unique management and security challenges:
- The host computer, such as a laptop running VMware Fusion or Workstation, has additional software running that could contain vulnerabilities.
- We now have to worry about attackers "jumping" from guest-to-guest and from guest-to-host with VMware escape attacks.
- Administrators can more easily create additional servers. With just a few clicks, you can have another copy of your DNS server, leading to VM sprawl.
- The software used to run and maintain your virtualization environment must be protected from attacks, otherwise your entire infrastructure could be compromised.
- vSphere ESX - "In the original vSphere ESX architecture, the virtualization kernel (referred to as the VMkernel) was augmented with a management partition known as the console operating system (COS or service console)."
- vSphere ESXi - "In the new vSphere ESXi architecture, the COS has been removed and all of the VMware agents run directly on the VMkernel. Infrastructure services are provided natively through modules included with the VMkernel."
- vCenter - "VMware vCenter Server provides a centralized and extensible platform for managing virtual infrastructure. VMware vCenter Server, formerly VMware vCenter, manages VMware vSphere environments allowing IT administrators simple and automated control over the virtual environment to deliver infrastructure with confidence."
Network-based Vulnerability Scanning for VMware
The first step is determining how many VMware ESX/ESXi/vCenter servers are on the network and where they’re located. Running a Nessus vulnerability scan without credentials allows you to identify the servers involved in your virtualization infrastructure. Hopefully there are no surprises when you run this scan! Once my scan was completed (a generic network-based scan with all plugins enabled), I created a filter to search for only VMware-specific results:
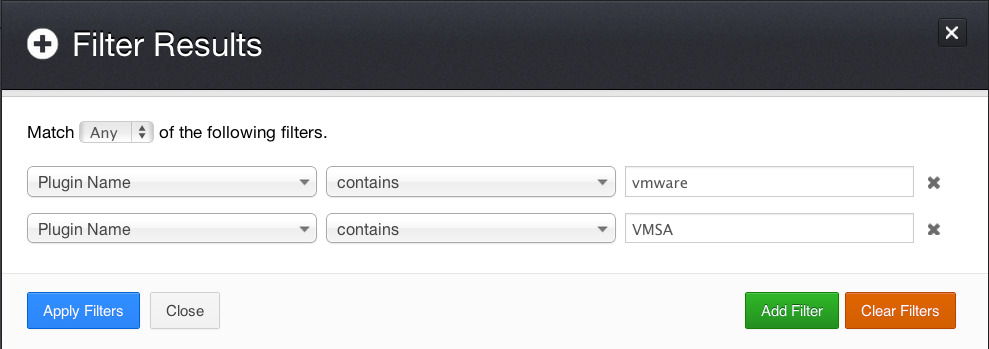
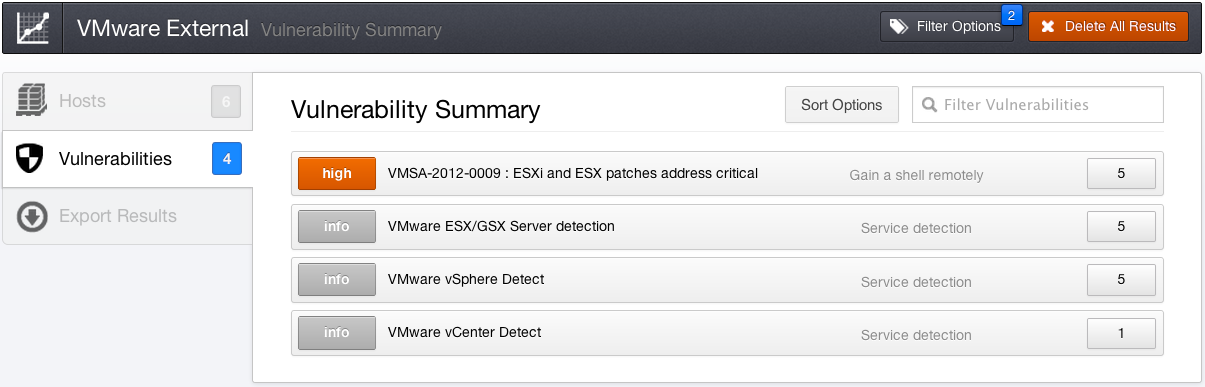
Not only did Nessus detect the virtualization servers, but it also identified vulnerabilities using network-based vulnerability checks:
Configuring VMware Patch Auditing
The next step, once the virtualization platforms have been identified, is to scan them using credentials. This allows Nessus to log in via the VMware SOAP API to perform patch auditing and pull information about hosted VMs.
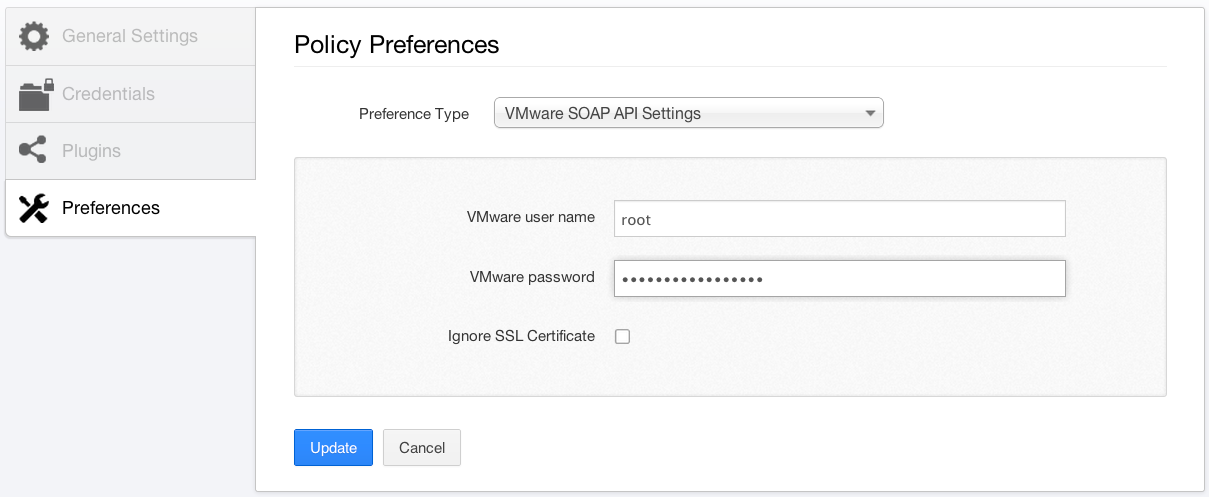
If you have VMware vCenter servers on the network, you can configure credentials for them as well. The preference screen looks nearly identical to the one above and can be found in "Preferences" -> "VMware vCenter SOAP API Settings." You must enter the hostname or IP address of your vCenter server, along with the username and password.
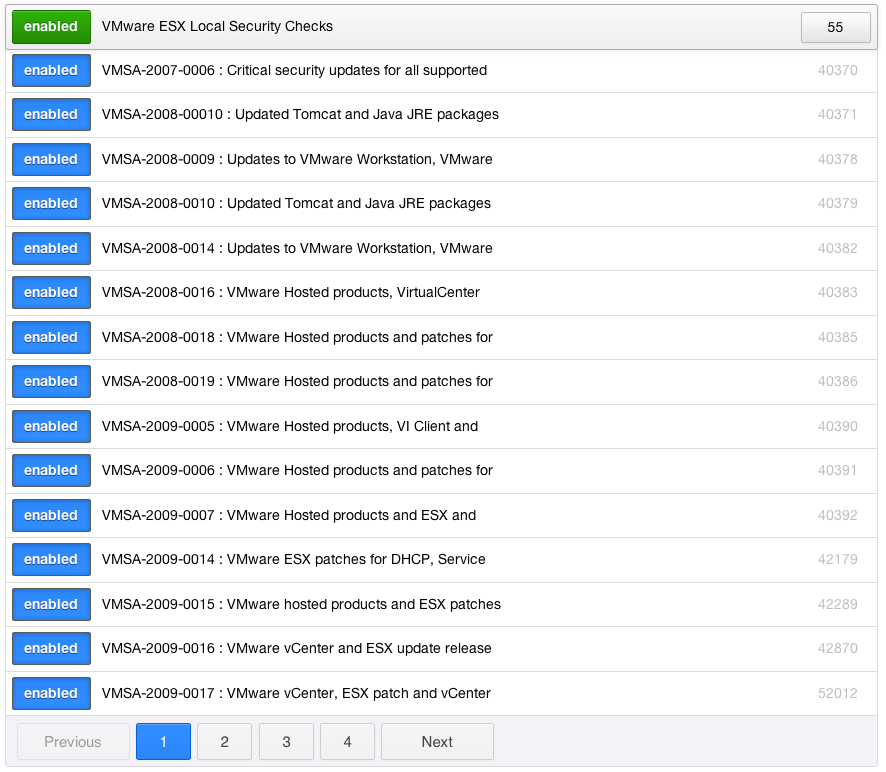
In order to audit the patches of ESX, ESXi, or vCenter, you must also enable the "VMware ESX Local Security Checks" plugin family as shown below:
The Results
Once the scan has completed, using the provided credentials, Nessus will report the missing patches for each VMware ESX/ESXi/vCenter server that was scanned. Below, Nessus found an ESX server running version 4.1 that's missing a critical-severity-level patch:
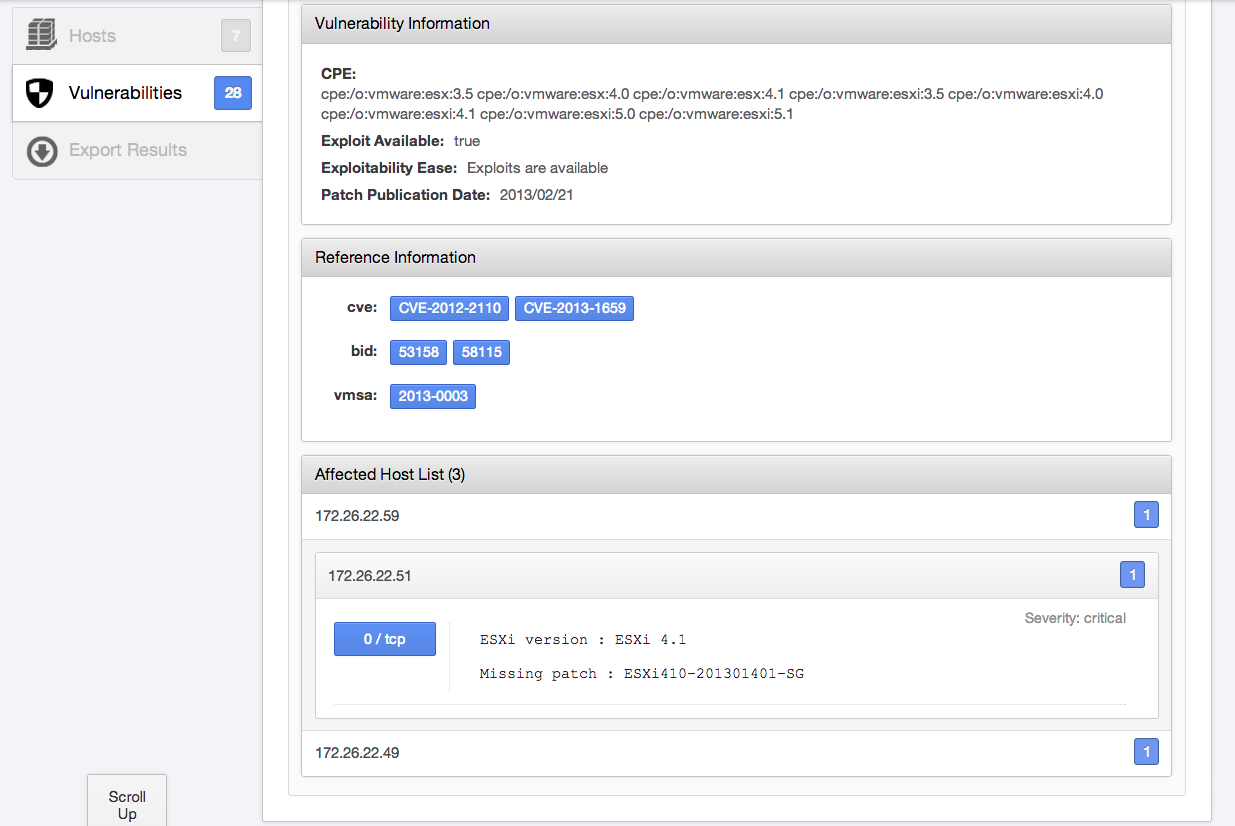
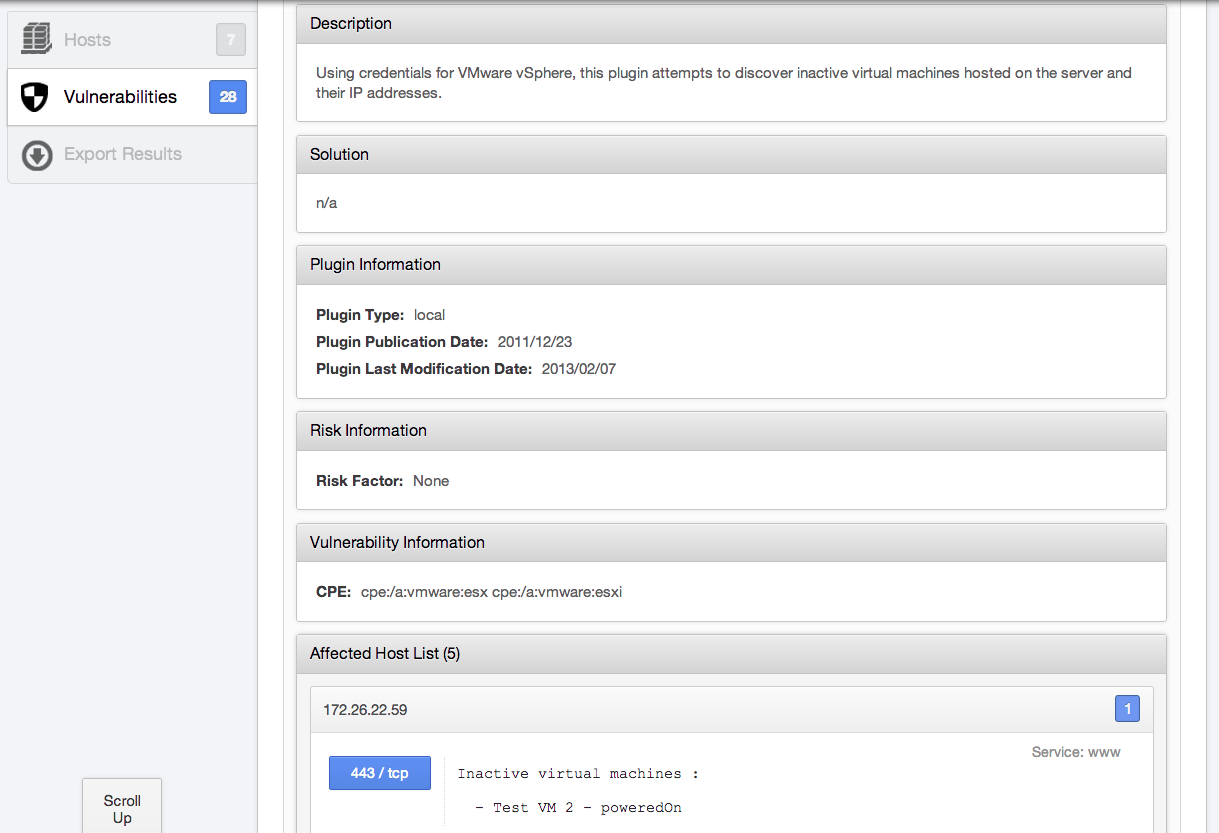
Using the SOAP API, Nessus can log in and pull information from ESX/ESXi servers, such as active and inactive VMs on the host. This information is extremely useful to continually audit your environment and keep tabs on the number of VMs. Acting on this information can help prevent VM sprawl:
Conclusion
Getting a handle on your virtualization environments can be challenging. The ease with which new VMs can be created and powered on produces a moving target that can be difficult to manage. Vulnerabilities can affect the entire platform, potentially providing an attacker with access to sensitive systems by successfully attacking only one ESX/vCenter target.
Tenable can help. Use Nessus to detect new instances of VMware virtualization platforms in your environment using network-based checks. For the VMs you already manage, Nessus allows you to constantly audit them for new vulnerabilities, assure the patches you've applied are intact, and gather useful information for managing your environment. In addition to vulnerability scanning and patch auditing, you can also perform configuration auditing, ensuring that your virtualization platforms are hardened to your specifications, and compliance auditing.
- Nessus
- Patch Auditing

