Microsoft’s May 2023 Patch Tuesday Addresses 38 CVEs (CVE-2023-29336)

Microsoft addresses 38 CVEs including three zero-day vulnerabilities, two of which were exploited in the wild.
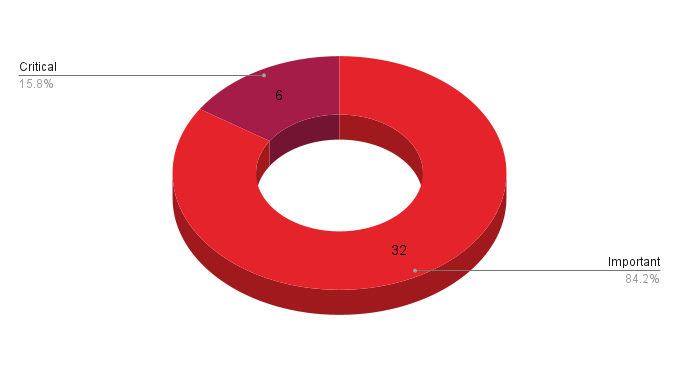
- 6Critical
- 32Important
- 0Moderate
- 0Low
Microsoft patched 38 CVEs in its May 2023 Patch Tuesday Release, with six rated as critical and 32 rated as important.
This month’s update includes patches for:
- Microsoft Bluetooth Driver
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft Office Word
- Microsoft Teams
- Microsoft Windows Codecs Library
- Reliable Multicast Transport Driver (RMCAST)
- Remote Desktop Client
- SysInternals
- Visual Studio Code
- Windows Backup Engine
- Windows Installer
- Windows iSCSI Target Service
- Windows Kernel
- Windows LDAP - Lightweight Directory Access Protocol
- Windows MSHTML Platform
- Windows Network File System
- Windows NFS Portmapper
- Windows NTLM
- Windows OLE
- Windows RDP Client
- Windows Remote Procedure Call Runtime
- Windows Secure Boot
- Windows Secure Socket Tunneling Protocol (SSTP)
- Windows SMB
- Windows Win32K
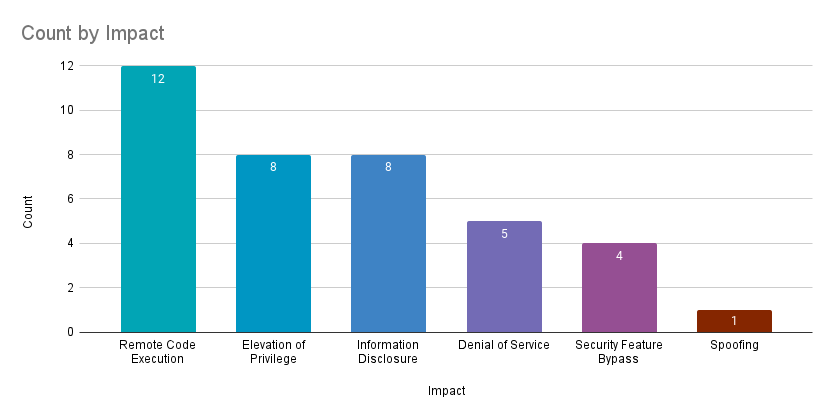
Remote code execution (RCE) vulnerabilities accounted for 31.6% of the vulnerabilities patched this month, followed by both elevation of privilege (EoP) and information disclosure vulnerabilities at 21.1%.
CVE-2023-29336 | Win32k Elevation of Privilege Vulnerability
CVE-2023-29336 is an EoP vulnerability in Microsoft’s Win32k, a core kernel-side driver used in Windows. This vulnerability received a CVSSv3 score of 7.8 and was exploited in the wild as a zero-day. Exploitation of this vulnerability would allow an attacker to gain SYSTEM level privileges on an affected host. Over the last few years, we have seen multiple Win32k EoP zero days exploited in the wild. In the January 2022 Patch Tuesday release, Microsoft patched CVE-2022-21882. CVE-2022-21882 was reportedly a patch bypass for CVE-2021-1732, another Win32k EoP zero day vulnerability from February 2021. In October 2021, Microsoft patched CVE-2021-40449, another Win32k EoP zero day linked to a remote access trojan known as MysterySnail and was reportedly a patch bypass for CVE-2016-3309. It is unclear if CVE-2023-29336 is also a patch bypass.
CVE-2023-24932 | Secure Boot Security Feature Bypass Vulnerability
CVE-2023-24932 is a security feature bypass vulnerability in Secure Boot in Windows operating systems, which allows for running of untrusted software during the boot up process. It was publicly disclosed and exploited in the wild as a zero-day prior to a patch being available. The flaw was given a CVSSv3 score of 6.7. Exploitation of this vulnerability requires an attacker to have administrative rights or physical access to the vulnerable device, so Microsoft has rated this as “Exploitation Less Likely” according to Microsoft’s Exploitability Index.
According to the advisory, additional steps must be taken to mitigate this vulnerability. These steps are outlined in KB5025885 which specifies that the May 9, 2023 Windows security updates must be installed first. The KB article notes that this update and the associated mitigation steps are necessary due to the publicly disclosed bypass being used by the BlackLotus UEFI bootkit. More information can be found in a blog post by ESET who are also credited with disclosing CVE-2023-24932 to Microsoft alongside Tomer Sne-or with SentinelOne.
CVE-2023-24932 is the fourth security feature bypass vulnerability disclosed in 2023 in either Windows Boot Manager or Secure Boot. In April’s Patch Tuesday release, Microsoft addressed CVE-2023-28269 and CVE-2023-28249, and in January’s Patch Tuesday release, Microsoft addressed CVE-2023-21560.
CVE-2023-29325 | Windows OLE Remote Code Execution Vulnerability
CVE-2023-29325 is a RCE in the Windows Object Linking and Embedding (OLE) mechanism of Windows operating systems that was publicly disclosed and given a CVSSv3 score of 8.1. Windows OLE is a technology that allows the creation of documents that contain objects from several applications. The vulnerability lies in the processing of RTF documents and emails. Microsoft said that the Preview Pane feature in Microsoft Outlook and Office is a vector for exploitation. An unauthenticated, remote attacker can exploit this vulnerability by sending a specially crafted document to a vulnerable system. However, the vulnerability has been given a high complexity as successful exploitation requires the attacker to win a race condition and the target to be prepared for exploitation.
As well as the patch released in this month’s update, Microsoft has provided mitigation advice to prevent users from opening RTF documents or emails in Outlook and Office to reduce the risk of exploitation where immediate patching is not possible.
CVE-2023-24941 | Windows Network File System Remote Code Execution Vulnerability
CVE-2023-24941 is a critical RCE vulnerability affecting supported versions of Windows Server that was given a CVSSv3 score of 9.8. The affected component is the Network File System (NFS) service, which is used for file sharing between Unix and Windows Server systems. Specifically the vulnerability affects NFSV4.1, but not NFSV2.0 or NFSV3.0. CVE-2023-24941 can be exploited by a remote, unauthenticated attacker sending a malicious call to a vulnerable server.
Microsoft provided mitigation guidance for organizations where immediate patching is not possible, which involves disabling NFSV4.1. However, this mitigation should not be applied if the server has not applied the May 2022 patch, as that release addressed a similar vulnerability, CVE-2022-26937, in NFSV2 and NFSV3.
Windows 10 20H2 End Of Life
Microsoft announced that Windows 10 20H2 has reached its end of life for Enterprise, Education, IoT Enterprise, and Enterprise multi-session editions. This means that users of these versions of Windows 10 20H2 will no longer receive security updates and should upgrade as soon as possible. Plugin ID 161921 can be used to identify hosts that have unsupported installations of Windows 10 version 20H2.
Next month on June 13 (also the June Patch Tuesday release), Windows 10 21H2 will reach end of life for Home, Pro, Pro Education and Pro for Workstations editions. For these affected systems, we recommend planning your migration as soon as possible to supported versions of Windows.
Tenable Solutions
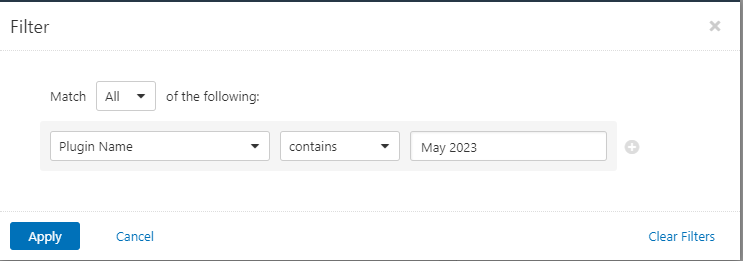
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains May 2023.
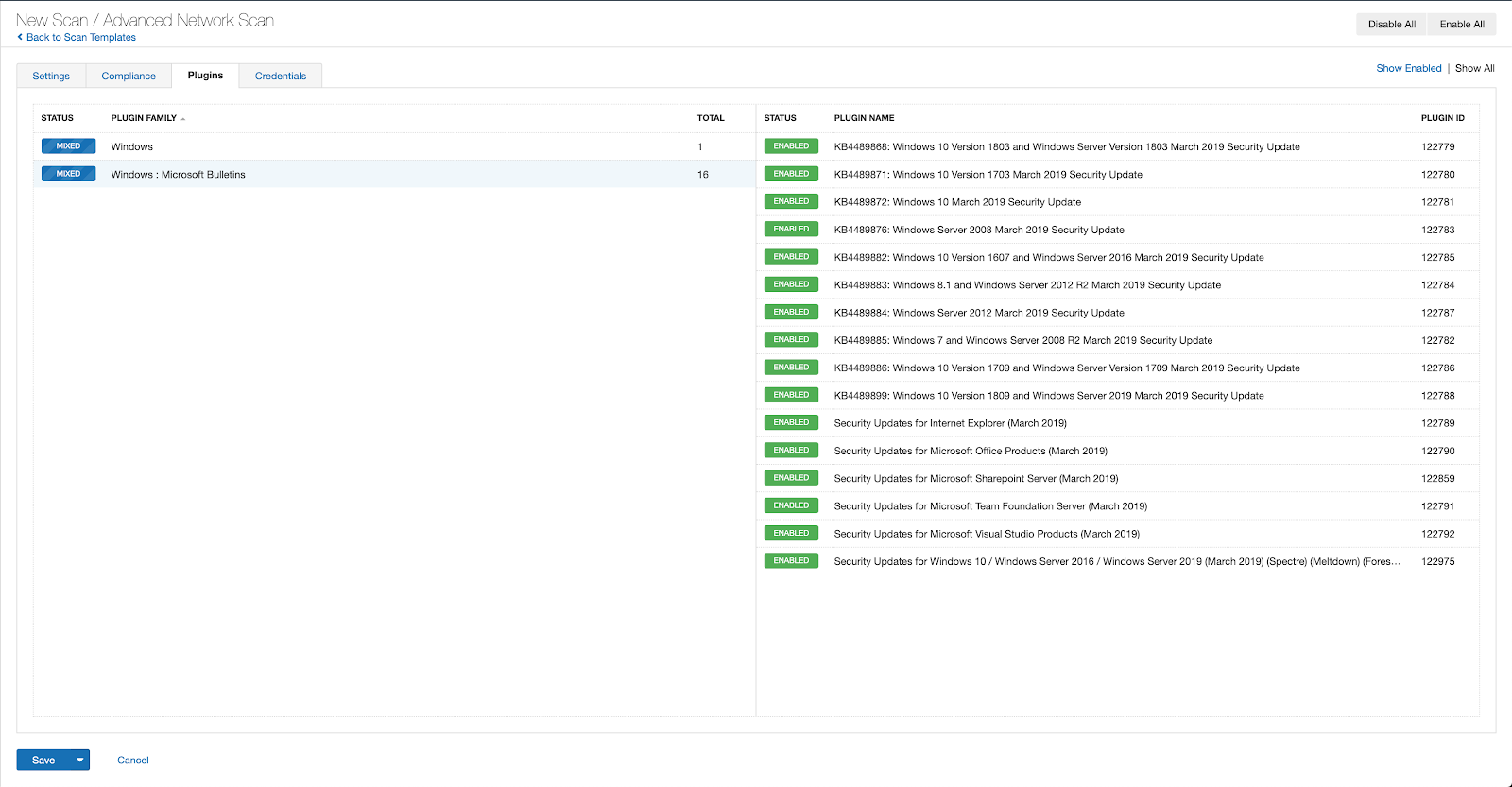
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable Vulnerability Management (formerly Tenable.io):
A list of all the plugins released for Tenable’s May 2023 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's May 2023 Security Updates
- Tenable plugins for Microsoft May 2023 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management


