Microsoft’s September 2021 Patch Tuesday Addresses 60 CVEs (CVE-2021-40444)

Microsoft addresses 60 CVEs in its September 2021 Patch Tuesday release, along with patches for a critical vulnerability in its MSHTML (Trident) engine that was first disclosed in an out-of-band advisory on September 7.
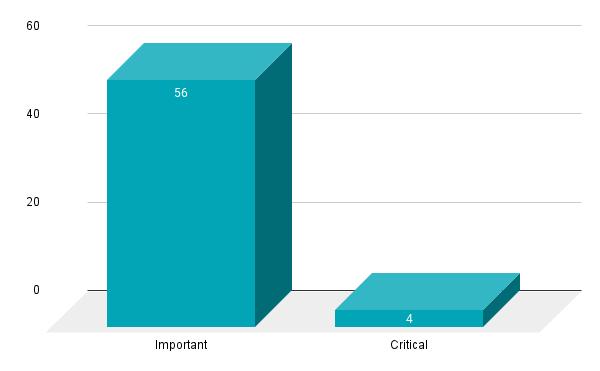
- 4Critical
- 56Important
- 0Moderate
- 0Low
Microsoft patched 60 CVEs in the September 2021 Patch Tuesday release, including four CVEs rated as critical and 56 rated as important. This is the seventh time in 2021 that Microsoft has patched fewer than 100 vulnerabilities in a Patch Tuesday release, a stark contrast to 2020, which featured eight months where over 100 CVEs were patched.
This month's Patch Tuesday release includes fixes for:
- Azure Open Management Infrastructure
- Azure Sphere
- Dynamics Business Central Control
- Microsoft Accessibility Insights for Android
- Microsoft Edge (Chromium-based)
- Microsoft Edge for Android
- Microsoft MPEG-2 Video Extension
- Microsoft Office
- Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Office Word
- Microsoft Windows Codecs Library
- Microsoft Windows DNS
- Visual Studio
- Windows Ancillary Function Driver for WinSock
- Windows Authenticode
- Windows Bind Filter Driver
- Windows BitLocker
- Windows Common Log File System Driver
- Windows Event Tracing
- Windows Installer
- Windows Kernel
- Windows Key Storage Provider
- Windows MSHTML Platform
- Windows Print Spooler Components
- Windows Redirected Drive Buffering
- Windows Scripting
- Windows SMB
- Windows Storage
- Windows Subsystem for Linux
- Windows TDX.sys
- Windows Update
- Windows Win32K
- Windows WLAN Auto Config Service
- Windows WLAN Service.
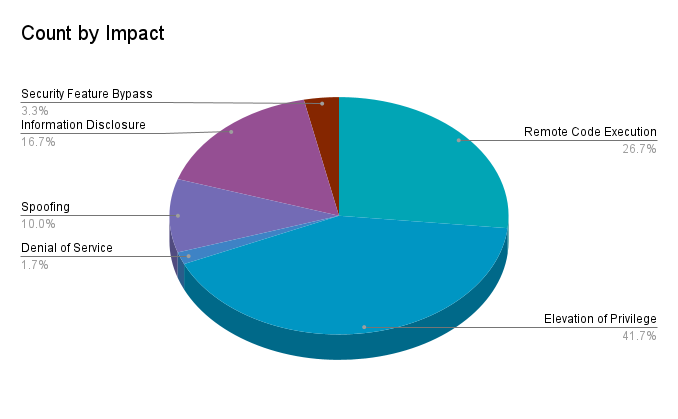
Elevation of privilege (EoP) vulnerabilities accounted for 41.7% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 26.7%.
CVE-2021-40444 | Microsoft MSHTML Remote Code Execution Vulnerability
CVE-2021-40444 is a critical zero-day RCE vulnerability in Microsoft’s MSHTML (Trident) engine that was exploited in the wild in limited, targeted attacks. It was assigned a CVSSv3 score of 8.8. To exploit this vulnerability, an attacker would need to create a specially crafted Microsoft Office document containing a malicious ActiveX control. From there, the attacker would need to use social engineering techniques to convince their target to open the document. Microsoft says the impact of this vulnerability would be more significant in cases where the recipient has administrative privileges.
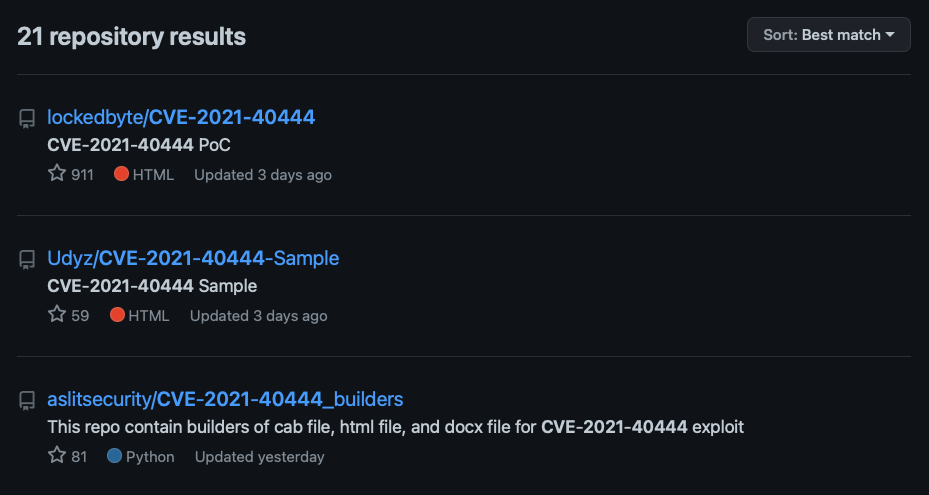
At the time this blog post was published, there were at least 21 repositories on GitHub containing proof-of-concept code for this flaw.
We strongly recommend organizations apply this month’s patches to ensure this vulnerability is addressed, as it won’t be long before other threat actors, including those affiliated with ransomware groups, begin leveraging this flaw as part of their attacks.
CVE-2021-36968 | Windows DNS Elevation of Privilege Vulnerability
CVE-2021-36968 is an EoP vulnerability found in Windows DNS. The vulnerability was assigned a CVSS score of 7.8. While no additional information from Microsoft has been provided, the security advisory makes note that this vulnerability has been publicly disclosed. Exploitation requires local access and a low privileged user account and is less likely to be exploited according to Microsoft’s Exploitability Index.
CVE-2021-38667, CVE-2021-38671 and CVE-2021-40447 | Windows Print Spooler Elevation of Privilege Vulnerability
CVE-2021-38667, CVE-2021-38671 and CVE-2021-40447 are EoP vulnerabilities in Windows Print Spooler. All three vulnerabilities were assigned a CVSSv3 score of 7.8 and are rated Important. Of the three vulnerabilities, CVE-2021-38671 is the only flaw rated as Exploitation More Likely. There has been a flurry of activity surrounding Windows Print Spooler related vulnerabilities, beginning with CVE-2021-1675 in June and CVE-2021-34527, also known as PrintNightmare in July. We published a blog post in August about the seven Print Spooler related vulnerabilities Microsoft published advisories for which included CVE-2021-36958, a zero-day RCE that was patched today. Because of its ubiquity, Print Spooler is a valuable target for attackers, so the fact that we continue to see research in this space shows that there are an untold number of vulnerabilities within Print Spooler.
CVE-2021-36955, CVE-2021-36963 and CVE-2021-38633 | Windows Common Log File System Driver Elevation of Privilege Vulnerability
CVE-2021-36955, CVE-2021-36963 and CVE-2021-38633 are EoP vulnerabilities found in the Windows Common Log File System (CLFS) Driver which would allow a low privileged local attacker to elevate their user account privileges. While Microsoft has not observed exploitation in the wild, they rate these flaws as “Exploitation More Likely.” EoP vulnerabilities are commonly used in malware/ransomware attacks as we’ve observed with CVE-2020-1472, aka Zerologon, one of the Top Five Vulnerabilities of 2020. As such, we strongly recommend prioritizing the installation of these patches.
CVE-2021-36975 and CVE-2021-38639 | Win32k Elevation of Privilege Vulnerability
CVE-2021-36975 and CVE-2021-38639 are EoP vulnerabilities found in Win32k, the kernel-mode subsystem that provides graphical (GUI) content functionality in Windows. With an assigned CVSS score of 7.8 and exploitability rating of “Exploitation More Likely,” attackers are expected to leverage this flaw to elevate account privileges of low privileged local user accounts. As Win32k is a core component of Windows, applying the necessary cumulative patches for your version of Windows is strongly recommended.
Tenable Solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains September 2021.
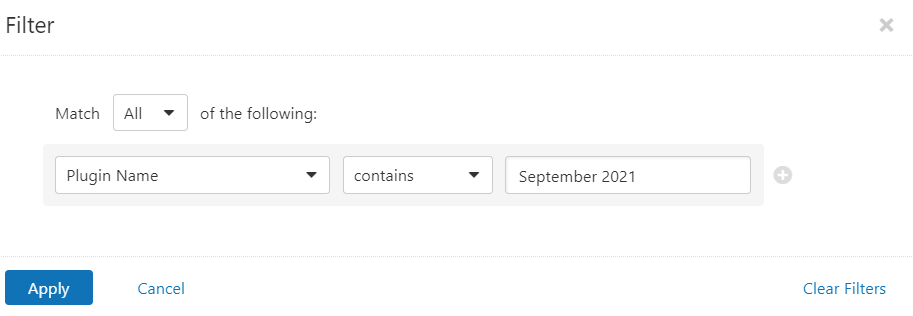
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
A list of all the plugins released for Tenable’s September 2021 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's September 2021 Security Updates
- Tenable plugins for Microsoft September 2021 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

