Microsoft Patch Tuesday 2023 Year in Review

Microsoft addressed over 900 CVEs as part of Patch Tuesday releases in 2023, including over 20 zero-day vulnerabilities.
Background
Microsoft’s Patch Tuesday, a monthly release of software patches for various Microsoft products, celebrated its 20th anniversary in 2023. In 2022, Tenable Research published a blog post discussing Patch Tuesday’s impact on cybersecurity over the years. For 2023, we wanted to continue this lookback with a year in review of Patch Tuesday to surface various trends we observed from our monthly analysis.
Analysis
For 2023, Microsoft patched 909 CVEs, a slight decline of 0.87% from 2022, which saw Microsoft patch 917 CVEs.
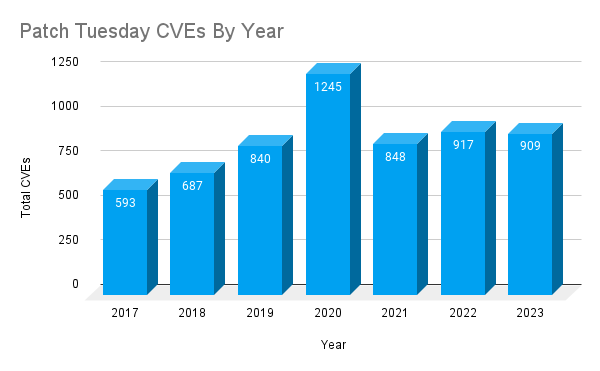
Since 2017, Patch Tuesday releases have experienced an upward trend, peaking in 2020 with 1,245 CVEs patched. Over the last three years, Patch Tuesday has trended down from its peak, leveling off and hovering towards the baseline average, which is 862 CVEs per year.
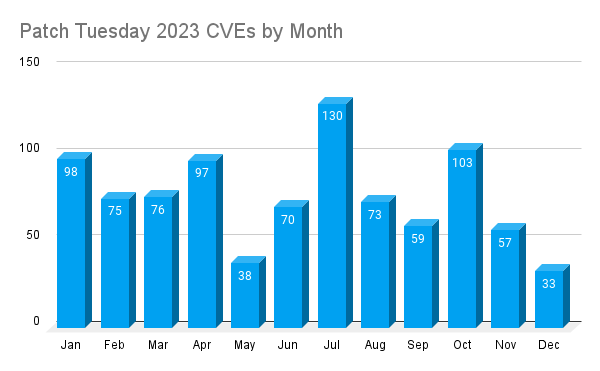
The peak month for Patch Tuesday in 2023 was July, when Microsoft patched 130 CVEs. Only two months saw over 100 CVEs patched (July, October) while there were four months where Microsoft patched fewer than 60 CVEs (May, September, November, December).
Patch Tuesday 2023 by severity
Each month, Microsoft categorizes vulnerabilities into four main severity levels: low, moderate, important and critical.
In 2023, the majority of vulnerabilities were rated as important, accounting for 90% of all CVEs patched, followed by critical at 9.6%. Moderate and low vulnerabilities combined accounted for just 0.4% of all CVEs patched.
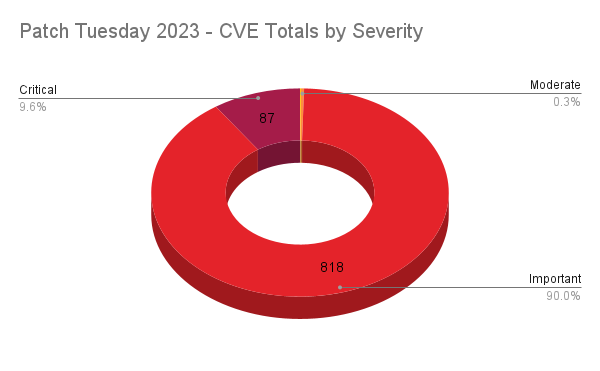
These figures are relatively consistent with 2022 figures, when Microsoft patched 831 important CVEs, which accounted for 90.2% while critical vulnerabilities accounted for 85 CVEs or 9.2%.
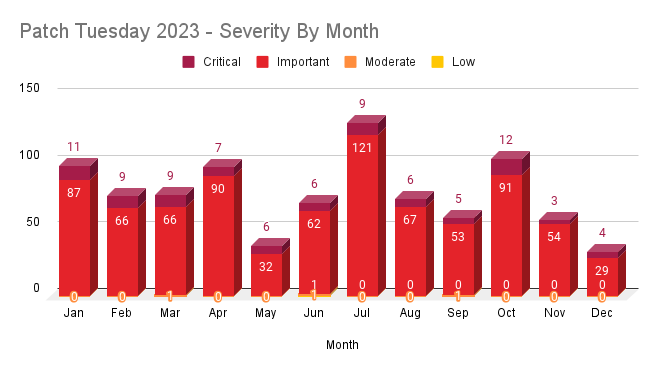
As noted previously, July 2023 was the peak month for patches, with 130 CVEs addressed: nine critical vulnerabilities and 121 important vulnerabilities.
Patch Tuesday 2023 by impact
In addition to severity levels, Microsoft also categorizes vulnerabilities by seven impact levels: remote code execution (RCE), elevation of privilege (EoP), denial of service (DoS), information disclosure, spoofing, security feature bypass and tampering.
In 2023, the majority of vulnerabilities patched by Microsoft fell into the RCE category, accounting for 36%, which was followed by EoP vulnerabilities at 26%. Information Disclosure vulnerabilities accounted for 12.5% of vulnerabilities patched. Despite having a category for it, Microsoft did not label any vulnerabilities as Tampering.
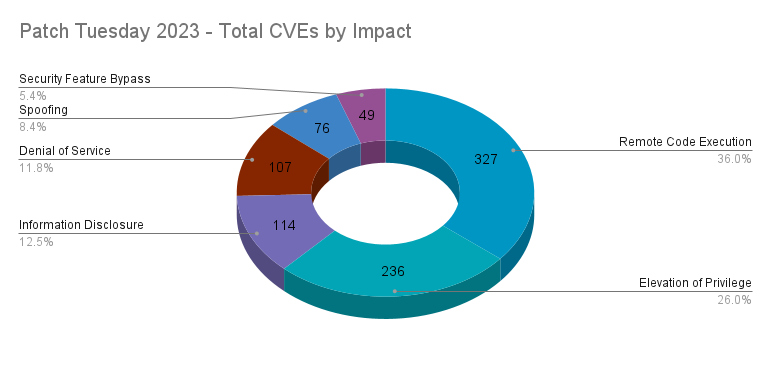
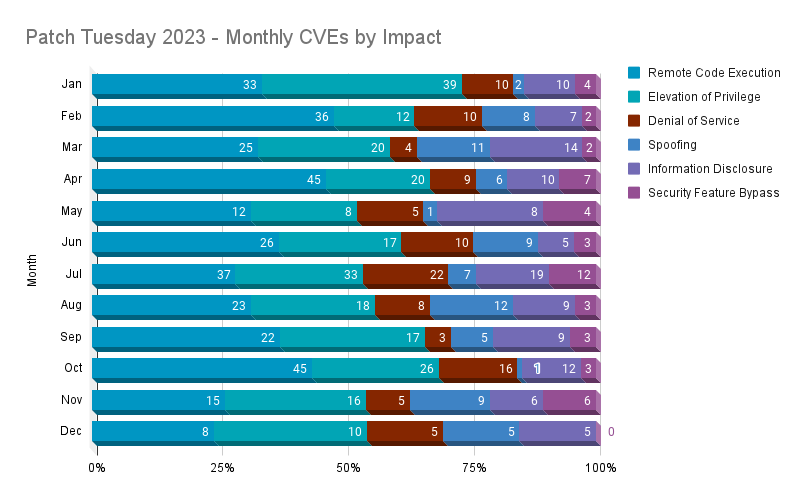
Each month, RCE and EoP vulnerabilities battled for the top spot, as they both combined to account for nearly two-thirds of all vulnerabilities patched in 2023.
Patch Tuesday 2023 zero-day vulnerabilities
When reviewing Patch Tuesday releases, one of the important factors is the presence of zero-day vulnerabilities. Zero-day vulnerabilities are defined as vulnerabilities in software that have been exploited in the wild and/or have been publicly disclosed prior to patches becoming available.
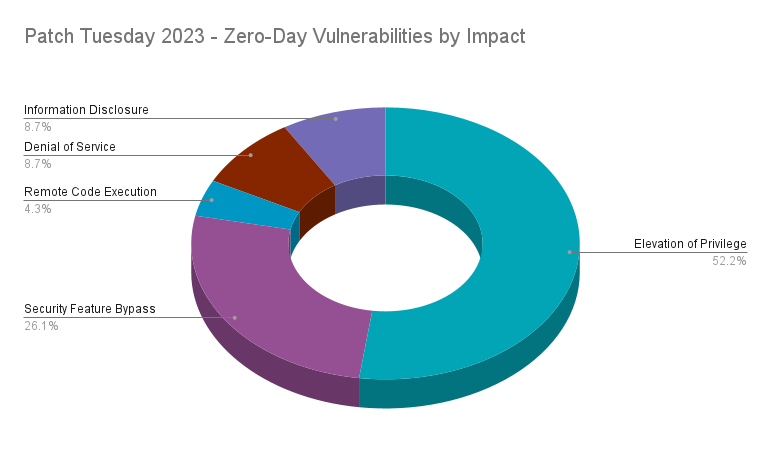
In 2023, Microsoft released patches for 23 zero-day vulnerabilities. For this count, we did not include a Defense In Depth update (ADV230003) from August as it is a fix for a vulnerability disclosed in July 2023, which has already been counted.
Of the 23 zero-day vulnerabilities patched in 2023, over half (52.2%) were EoP flaws. EoP vulnerabilities are often leveraged by advanced persistent threat (APT) actors and by determined cybercriminals seeking to elevate privileges as part of post-compromise activity. Following EoP flaws, security feature bypass vulnerabilities accounted for 26.1% of zero-days in 2023. These two categories combined for over three quarters (78.3%) of all zero-day vulnerabilities in 2023. While RCEs were the most prominent vulnerabilities across Patch Tuesday, they only accounted for 4.3% of zero-day flaws.
Some of the most notable zero-day vulnerabilities disclosed during the Patch Tuesday releases in 2023 include CVE-2023-23397, an EoP vulnerability in Microsoft Outlook that has been exploited by a Russian advanced persistent threat (APT) group referred to as APT28 or Forest Blizzard. Despite being patched in March, researchers at Unit 42 have observed a campaign as recently as October 2023 leveraging this flaw.
At least two of the zero-days were observed being exploited by ransomware groups, including CVE-2023-24880 by the Magniber ransomware group and CVE-2023-28252 by the Nokoyawa ransomware group. CVE-2023-24932 was observed being used in the BlackLotus UEFI bootkit to bypass Secure Boot, while CVE-2023-36884 has been utilized by another Russia-based threat actor referred to as Storm-0978 to distribute the RomCom backdoor. Finally, a vulnerability in the HTTP/2 protocol, CVE-2023-44487, also known as Rapid Reset, was used to conduct distributed denial-of-service (DDoS) attacks from August through October. Details for many of the other zero-days disclosed in 2023 were not made public.
Conclusion
Software releases like Patch Tuesday with an expected cadence, such as those that happen each and every month, were conceptualized to help defenders prepare for the tranche of security patches. Despite this release cadence, known vulnerabilities continue to haunt organizations for months to years, which means there is still more work to be done.
Looking back at Patch Tuesday for 2023, we see that the volume of CVEs patched were in-line with 2022 numbers and have remained far off from the peak in 2020. Despite the overall numbers, Patch Tuesday in 2023 was still eventful due to the presence of several zero-day flaws and a number of critical vulnerabilities across a variety of Microsoft products.
Each and every month, Tenable Research publishes a Patch Tuesday blog to highlight some of the noteworthy vulnerabilities addressed. Follow the Tenable blog for more information as we move into 2024.
Get more information
- Tenable Blog: Patch Tuesday's Impact on Cybersecurity Over The Years
- Microsoft Blog on Celebrating 20 Years of Patch Tuesday
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management


