IPv6 Scanning with Nessus and PVS
While many organizations, service providers and manufacturers have made the switch to IPv6, this might be the year that everyone who’s been dragging their heels has to as well (I know … you’ve heard this story before). Slate and others report that the USA will really run out of Internet addresses this summer. Asia and Europe were already depleted in 2011 and 2012 respectively.
The US will run out of Internet addresses this summer
If you’re a Tenable customer, you might wonder how switching to IPv6 will affect your scanning efforts. For example, can Nessus® scan IPv6 networks? Will results look different? The purpose of this article is to outline how Tenable can help you with vulnerability management as you transition to IPv6.
A brief background on IPv4 and IPv6
Internet Protocol version 4 (IPv4) and Internet Protocol version 6 (IPv6) are both standards for giving any asset (e.g., laptop, smartphone, printer, router, etc.) that connects to the Internet a unique identifier or address so that asset can connect to other devices on the Internet.
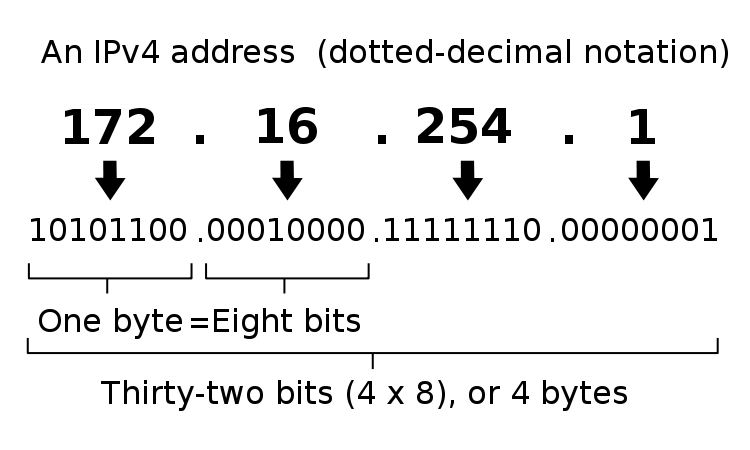
IPv4 is the most widely deployed standard today. It uses 32-bit addresses, which limits the number of possible combinations to approximately 4.3 billion:
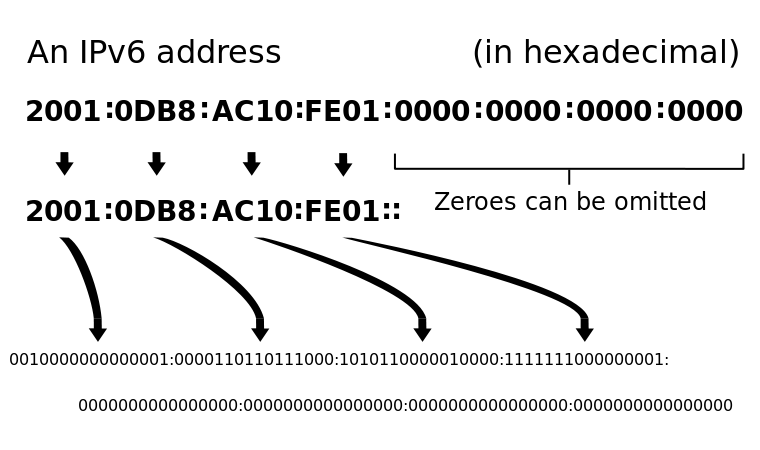
IPv6 uses a 128-bit address, which allows 1028 (79 228 162 514 264 337 593 543 950 336) more addresses than the number of IPv4 addresses:
Moving from IPv4 to IPv6 is a big but necessary change
There are other technology differences between IPv4 and IPv6 but the size, format and number of addresses available is definitely a key difference between these protocols, and an important difference to consider when doing vulnerability assessments on IPv6 networks.
Securing IPv6 networks
There are misconceptions about IPv6 security, including that IPv6 is just too big to scan so it's impossible for hackers to breach. As Tenable CEO Ron Gula wrote in the Tenable blog a few years ago, people are forgetting that a blind, brute-force attack is not the only way to breach a network. IPv6 addresses follow specific patterns, and penetration testing experts and hackers are improving their odds of success by refining their scans to take advantage of these known patterns. Weak configuration settings, exposed vulnerabilities, and compliance violations are just as dangerous in IPv6 as they are in IPv4.
Another security challenge for organizations is that even if they haven’t yet made the move to IPv6, there might be IPv6 devices already on their networks, and attackers can use default IPv6 capabilities to lurk undetected. One good example is a “link local” IPv6 address, deployed today in many organizations. By default, a host in “link local” mode (with an IP starting with fe80::) is designed to look for an IPv6 router. When a device signals that it is such a router, the “link local” host will send all their IPv6 traffic to it without any further authentication mechanism. So, if an attacker compromised a host on a network and installed IPv6 tunneling software on it, that host would basically become the de facto IPv6 router of the local network and would tunnel all traffic to the Internet via an IPv6-to-IPv4 tunnel. Many websites advertise an IPv6 address these days (such as Google) and many OSes favor IPv6 over IPv4, which means an attacker would be in a great position to sniff a lot of traffic without touching the network infrastructure just by broadcasting a single ICMPv6 packet. As Computer Weekly pointed out a few years ago, it’s important to “take care of your tunnels” and make sure your tools are able to watch for IPv6 traffic.
Performing vulnerability assessments on IPv6 networks
Most vulnerability assessment vendors today recognize this need to protect the IPv6 network. Tenable was one of the first vendors to support IPv6 in our SecurityCenter Continuous View™ solution in December 2012 (Nessus and Passive Vulnerability Scanner™ are both core components of SecurityCenter CV™). While most vulnerability assessment products now support IPv6, there are a couple of things about Tenable’s approach that are optimal for users.
- Native IPv6 support: IPv4 and IPv6 are completely different protocols. If you were to compare them to languages, one speaks in English and the other speaks French. For vulnerability assessments, you want your scanner to support both protocols natively, and not rely on translators to move data between the two protocols. Nessus supports both IPv4 and IPv6 natively, so you can run scans on either network in the native “language” of that network. Scanners that rely on translators to map IPv6 data to IPv4 run into issues in several areas. Mapping more than a few dozen assets is problematic simply because of the effort to keep mappings up to date. Plus, in IPv6, transient addresses mean IPs are constantly changing which makes maintaining a translation “map” practically impossible.
- Flexible reporting: Identifying assets by their IPv4 address has been common practice for years. An IP address like 172.16.254.1 for some people is fairly easy to remember. With IPv6, a 128-bit hexadecimal address represented as 3ffe:1900:4545:3:200:f8ff:fe21:67cf is too long for the average person to remember and to know that it represents, for example, a printer in the northeast corner of the 3rd floor of the office building. So having reports display assets in that format may not be useful for all report viewers. As part of its support for IPv6, Nessus reporting tools can display IPv6 addresses in different formats like DNS to make reporting in IPv6 environments easy to interpret. Other scanners that are translating IPv6 data to IPv4 will have a very tough time displaying data in a format that is easy for the user to understand.
Knowing what’s on your network: Passive Vulnerability Scanning
Using PVS to discover assets on your IPv6 network and sharing this information with Nessus for vulnerability assessment scanning is a powerful combination
Any conversation about IPv6 should include a discussion about how to identify the assets that are on your network and need to be scanned. With IPv6, because the size of the address space is so big, traditional host discovery methods become less effective – it simply will take too long to do a discovery scan. Tenable’s solutions like Passive Vulnerability Scanner (PVS™) become very important here. PVS performs automatic discovery of active servers, laptops, BYOD, and network devices, whether you have an IPv4 or IPv6 network. Using PVS to discover assets on your IPv6 network and sharing this information with Nessus for vulnerability assessment scanning is a powerful combination.
More information
Moving from IPv4 to IPv6 is a big but necessary change. To learn more about how Tenable can help you ensure the security of your new IPv6 environment, download our whitepaper or test drive any of our vulnerability assessment and management solutions in your IPv4 or IPv6 environments.
- Nessus evaluation request
- PVS evaluation request
Special thanks to Corey Bodzin for his generous contributions to this article.
- Nessus
- Passive Network Monitoring
- SecurityCenter
- Vulnerability Management
- Vulnerability Scanning

