Intel AMT Vulnerability Detection with Nessus and PVS (INTEL-SA-00075)
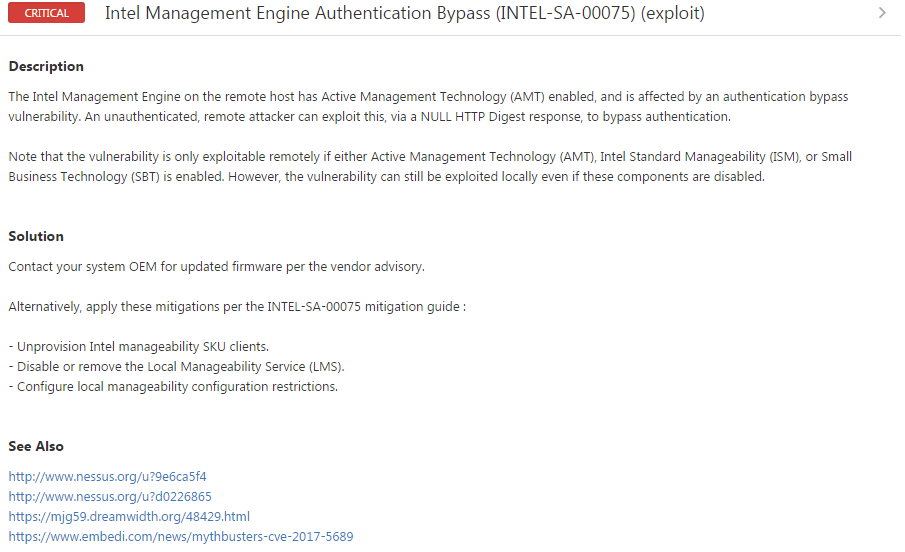
Intel recently announced an escalation of privilege vulnerability in the Intel® Active Management Technology (AMT), Intel® Standard Manageability (ISM), and Intel® Small Business Technology firmware, versions 6 through 11.6. This vulnerability has the potential of being a proverbial big one. The vulnerability has been part of the Intel chipsets for years, specifically the Management Engine (ME). The ME runs things like DRM (Digital Rights Management) and does TPM (Trusted Platform Modules) checks as well as AMT. AMT enables systems administrators to re-image bare metal machines over a remote connection. To accomplish that, the AMT requires many privileges, from network access to writing to memory and disk. The AMT is hardware and operates separately from any operating system installed on a system. Obviously, with this much power there is some protection: in this case, access to AMT is protected by a password. The vulnerability in AMT is that the password can be bypassed.
About AMT
The vulnerability is not in all Intel chipsets, but it does heavily impact servers (not consumer PCs). If you have explicitly enabled AMT at any point, you are at risk.
There have been very few technical details published on the vulnerability itself, other than it allows unauthenticated access to AMT. Currently, it is not known whether this vulnerability impacts all AMT installations or just those in Small Business Mode or Enterprise Mode. If it is Enterprise Mode only, then the impact to regular end users will be minimal. Enterprise Mode can be challenging to set up, and few if any home or even small business users would bother. However, if this vulnerability impacts all installations of AMT or even Small Business Mode, things will be much much worse.
AMT listens to TCP ports 16992 and 16993 to accept incoming network connections. There are already reports of people (from researchers to attackers) mass scanning the entire Internet looking for systems with these ports open.
Detection methods
Nessus
Tenable provides several detection tools to identify vulnerable servers.
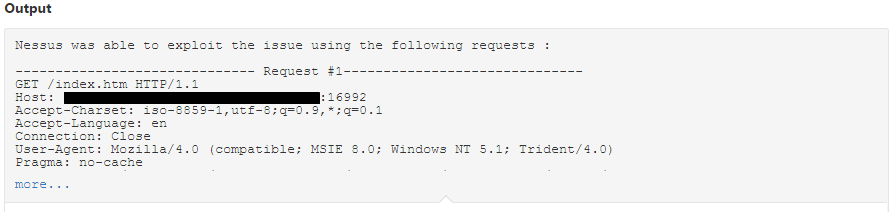
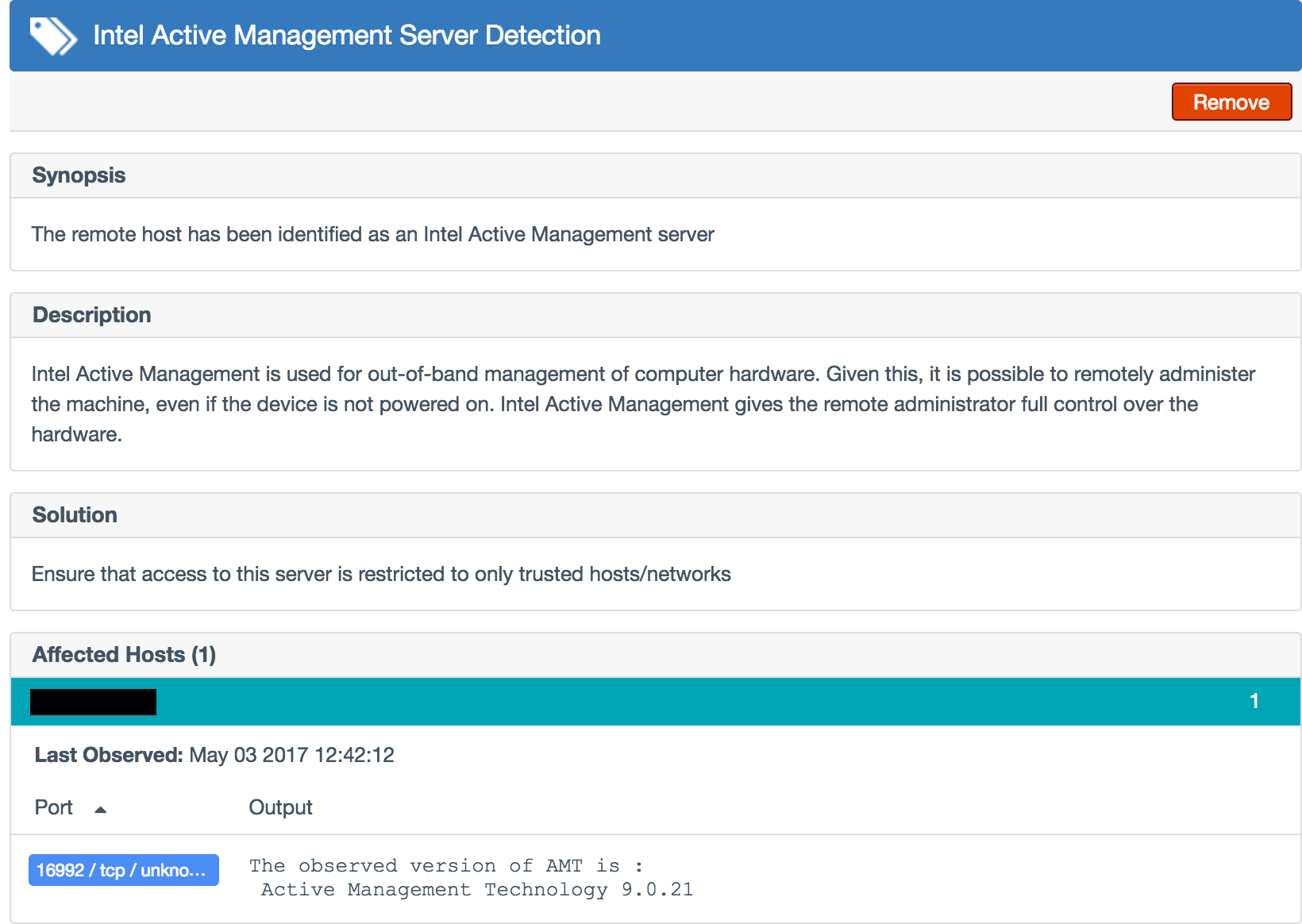
The Nessus plugin #97999 tests for the vulnerability reported in CVE-2017-5689 by performing the authentication bypass against a provisioned AMT service to confirm that it is vulnerable:
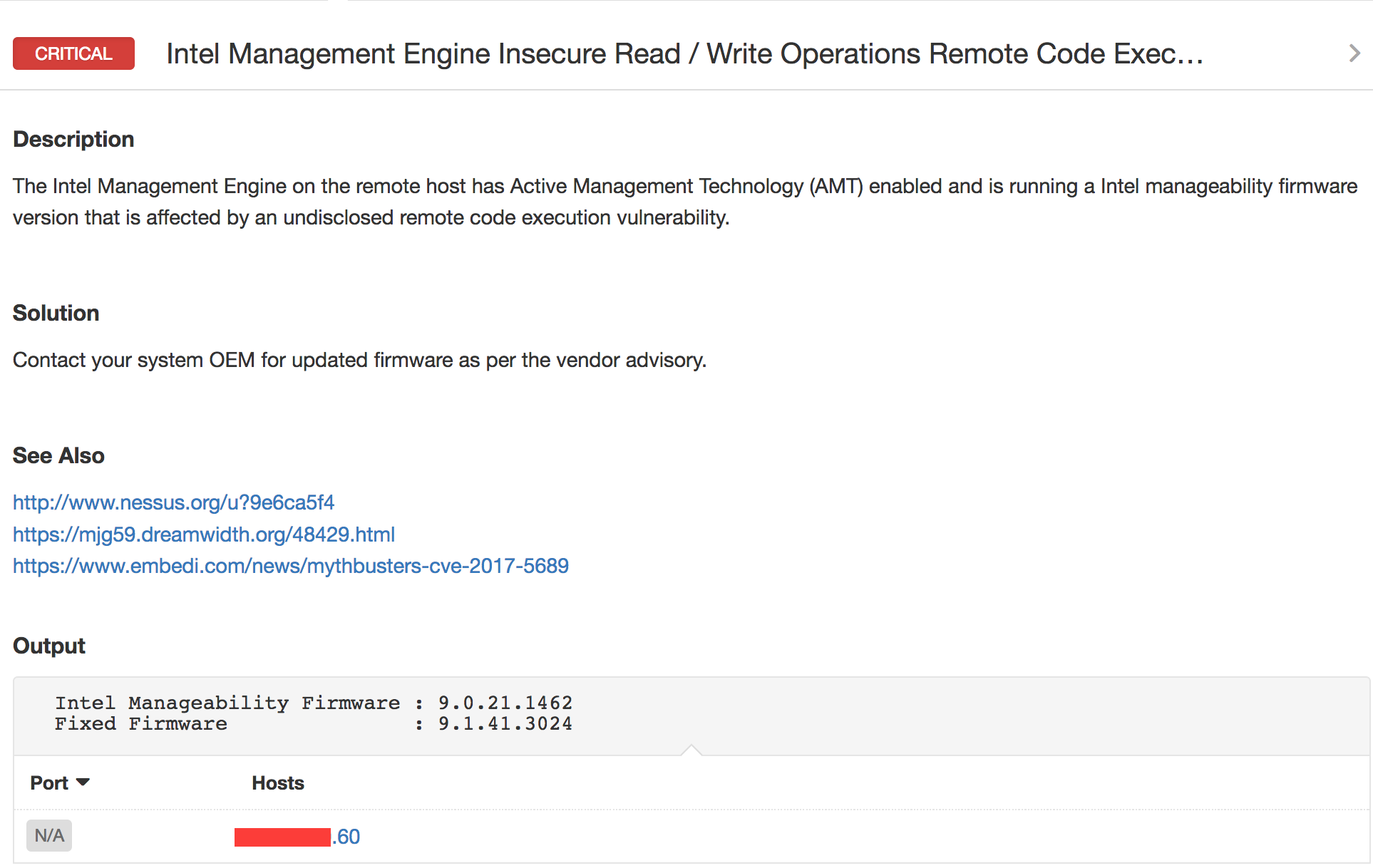
The credentialed Nessus® plugin #97997 detects systems that are affected by the Intel vulnerability and provides remediation guidance:
Another Nessus plugin #97998 detects vulnerable versions based on the banner of the service listening on port 16992. Note though the banner versions are not always granular enough, so in some cases it could result in false negatives. But it will accurately identify all systems that are vulnerable, so the risk of false positives is very low.
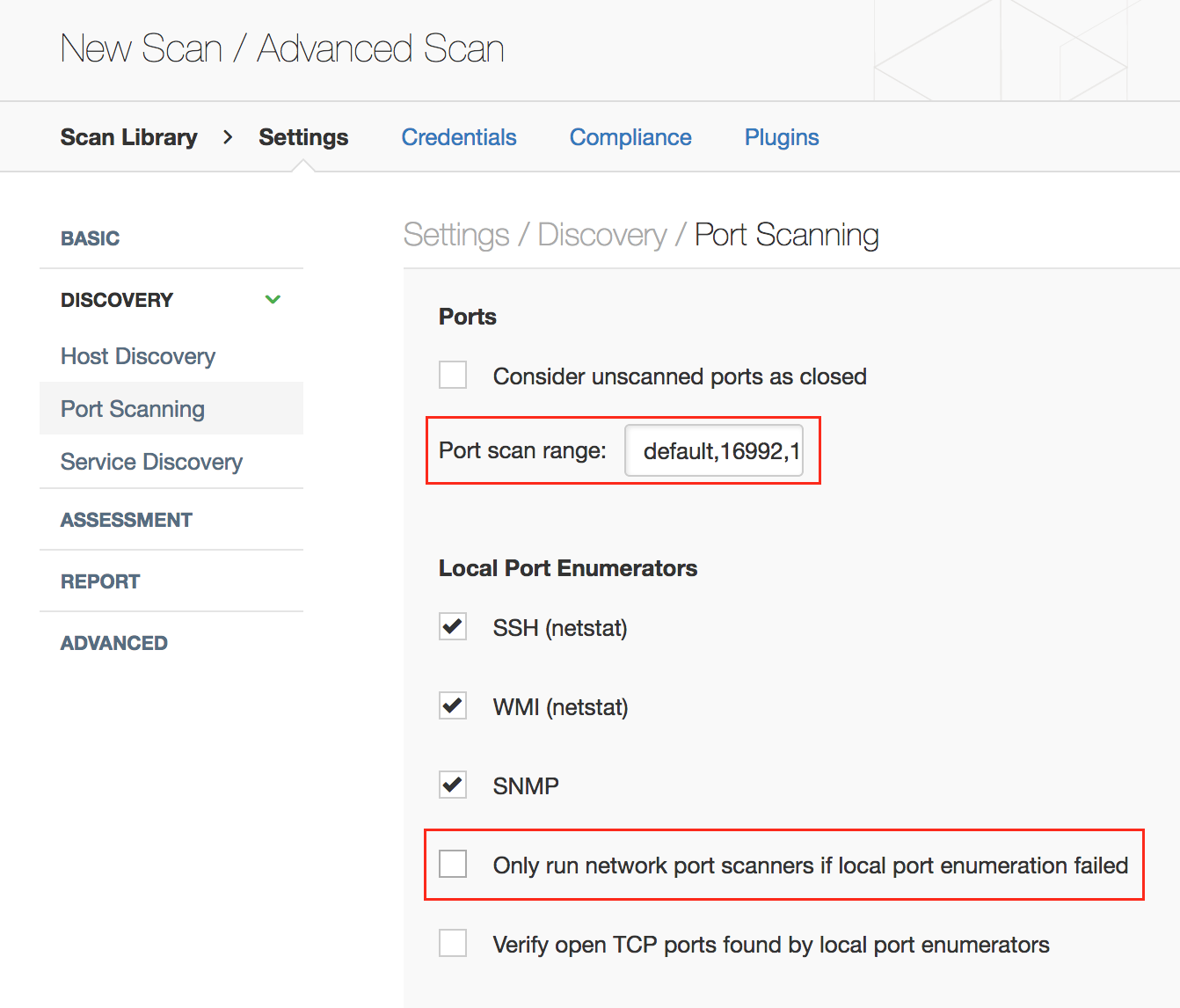
Note: You should update default Nessus port scanning preferences to probe ports 16992, 16993, and 623 in addition to the default ports. You should also enable network port scanners even though local port enumeration worked, because the Intel AMT ports are not visible to the OS:
Note: For SecurityCenter users, you must use a defined set of ports. If you are only scanning for the AMT ports, you can use these ports: 16992, 16993, 16994, 16995, 623 and 664. However if you would like to include all the default ports in a easy range setting, use 1-20000. Whichever method you choose, the keyword default must be removed from the scan template for the data to be collected properly.
PVS
Note: Passive Vulnerability Scanner (PVS) is now Nessus Network Monitor. To learn more about this application and its latest capabilities, visit the Nessus Network Monitor web page.
The Tenable Passive Vulnerability Scanner® (PVS™) can also detect hosts that have AMT running via plugin #69 55:
SecurityCenter
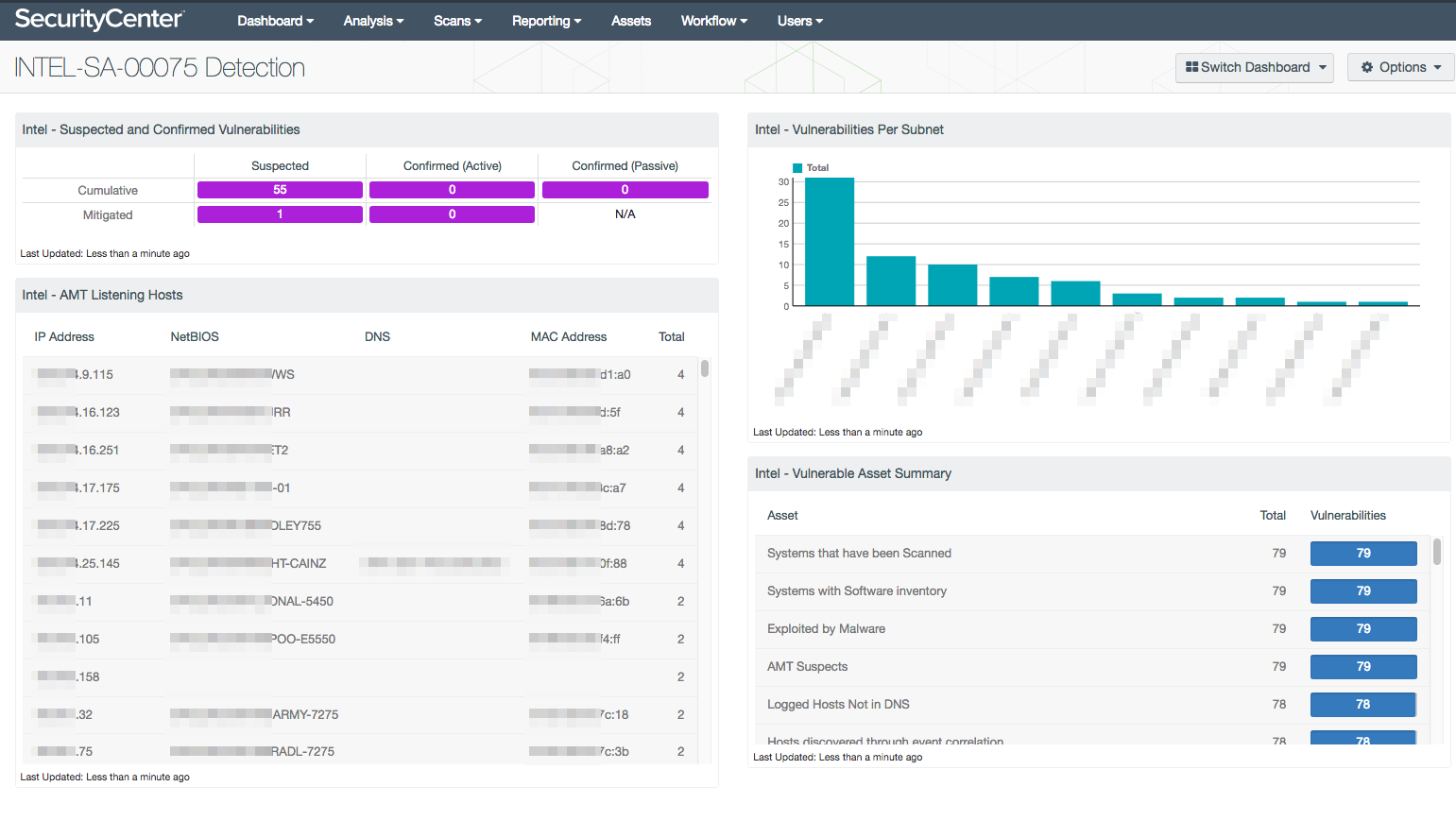
SecurityCenter® users can start assessing the risk that this vulnerability presents without having to rescan the network. SecurityCenter collects many other plugins filled with service detections, banner detection, and installed software programs. The new INTEL-SA-00075 Detection dashboard uses all these options and previously collected data to identify potentially vulnerable systems, and then uses the CVE to identify systems that are confirmed vulnerable.
The matrix in the upper left of the dashboard identifies both current and remediated vulnerabilities. As you scan your network, find the vulnerabilities, and apply patches, the numbers will move from the Cumulative row into the Mitigated row. The dashboard also shows you if the vulnerabilities are only Suspected or if they are Confirmed, using active and passive detection methods.
The INTEL-SA-00075 Detection dashboard quickly helps you understand where the most immediate risk is in your environment.
Manual
To check if you have the supported CPU, chipset, network hardware and AMT you can either use the Tenable.io plugins described above or check your BIOS. (For most systems, use CTRL-P during boot.) If you see AMT listed there, you should disable it. Determine if you have an Intel AMT, Intel SBA, or Intel ISM capable system by reviewing this document.
Mitigation
AMT has been around for about the last seven years and most machines made with AMT since then could be at risk. Once you have identified the servers that are impacted by the Intel vulnerability, you should check with your vendor(s) for a patch release – firmware updates are not automatic and are specific to each manufacturer. Older systems obviously stopped receiving firmware updates years ago and most likely won't receive a patch for this vulnerability. If your vendor does not issue a patch, you may want to follow mitigation steps recommended by Intel.
We recommend you follow these steps immediately to secure your infrastructure; otherwise, this vulnerability could result in a remotely controlled exploit and serious consequences.
Updated May 10, 2017 and May 18, 2017
- Plugins
- Vulnerability Scanning