Cybersecurity Snapshot: U.S. Gov’t Turns Up Heat on Breach Notifications, While Cyber Concerns Still Hamper Cloud Value

Learn all about the FCC’s plan to accelerate telecom breach reports. Plus, why cyber worries remain a cloud obstacle. Also, find out how to rate your cloud MSP’s cybersecurity strength. Then check out our ad-hoc poll on cloud security. And much more!
Dive into six things that are top of mind for the week ending Jan. 13.
1 - FCC wants telecoms to report data breaches immediately
Telecom companies that suffer a breach in which proprietary customer data is compromised may soon be required to disclose it right away if the U.S. Federal Communications Commission (FCC) updates its data breach reporting rule, in place since 2007.
The revised rule would mandate that telecoms notify customers and federal law enforcement immediately after discovering a breach involving “customer proprietary network information.”
Currently, the FCC requires telecom providers with 5,000 customers or more to report breaches within seven days, while providers with under 5,000 customers have 30 days to do so.

“This new proceeding will take a much-needed, fresh look at our data breach reporting rules to better protect consumers, increase security, and reduce the impact of future breaches,” FCC Chairwoman Jessica Rosenworcel said in a statement.
The FCC’s proposal is just the latest initiative by the U.S. federal government to spur businesses into reporting breaches more quickly and, in general, to be more transparent about their cyber risk and their cybersecurity practices.
U.S. government agencies currently working on new cyber breach notification requirements include the Securities and Exchange Commission and the Cybersecurity and Infrastructure Security Agency.
For more information:
- “Regulator Eyes Revamped Data Breach Reporting Requirements” (GovInfoSecurity)
- “2022 Hindsight: Breach Notification Year in Review” (JD Supra)
- “Proposed SEC Rules Require More Transparency About Cyber-Risk” (DarkReading)
- “CISA calls for public feedback on new incident reporting rules” (SC Magazine)
- “SEC, CISA push dueling cyberattack incident reporting” (Protocol)
2 - Report: Security still a main obstacle to cloud value
As organizations strive to maximize the benefits of their cloud investments, they continue to struggle with recurrent and persistent obstacles, including security and compliance risks.
That’s a finding from Accenture’s report “The race to the cloud: Reaching the inflection point to long-sought value,” based on proprietary research and a global survey of 800 IT and business leaders.
Compared with the report’s previous edition, published in 2020, surveyed organizations have made progress towards achieving full value from their cloud efforts, with 42% reporting having fully achieved their cloud goals, up from 37%.
But a set of “stubborn barriers” continues to stand in the way, with security and compliance risks tied for first along with complexity of business and operational change. Legacy application modernization ranked third in this list of usual suspects hampering cloud-value realization.
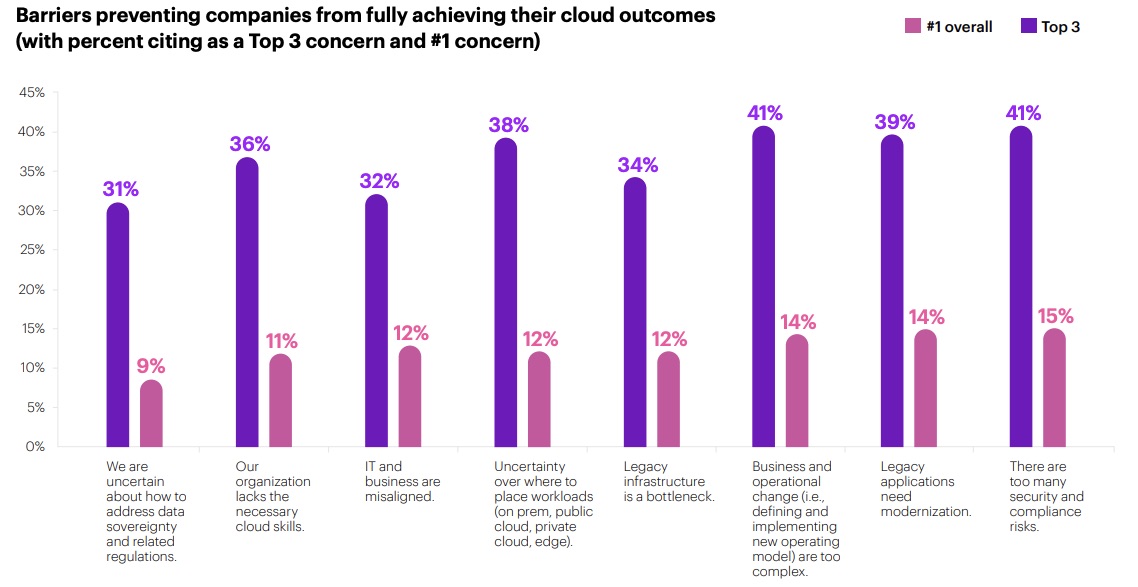
(Source: Accenture’s report “The race to the cloud: Reaching the inflection point to long-sought value,” January 2023)
A key reason why these obstacles remain is that organizations’ cloud efforts are becoming more complex, as more business-critical workloads shift from on premises.
“The challenge now will be in defining the right use cases centered on a much broader definition of value, and using cloud as an operating system to bring together data, AI, applications, infrastructure and security to optimize operations and accelerate growth,” the report reads.
For more information, check out report highlights or read the full report.
3 - An ad-hoc poll on cloud security
During the recent Tenable webinar “When It Comes to Effective Cloud Security, Sharing is Caring,” we polled attendees on various aspects of their cloud security processes, tools and strategies. Check out the results below.
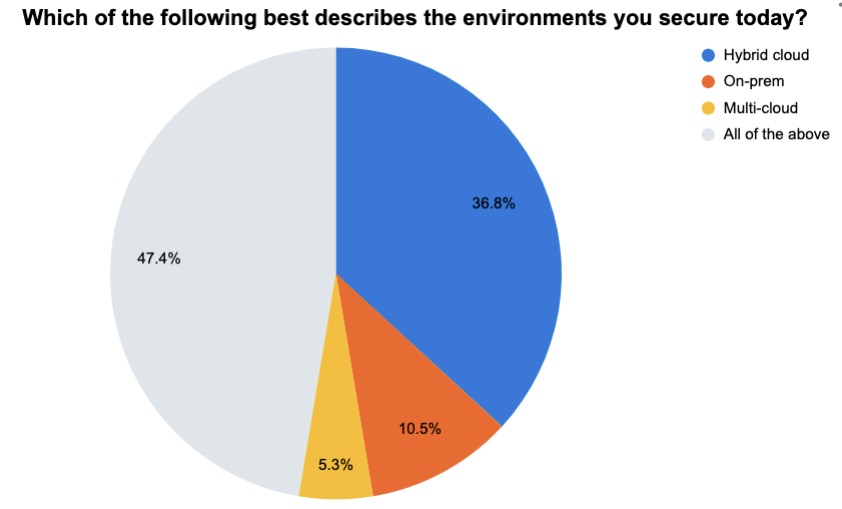
(Source: 57 respondents polled by Tenable, December 2022)
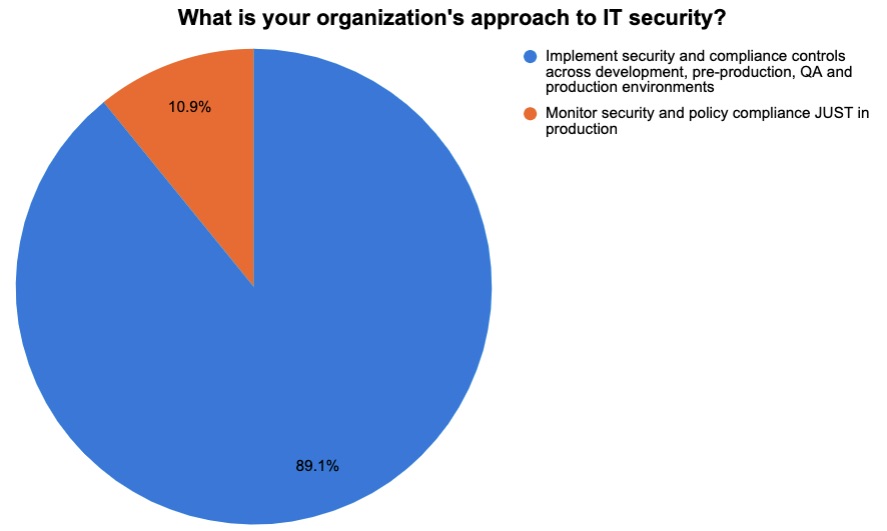
(Source: 46 respondents polled by Tenable, December 2022)
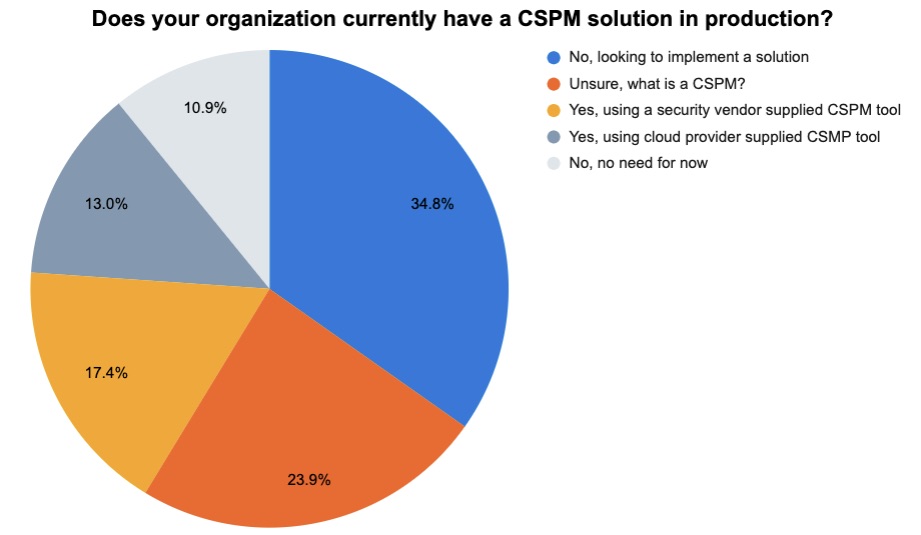
(Source: 46 respondents polled by Tenable, December 2022)
For more information about cloud security, check out these Tenable resources:
- “Cloud Security: 5 Key Takeaways from the SANS DevSecOps Survey” (blog)
- “Scaling Cloud Adoption without Sacrificing Security Standards” (on-demand webinar)
- “How to Choose a Modern CSPM Tool to Reduce Your Cloud Infrastructure Risk” (blog)
- “To Boost Software Supply Chain Security, Stop the Finger-Pointing” (blog)
- “How CISOs Can Stop Worrying About Cloud Security and Rest Easy” (infographic)
- “The Four Phases of Cloud Security Maturity” (on-demand webinar)
4 - All quiet on the IoT breach front?
In its list of 2022’s most relevant trends and happenings in the IoT world, market researcher IoT Analytics left vacant the category “IoT security breach of the year.” While in years past it has singled out major IoT breaches, it determined that none of the IoT security incidents recorded in 2022 rose to that level of significance.
“We interpret this as a positive sign and a direct result of the investment that has gone into security research and solutions,” the firm wrote in its “IoT 2022 in review: The 10 Most Relevant IoT Developments of the Year” report.
Instead, IoT Analytics turned its attention to various IoT attack tools, malware and vulnerabilities that emerged in 2022 and that it considers particularly dangerous.
For more information about IoT security:
- “What is IoT security?” (TechTarget)
- “Secure IoT best practice guidelines” (IoT Security Foundation)
- “Top 5 IoT security threats and risks to prioritize” (TechTarget)
- “Guidance for testing IoT security products” (Tenable)
- “NIST Cybersecurity for IOT Program” (U.S. National Institute of Standards and Technology)
5 - Using MSPs to manage your cloud services? Here’s some security advice
If you’re outsourcing the operation of your cloud services to a managed service provider (MSP), the U.K.’s National Cyber Security Centre (NCSC) has some recommendations to keep your organization safe.
Along with the benefits of handing over tasks like provisioning new cloud instances to an MSP come security risks from, for example, giving the MSP administrative access to your data, the NCSC points out in a recent blog.
“This increases the attack surface, as there are now more systems that, if attacked, would compromise your data,” the blog reads.

Here’s a list of questions the NCSC recommends you ask to reduce the risk of falling victim to a cyberattack via a third-party like an MSP:
- Have you given the MSP only the cloud privileges they need to provide the contracted services, or have you granted them excessive access?
- Do you have full visibility from your security operations center of the cloud services actions the MSP takes on your behalf?
- Does the MSP follow secure administration practices and document them?
- Is the MSP itself outsourcing administration of some of your cloud services to another organization – a fourth-party in this case?
- What is the MSP contractually required to disclose regarding breaches that impact your services or data, and to what extent are they required to collaborate with you in case of a security incident?
For more information about managing MSP third-party risk:
- “Protecting Against Cyber Threats to MSPs and their Customers” (CISA, NCSC and other national cybersecurity agencies)
- “How To Assess the Cybersecurity Preparedness of IT Service Providers and MSPs” (Tenable)
VIDEOS:
How SMBs should select a security-savvy managed service provider (IDG TECHtalk)
Rethinking Efficient Third-Party Risk Management (RSA Conference)
6 - Cyber among WEF’s top 10 global risks
A cyber risk ranks among the top 10 in the World Economic Forum’s (WEF) lists of short- and long-term global risks. The WEF’s “Global Risks Report 2023” lists widespread cybercrime and cyber insecurity as the eighth most severe global risk within a two-year period and within a 10-year period.
Global Risks Ranked by Severity over the Short and Long Term
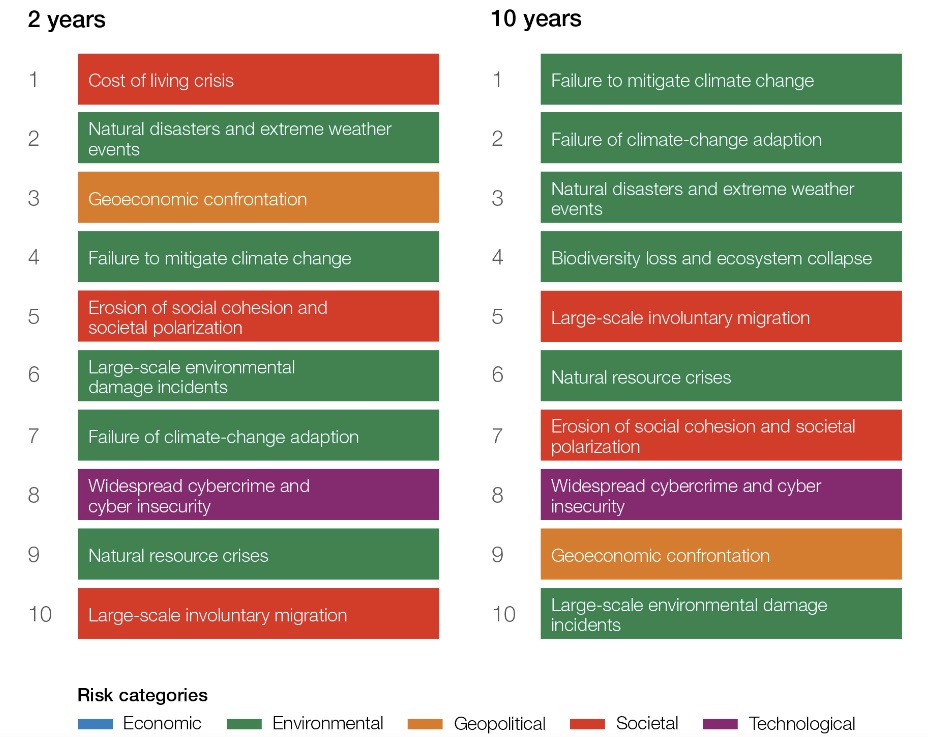
(Source: World Economic Forum’s “Global Risks Report 2023”, January 2023)
Moreover, another cyber-related risk – cyberattacks on critical infrastructure – ranks fifth among what WEF calls “currently manifesting risks,” which are those expected to have a global impact this year.
Other technology-related risks mentioned in the report include digital power concentration, digital inequality and dangers of emerging technologies like AI and quantum computing. “Technology will exacerbate inequalities while risks from cybersecurity will remain a constant concern,” reads the 98-page report.
To tackle global cybercrime in particular, WEF calls for more cooperation between countries, including more transparent information sharing, international rules and joint efforts. WEF currently is involved in collaborative efforts with public- and private-sector partners in areas including:
- Free cybersecurity training and education
- Research into risks from next-generation technologies
- Guidance for IoT security
The report is based on a survey of 1,200-plus experts from academia, business, government. For more information, check out a report summary, report highlights or the full report, as well as as a separate article about cybercrime risks and solutions.
Press conference on the WEF’s Global Risks Report 2023
- Cloud
- Cybersecurity Snapshot
- Internet of Things


