Cybersecurity Snapshot: IoT Vendors Fail at Vulnerability Disclosures, While Cyber Threats Again Top Business Risks

Learn all about how most IoT product makers lack vulnerability disclosure policies. Plus, businesses again rank cyber risk as their top concern. Also, check out a new toolbox for cybersecurity awareness programs. Then scan the latest list of top malware. And much more!
Dive into six things that are top of mind for the week ending Jan. 27.
1 - Cyber tops ranking of business risks – again
Here’s further proof that business leaders are hyper aware about how devastating cyber incidents can be to their organizations.
The “Allianz Risk Barometer 2023” ranked cyber incidents, including digital outages, ransomware attacks and data breaches, as the biggest business risk in the world.
It’s the first time the same risk has topped this annual report from insurer Allianz Global Corporate & Specialty in consecutive years.
The report, now in its 12th year and based on a survey of 2,712 risk management experts from 94 countries and territories, found that cyber risk also ranks first among small business worries. It’s also organizations’ most feared cause of business interruption, as well as their main environmental, social and governance (ESG) concern.
Which causes of business interruption does your company fear most?

(Source: “Allianz Risk Barometer 2023” report from Allianz Global Corporate & Specialty, January 2023. Respondents could choose more than one risk.)
Among cyber risks, respondents ranked data breaches as the most concerning for various reasons, including recovery costs, government fines, customer lawsuits and reputational damage. Ransomware was the second most concerning cyber risk.
Which cyber exposures concern your company most over the next year?
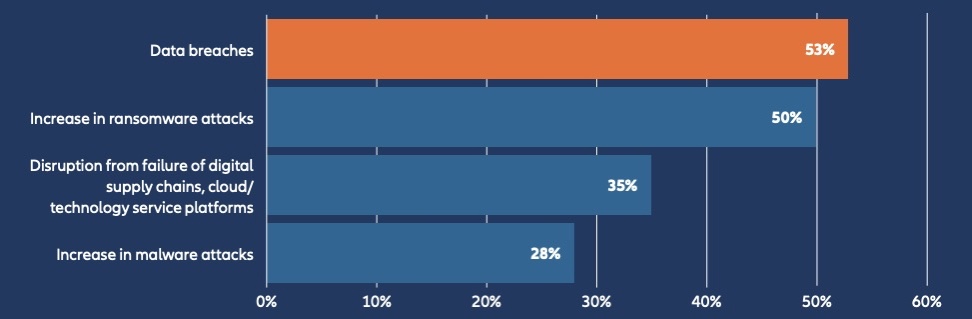
(Source: “Allianz Risk Barometer 2023” report from Allianz Global Corporate & Specialty, January 2023. Respondents could choose more than one answer.)
The key to reducing risk? Boost cyber hygiene by strengthening IT security training, incident response and cybersecurity governance, the report suggests.
For more information, you can check out highlights from the report, read a summary of the cyber risk findings, download the full report and watch these Allianz videos:
Allianz Risk Barometer 2023 - These are the top business risks
Global media Call introducing Allianz Risk Barometer 2023
2 - Who’s in charge of web app security? Check out our poll.
At a recent webinar about Tenable.sc, we polled attendees about web application security (WAS). Check out what respondents said about the number of web apps they manage and which team is in charge of their WAS program.
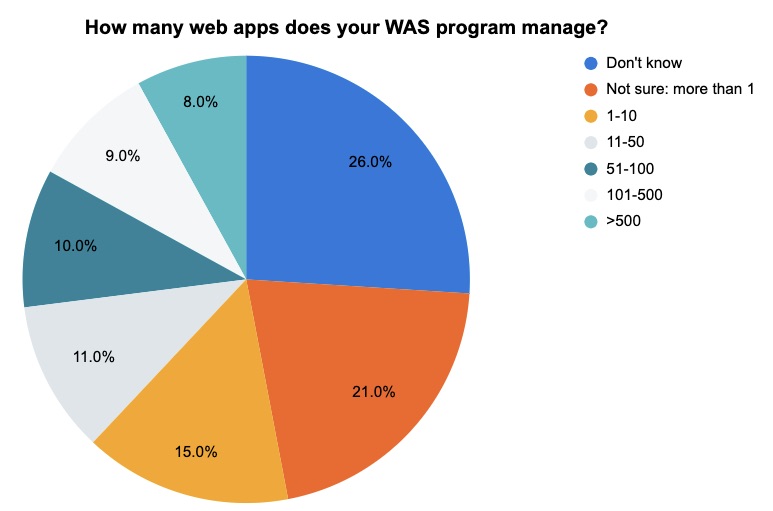
(100 respondents polled by Tenable, December 2022)
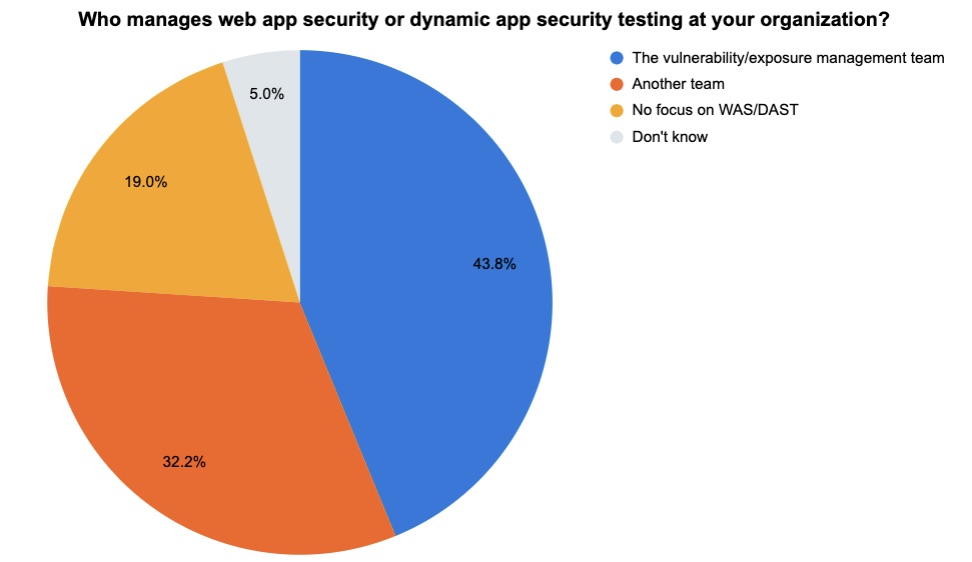
(121 respondents polled by Tenable, December 2022)
For more information about web app and cloud security, check out these Tenable resources:
- “Web App Security: 5 Best Practices” (ebook)
- “4 Steps To Achieving Comprehensive Kubernetes Security” (white paper)
- “Cloud Security Basics: Protecting Your Web Applications” (blog)
- “5 Key Takeaways from the SANS DevSecOps Survey” (blog)
- “Web App Security: 3 Lessons We Learned From Formula 1 Racing” (blog)
3 - Vendors of IoT products must step up vulnerability disclosures
A woefully low number of companies that sell internet of things (IoT) products have a vulnerability disclosure policy in place, a situation that paints a discouraging picture for IoT security.
Specifically, among 332 IoT product vendors surveyed, only 27% have a vulnerability disclosure policy, even despite an increase in legislation and regulation regarding this issue. That’s the main finding from the IoT Security Foundation’s fifth annual “State of Vulnerability Disclosure Policy Usage in Global Consumer IoT in 2022” report.
The companies, which were surveyed by IoT and mobile security specialist Copper Horse, sell IoT products for consumer and commercial uses, including appliances, routers and smart home devices.
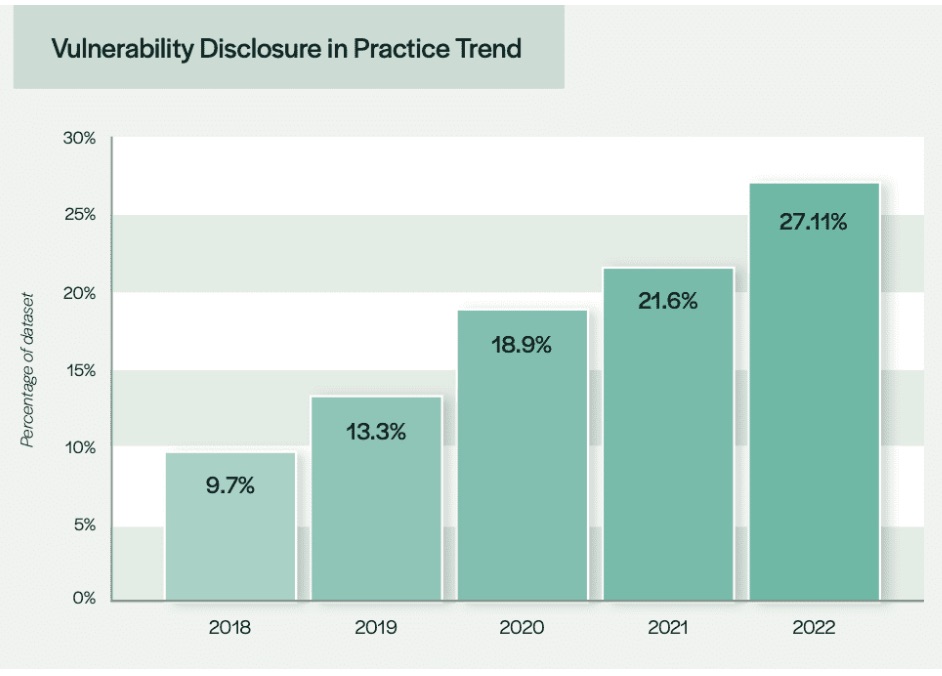
(Source: “State of Vulnerability Disclosure Policy Usage in Global Consumer IoT in 2022” report from the IoT Security Foundation, January 2023)
The percentage of IoT vendors with a vulnerability disclosure policy, while higher than last year (21.6%) is still “disappointingly low” and “far below” the desired level of near 100%, according to the IoT Security Foundation.
“The general story is depressingly similar to the previous annual reports published by the IoTSF,” reads the report.
These policies outline how third-party researchers can report vulnerabilities they discover on IoT products to the vendors, as well as how the vendor will handle the disclosure process.
For more information about IoT security and vulnerability disclosure:
- “Vulnerability Disclosure: Best Practices Guidelines” (IoT Security Foundation)
- “Coordinated Vulnerability Disclosure Process” (U.S. Cybersecurity and Infrastructure Security Agency - CISA)
- “The dark web’s criminal minds see Internet of Things as next big hacking prize” (CNBC)
- “A framework for securing the IoT ecosystem” (Tenable)
VIDEOS
Do IoT Devices Make Your Network Unsecure? (Cyber Gray Matter)
The Future of IoT Security (TechTarget)
4 - A “toolbox” to boost employee cybersecurity awareness
Looking for guidance on establishing a security awareness program? Eager to improve an existing one to better train and educate employees on cybersecurity best practices? The EU Agency for Cybersecurity (ENISA) just published a “do it yourself” toolbox for raising cybersecurity awareness.

The “AR-in-a-Box,” as the collection of documents is called, includes guidelines, instructions, quizzes, games and more on topics including:
- How to build a security awareness program for your organization
- How to create an external security awareness campaign
- How to choose tools and channels to reach your target audience
- How to develop key performance indicators to assess your security awareness program
For more information about effective cybersecurity awareness programs:
- “Cybersecurity Awareness for Employees: Best Practices” (IT Business Edge)
- “Building a Cybersecurity Awareness Program” (Carnegie Mellon University study)
- “How CIOs can drive identity-based security awareness” (VentureBeat)
VIDEOS
How to Build a Strong Security Awareness Program for Your Employees (EC-Council)
How to make security awareness training fun and engaging (Infosec)
Building, Maturing and Sustaining a Security Awareness Program (SANS Institute)
5 - GAO: Heed our cybersecurity recommendations
Over the past 12 years, the U.S. Government Accountability Office (GAO) has made about 335 specific cybersecurity recommendations to federal agencies, almost 60% of which haven’t been implemented. That’s according to – you guessed it – a GAO report, in which the agency encourages the U.S. federal government to heed its cybersecurity advice.
While it’s not clear whether GAO’s public plea will spur federal agencies into action, it’s interesting to check out the cybersecurity risks and challenges the agency highlights, which likely apply to most private-sector companies as well.
These include:
- The importance of having a comprehensive cybersecurity strategy
- Supply chain risks
- The shortage of cybersecurity professionals
- The danger from emerging technologies, like quantum computing, IoT and artificial intelligence
The report reiterates key recommendations GAO has made over the years, many of which may be applicable to organizations of all types.
For more information, check out the coverage from NextGov, Business Insurance, Infosecurity Magazine and The Register.
6 - The latest CIS top 10 malware ranking is out
And here’s the list of most prevalent malware strains for December 2022 from the Center for Internet Security (CIS), featuring the return of NanoCore, Snugy, and Tinba, with SessionManager2 topping the rankings.
Here’s the full list, in descending order:
- SessionManager2, a malicious Internet Information Services (IIS) module or backdoor
- Gh0st, a remote access trojan (RAT)
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI) and EternalBlue
- ZeuS, a modular banking trojan that uses keystroke logging
- Agent Tesla, a RAT that captures credentials, keystrokes and screenshots
- NanoCore, a RAT that spreads via malspam as a malicious Excel spreadsheet
- Ursnif (aka Gozi and Dreambot), a banking trojan
- LingyunNet, riskware that uses victims’ system resources
- Snugy, a PowerShell-based backdoor
- Tinba, a banking trojan also known as Tiny Banker due to its small file size
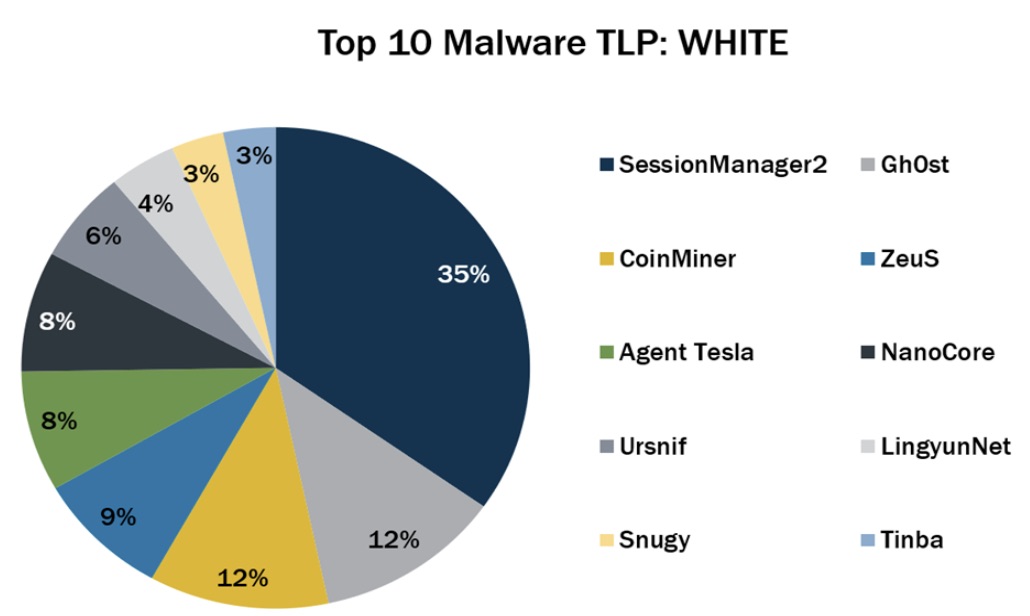
(Source: Center for Internet Security, December 2022)
For more information, check out the CIS report, which has plenty of details, context and indicators of compromise for each malware strain.
- Cybersecurity Snapshot
- Exposure Management
- Malware
- Vulnerability Management
- Vulnerability Scanning
