Cybersecurity Snapshot: How To Boost Customers' Trust in Your Digital Services

Check out how beefing up digital trust in your technology yields key business benefits. Plus, a sophisticated cyber espionage operation has been defused. Also, why cyberattack victims should speak up. In addition, don’t miss our poll on mobile device security. And much more!
Dive into six things that are top of mind for the week ending May 12.
1 – It’s a matter of (digital) trust
Do your customers and partners trust the reliability and security of your organization’s digital services? If not, the business consequences can be dire – especially for organizations with increasingly or already fully digitized operations.
If you're interested in learning how your company can boost confidence in the integrity of its technology, check out ISACA’s “State of Digital Trust 2023” report. Its main finding: While most organizations recognize the importance of digital trust, many aren’t taking the right steps to achieve it – but there are ways to remedy that.

“As organizations move to a digital-first business model, trust is the essential component that must be earned before, during and after every interaction,” Interim ISACA CEO Tracey Dedrick said in a statement.
To boost digital trust, take a holistic, collaborative approach that encompasses areas including security, risk, data protection, privacy and governance, according to ISACA.
Here are key findings from the study, based on a survey of 8,100 professionals involved in areas that impact digital trust:
- 98% of respondents say digital trust is important, and 82% say it’ll be even more important in five years
- Only 13% of organizations polled have a dedicated staff for digital trust, and only 19% say it’s a priority for their board of directors
- 29% have no way of quantifiably measuring digital trust
- 53% feel confidence about the digital trustworthiness of their organization
ISACA, which views digital trust as “an umbrella” under which existing functions are synchronized, considers it essential to craft a digital trust framework that’s aligned with business goals. Other important elements for boosting digital trust include: sufficient skills and training; leadership buy-in; alignment between digital trust and enterprise goals; and the necessary budget.
The good news is that organizations with a strong digital trust say it has yielded concrete benefits for them, including stronger reputation, data reliability, privacy protections and cybersecurity, and customer loyalty.
For more information check out:
- The full “State of Digital Trust Report 2023”
- The report’s announcement
- The companion blog “Taking Digital Trust from a Lofty Goal to a Measurable Reality”
- Links to report infographics
VIDEO
What does digital trust mean to you? (ISACA)
2 – A temperature check on mobile asset security
At a recent Tenable webinar, we polled attendees on securely managing remote and mobile assets. Check out what they said!
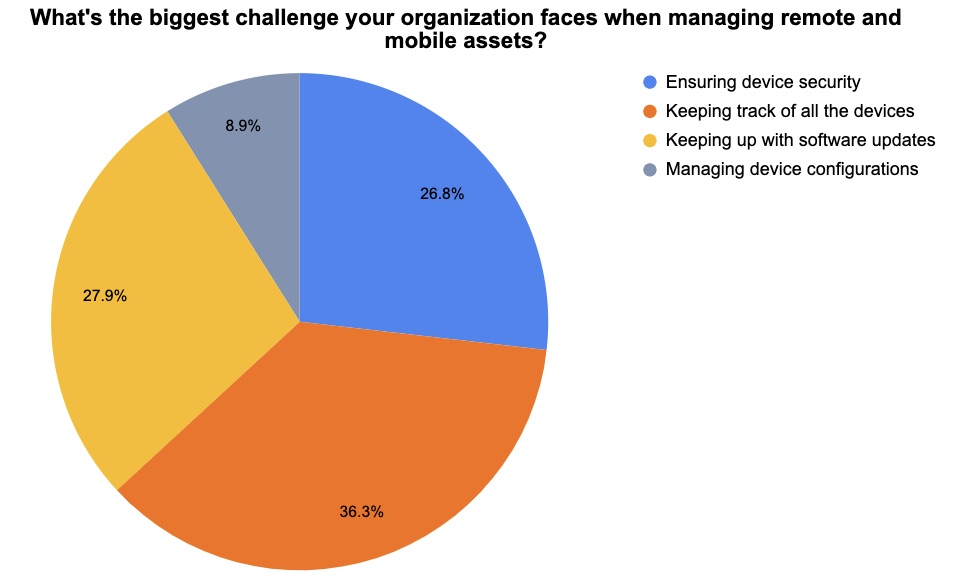
(Source: 179 webinar attendees polled by Tenable)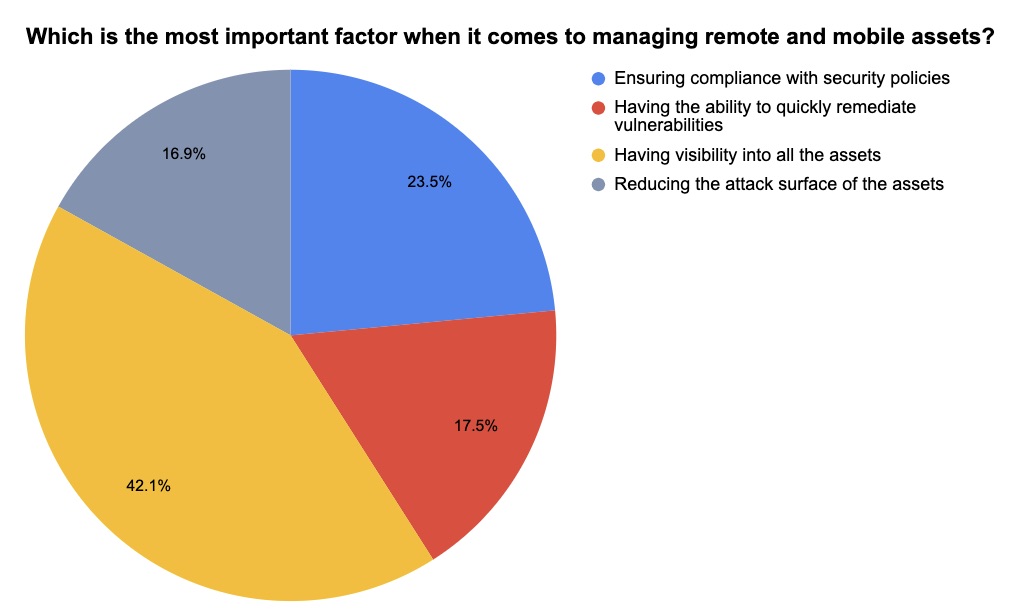
(Source: 183 webinar attendees polled by Tenable)
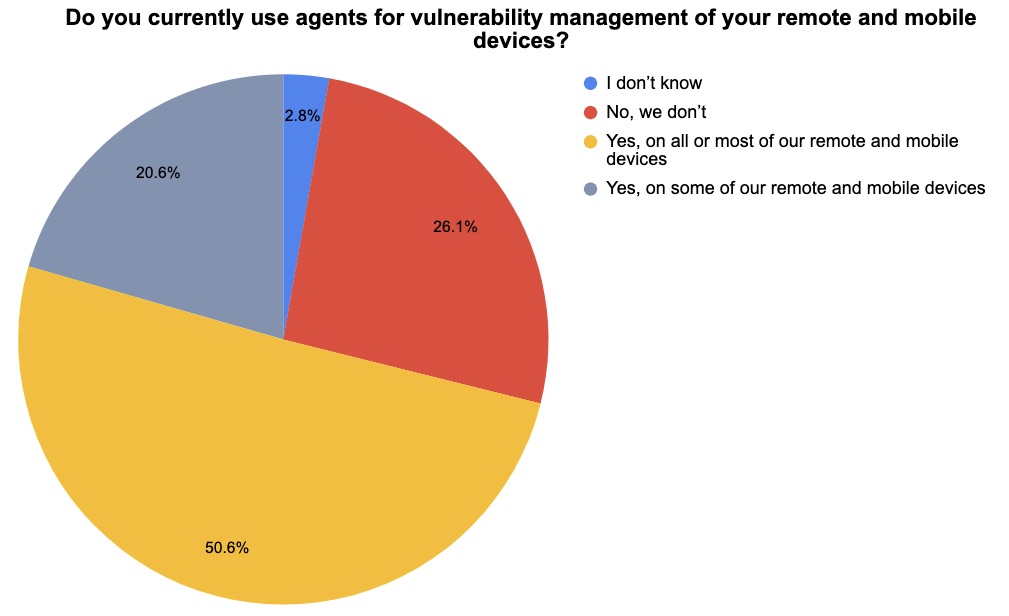
(Source: 180 webinar attendees polled by Tenable)
3 – U.K. government: Cyberattack victims must speak up
The U.K.’s cybersecurity and data privacy agencies called on victims of cybercrimes to report the incidents, saying that staying mum helps the bad guys.
In a joint blog post this week, leaders from the NCSC and the Information Commissioner’s Office (ICO) clamored for more transparency from targets of cyberattacks, especially ransomware.

“Being open about an attack by seeking support and communicating openly with the NCSC and ICO in the days following it can only help you, while sharing information about the attack with your trust communities later on will ultimately improve the threat landscape for everyone,” they wrote.
In the blog, they outlined these six myths that they say foster a culture of toxic silence.
- Covering up the attack makes everything ok
- Reporting the incident makes it more likely to become public
- Paying a ransom makes the incident go away
- There’s no need to pay a ransom if you have good offline backups
- You don’t need to report the attack to the ICO if there’s no evidence of data theft
- If your data is leaked, you’ll only receive a fine
“If attacks are covered up, the criminals enjoy greater success, and more attacks take place. We know how damaging this is,” wrote ICO Director of Regulatory Cyber Mihaela Jembei and NCSC Deputy Director of Incident Management Eleanor Fairford.
For more information about the importance of cyberattack transparency:
- “Why reporting an incident only makes the cybersecurity community stronger” (CSO Online)
- “Enterprises reluctant to report cyber attacks to authorities” (TechTarget)
- “UK ‘increasingly concerned’ ransomware victims are keeping incidents secret” (The Record)
- “U.S. Senate report calls out lack of ransomware reporting” (TechTarget)
VIDEO
Eleanor Fairford and Mihaela Jembei in conversation (CyberUK Online)
4 – Russian “Snake” cyber spying operation exposed, disrupted
A highly advanced cyber snooping malware that Russia has used for 20 years to spy on sensitive targets and collect information on them has been unmasked. Further, a peer-to-peer network at the center of the operation has been disabled.
That’s the word this week from the U.S. Cybersecurity and Information Security Agency (CISA) and the U.S. Department of Justice (DOJ), which, in conjunction with a host of global partners, announced the strike against Russia’s Snake malware network.
CISA called Snake “the most sophisticated cyber espionage tool” developed and used by Russia’s Federal Security Service (FSB) intelligence agency, while the DOJ described it as “the foremost cyber espionage tool of the Russian government.”

So what makes Snake so special? Here are a few of its troubling characteristics:
- The FSB created a custom P2P network for Snake made up of many compromised computers worldwide.
- Snake’s usage of encryption and fragmentation in its communications protocols made it highly stealthy, allowing it to often remain undetected in victims’ computers indefinitely.
- Its modular architecture made it easy to add or replace components, which also simplified the creation of Snake instances for different host operating systems.
- Snake benefitted from software engineering design of a superior quality.
Snake infrastructure was detected in 50-plus countries across the Americas, Europe, Asia, Africa and Australia, according to the 48-page CISA advisory, which it published jointly with law enforcement agencies from multiple other countries, including the U.K., Canada and Australia.
The FSB has used Snake tactically and selectively, choosing high-value targets carefully and deliberately, including research institutions, government agencies and journalists. “Within the U.S., the FSB has victimized industries including education, small businesses, and media organizations, as well as critical infrastructure sectors including government facilities, financial services, critical manufacturing, and communications,” reads the CISA advisory.
In its advisory, CISA offers detailed technical information and mitigation recommendations designed to help cybersecurity teams detect and defend themselves from Snake.
For more details, check out:
- The CISA advisory summary
- The full CISA advisory titled “Hunting Russian Intelligence ‘Snake’ Malware”
- The DOJ’s press release
- The announcement from the U.K.’s National Cyber Security Centre (NCSC)
5 – Study: Cyberthreat intelligence is underused
Although a whopping 95% of enterprises with at least 1,000 employees have a budget for cyberthreat intelligence, many of these CTI programs fall short. That’s according to the Enterprise Strategy Group’s (ESG) report “Cyber-threat Intelligence Programs: Ubiquitous and Immature,” which found that:
- 46% of CISOs don’t check out CTI reports regularly
- 64% of organizations suspect their CTI sources are sometimes inaccurate
- 82% of organizations believe CTI programs are often treated as academic exercises
- 85% of security pros say their CTI program relies too much on manual processes
- 72% of security pros struggle to find relevant information in CTI data
- 63% of security pros say their organization lacks the necessary staff and skills to manage the CTI program

So what’s the problem? “It’s not the CTI as much as it is the CTI program,” wrote ESG analyst Jon Oltsik. “To achieve success, a CTI program must begin with defined objectives (in this case, tactical, operational, and strategic objectives), strong management, achievable workloads, and a feedback loop for continuous improvement.”
ESG recommends the following “lifecycle” approach for CTI programs:
- Planning and direction, where threat analysts define priority intelligence requirements
- CTI collection, which involves identifying the needed intelligence data and obtaining it
- Processing, during which the collected data is translated into threat intelligence
- Analysis and production, where the data is sliced and diced for actionable signals
- Dissemination of the CTI data and feedback from recipients
To get more details, check out the report’s infographic and Oltsik’s articles on CSO Online about the report: “Cyber threat intelligence programs: Still crazy after all these years” and “Dissecting threat intelligence lifecycle problems.”
6 – Towards a globally uniform cyber policy framework
Governments worldwide should harmonize their cybersecurity regulations and laws, and collaborate with each other more closely. Doing so will yield more consistent and effective policies for preventing cyber breaches.
So says a new report about global cyber policies from the Information Systems Security Certification Consortium, known as (ISC)², and the U.K.’s Royal United Services Institute (RUSI).
Titled "Global Approaches to Cyber Policy, Legislation and Regulation," the report looks at cybersecurity policies, regulations and laws in the U.K., the U.S., Japan, Canada, Singapore and the EU, hoping it serves as a guide for policymakers globally.

“Policymakers must take a proactive, rather than reactive, approach toward cybersecurity policy and collaborate across borders, industries and sectors to establish common standards, protocols and best practices,” said Clar Rosso, CEO of (ISC)², said in a statement.
The report focuses on four major areas:
- The general context in which cyber policies are crafted
- Priorities for protecting critical national infrastructure
- Development approaches for cyber skills and cyber workforce
- International cooperation for developing cyber norms
For more details, check out:
- A summary of the report
- The full report
- The report’s announcement
- Cloud
- Cybersecurity Snapshot
- Malware
- Remote Workforce
- Risk-based Vulnerability Management


