Cybersecurity Snapshot: CISOs Value Prevention Over Response, While CISA Urges Cyber Teams To Prep for Quantum Attacks

Time to start prepping for the quantum computing threat? CISA thinks so. Plus, why security leaders are prioritizing security prevention tools. Also, find out why ransomware attacks surged in July. Oh, and the White House wants your input on open source security. And much more!
Dive into six things that are top of mind for the week ending August 25.
1 – The quantum computers are coming!
As attackers salivate at the future prospect of weaponizing powerful quantum computers, the U.S. government says public- and private-sector organizations alike must start getting ready now – especially critical infrastructure operators.
This week, the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA) and National Institute of Standards and Technology (NIST) released a joint factsheet urging organizations to prepare for attacks that will use quantum computing.
“Post-quantum cryptography is about proactively developing and building capabilities to secure critical information and systems from being compromised through the use of quantum computers,” Rob Joyce, Director of NSA Cybersecurity, said in a statement.

When they become available, probably around 2030, quantum computers will have the capacity to decrypt data protected with today’s public-key cryptographic algorithms. Thus, the agencies say it’s time for IT, OT and security teams to start taking steps to protect their organizations, including:
- Develop a “quantum readiness roadmap” by establishing a project management team
- Plan the migration to post-quantum cryptographic standards
- Assess their organizations’ reliance on quantum-vulnerable cryptography
- Inventory systems, assets and data that are vulnerable to quantum computers
- Discuss post-quantum plans with key technology vendors
“The transition to a secured quantum computing era is a long-term intensive community effort that will require extensive collaboration between government and industry. The key is to be on this journey today and not wait until the last minute,” Joyce said.
To get all the details, read the joint alert, announcement and factsheet, and visit CISA’s “Post-Quantum Cryptography Initiative” homepage.
For more information about the quantum computing cyber risks, check out these Tenable blogs:
- “CISA: Critical infrastructure must prep for quantum computing threat”
- “Quantum computing’s security threat looms”
- “How to protect quantum computers from cyberattacks”
- “Time to prep for the quantum computing threat”
2 – Study: Cyber leaders prioritize detection and prevention
Enterprise security leaders are allocating more investments to detection and prevention, with remediation nabbing a smaller piece of the cyber budget pie.
That’s according to the study “The State of Cybersecurity Today” from Information Services Group (ISG), for which 204 executives from the world’s 2,000 largest companies were polled. Among respondents, 24% were C-level executives, such as CISOs and CIOs.

Key findings from the study include:
- Detection and prevention currently take up around half of enterprise security budgets, with response and recovery accounting for around 30%. The reason? Cyber leaders believe prevention and detection have a bigger cybersecurity impact.
- When asked to name their organizations’ emerging top risk in the next two years, a majority of respondents (56%) picked attacks that leverage artificial intelligence and machine learning.
- The vast majority of enterprises polled – 95% – experienced multiple cyberattacks in the past 12 months, with phishing (74%), malware (60%) and software vulnerability exploits (50%) being the most common.
- Bucking a trend where department budgets are shrinking by 7% annually on average, security budgets rose 4.6 on average in 2023 compared with 2022. Moreover, 83% of enterprises polled grew their security budgets, and only 4% cut it.
To get more details, read the ISG announcement and a summary of the report.
3 – CISA to AI vendors: Put security at the heart of your software
Artificial intelligence tools are, at their core, software products, and as such their developers must build them secure by design.
That’s the reminder CISA experts Christine Lai, AI Security Lead, and Dr. Jonathan Spring, Senior Technical Advisor delivered in their recent blog “Software Must Be Secure by Design, and Artificial Intelligence Is No Exception.”
In practice, this means that vendors of AI systems must prioritize their customers’ security as a core requisite, and emphasize security throughout their products’ lifecycle – “from inception of the idea to planning for the system’s end-of-life.”

“It also means that AI systems must be secure to use out of the box, with little to no configuration changes or additional cost,” the authors wrote.
For more information about AI system security:
- “Is AI vulnerability management on your radar screen?” (Tenable)
- “Adversarial AI Attacks Highlight Fundamental Security Issues” (Dark Reading)
- “It's time to harden AI and ML for cybersecurity” (TechTarget)
- “Vulnerability Disclosure and Management for AI/ML Systems” (Stanford University)
4 – Report: Ransomware attacks jumped in July
Ransomware gangs stayed busy last month, with attacks jumping 154% year-on-year and 16% compared with June of this year. For the second consecutive month, the surge was driven by the CL0P ransomware gang’s exploitation of vulnerabilities in Progress Software’s MOVEit Transfer product.
That’s according to the latest “Monthly Threat Pulse” report from NCC Group’s Global Threat Intelligence team, which also found that CL0P was responsible for 34% of observed attacks in July, followed by Lockbit 3.0 (10%).

“We are still seeing many organisations are still contending with the impact of Cl0p’s MOVEit attack, which goes to show just how far-reaching and long-lasting ransomware attacks can be – no organisation or individual is safe,” Matt Hull, Global Head of Threat Intelligence at NCC Group, said in the report.
To get more information about ransomware trends:
- “FAQ for MOVEit Transfer Vulnerabilities and CL0P Ransomware Gang” (Tenable)
- “Cyber attacks in 2023 develop quicker as average dwell times plummet” (ComputerWeekly)
- “Ransomware Attacks Skyrocket in 2023” (Infosecurity Magazine)
VIDEOS
Cyber Watch: $10M Bounty on CL0P Gang, Best Practices for Ransomware Incident Response, and more (Tenable)
Anatomy of a Threat: MOVEIt (Tenable)
5 – White House, cyber agencies want your input on open source security
As the U.S. government crafts plans to boost the security of open source software (OSS), it’s seeking comments from the public on how to best accomplish its goals.
The White House Office of the National Cyber Director (ONCD), CISA, and other federal agencies issued a formal request for information (RFI) about OSS security and memory-safe programming languages, such as Java and Python.

The U.S. federal government is one of the largest users of OSS, which provides the foundation for 96% of the world’s software, CISA Executive Assistant Director of Cybersecurity Eric Goldstein said in a statement.
“We envision an ecosystem in which creating secure open source code and regularly assessing the security of existing open source code is the norm rather than an added burden,” Goldstein said.
Some of the topics outlined in the RFI include:
- Rewriting critical OSS components in memory-safe languages
- Reducing OSS vulnerabilities at scale via, for example, boosting secure-by-default configurations in OSS development
- Strengthening the OSS supply chain by, for example, incorporating a zero-trust architecture into the OSS ecosystem
- Training software developers on security best practices
“In addition to its many benefits, the ubiquity of open-source software in commercial products, government systems, and military platforms presents unique security risks,” the White House statement reads.
If you’re interested in voicing your thoughts about how to best secure OSS, you have until October 9 of this year to offer your input via the U.S. government’s Regulation.gov website.
For more information about OSS security best practices:
- “Concise Guide for Evaluating Open Source Software” (Open Source Security Foundation)
- “How to Secure Your Open Source Components” (IEEE Computer Society)
- “Addressing Cybersecurity Challenges in Open Source Software: What you need to know” (The Linux Foundation)
- “Securing the Software Supply Chain: Recommended Practices for Developers” (CISA)
- “Top 10 open-source security and operational risks of 2023” (TechRepublic)
6 – CIS: Malware attacks drop in Q2
Malware activity fell by 40% in the second quarter, compared with the previous quarter, and the drop was even steeper – 65% – for the top 10 malware variants specifically.
That’s according to the Center for Internet Security’s “Top 10 Malware Q2 2023” blog report, which ranked crypto miner CoinMiner as the malware variant with the most activity during the quarter. Three variants cracked the quarterly top 10 list for the first time – DarkVision, Ratenjay and Amadey.
Here’s the full list, in descending order:
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI) and EternalBlue
- NanoCore, a remote access trojan (RAT) that spreads via malspam as a malicious Excel spreadsheet
- Zeus, a modular banking trojan that uses keystroke logging
- ViperSoftX, a multi-stage crypto stealer that’s spread within torrents and file sharing sites
- Agent Tesla, a RAT that captures credentials, keystrokes and screenshots
- Ratenjay, a RAT that’s dropped by other malware, executes remote commands and has keylogging capabilities
- Gh0st, a RAT designed to control infected endpoint devices
- Laplas, clipper malware that’s currently spread by SmokeLoader via phishing emails
- Dark Vision, a remote access toolkit whose capabilities include keylogging, screen captures and password recovery
- Amadey, a multifunctional botnet which steals information and downloads other malware
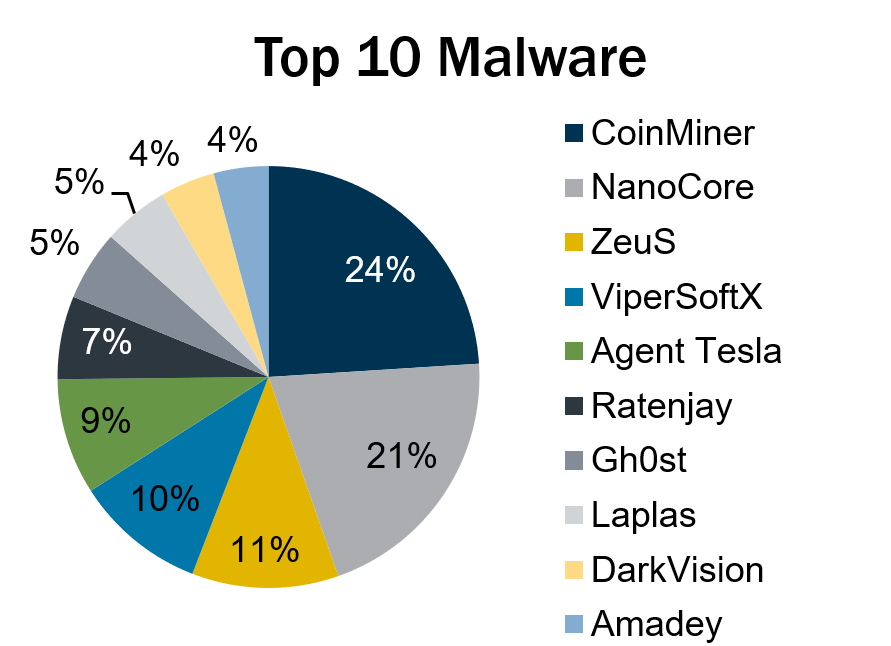
(Source: Center for Internet Security, August 2023)
To get more details, check out the CIS blog report, which offers many details, context and indicators of compromise for each malware strain.
For more information about malware prevention and mitigation:
- “Malware and best practices for malware removal” (VentureBeat)
- “Mitigating malware and ransomware attacks” (U.K. National Cyber Security Centre)
- “10 common types of malware attacks and how to prevent them” (TechTarget)
- “How Can I Protect Against Ransomware?” (CISA)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government


