COVID-19: Cibercriminosos se aproveitam do temor ao coronavírus

Malware and phishing campaigns use global interest in the novel coronavirus to capitalize on fear and uncertainty around the pandemic.
Contexto
In December 2019, reports of an outbreak of a new virus and disease, dubbed COVID-19 by the World Health Organization (WHO), began to emerge. COVID-19 is a novel coronavirus, which has captured global attention and is now considered a pandemic. Since December, COVID-19 has spread to more than 100 countries, with cases being reported every day. With such intense interest in the disease and the uncertainty around it, cybercriminals have found COVID-19 serves as the perfect lure to target users in a variety of ways, including leveraging it as part of malicious emails to phish users and spread digital viruses.
Coronavirus-themed malware campaigns
Emotet campaign
At the end of January 2020, researchers began observing attempts to distribute the Emotet malware in emails targeting users in Japan using COVID-19 as the lure.
新型コロナウイルス関連をテーマにした #emotet のばらまきメール。
— bom (@bomccss) January 29, 2020
昨日と本日で確認どちらも日本語に違和感はありません。
■件名
添
■添付ファイル
別添.doc
■件名
別添 01.29
■添付ファイル
取扱説明書.doc pic.twitter.com/r6Ra3eZf2l
IBM’s X-Force team compiled some indicators of compromise on January 29 and published a summary blog post on February 5. Emotet is part of a chain of three malware strains dubbed the Triple Threat by researchers at Cybereason. Emotet is responsible for bringing the TrickBot trojan into compromised environments, and TrickBot has been identified as a precursor to a Ryuk ransomware infection.
#Ryuk is one of possible payloads delivered by human operators that enter networks via Trickbot. The Trickbot implant downloads Cobalt Strike or PowerShell Empire and begins to move laterally, activating the Trickbot infection for #ransomware deployment: https://t.co/brO143JpO1 pic.twitter.com/TWmjEB7fcT
— Microsoft Security Intelligence (@MsftSecIntel) March 10, 2020
AZORult trojan
Researchers at Proofpoint published a blog post on February 10, highlighting a unique malicious spam campaign leveraging the genuine concerns around COVID-19 and its impact on global shipping.
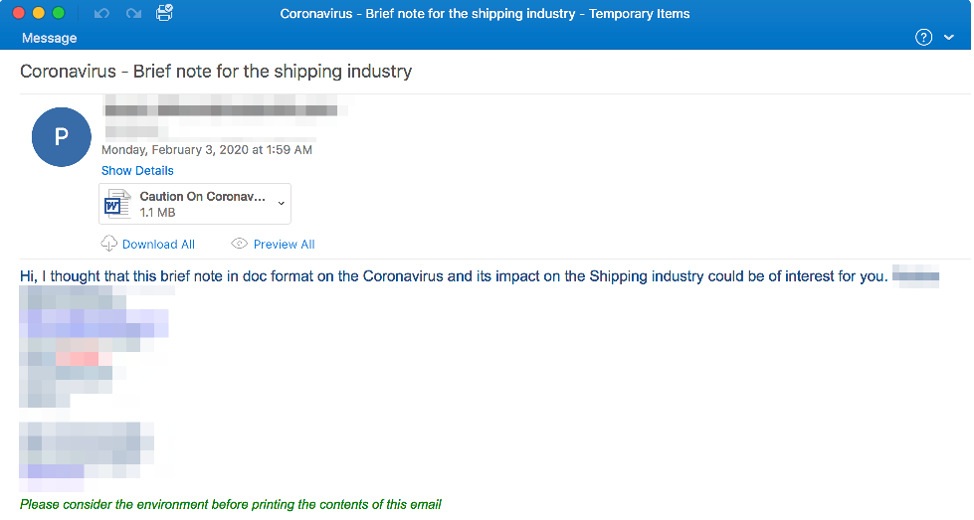
Image source: Proofpoint blog
The malicious Microsoft Word document found in this email exploits CVE-2017-11882, a memory corruption vulnerability in Microsoft Office’s Equation Editor component.
Once exploited, the AZORult trojan is installed on the compromised system. AZORult is an information-stealing trojan first identified in 2016, which exfiltrates sensitive data from a compromised system.
On March 9, researchers at Reason Labs observed cybercriminals continuing to use COVID-19 concerns to spread AZORult again.
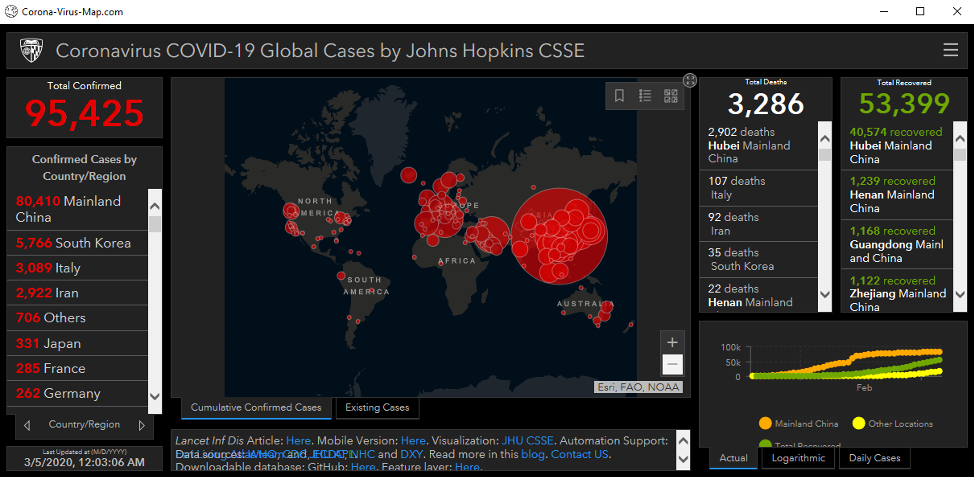
Image source: Reason Labs blog
The cybercriminals distributed a fake version of the Johns Hopkins Coronavirus Map in the form of a malicious executable. However, it is unclear whether they used malicious email or social media to distribute this malicious executable.
Nanocore Remote Access Trojan (RAT)
On February 13, researchers from the Cisco Talos team published a blog post highlighting how threat actors were capitalizing on the coronavirus outbreak. It began by referencing the Emotet campaigns discussed earlier. However, they also found campaigns using COVID-19 fears to distribute the Nanocore RAT.
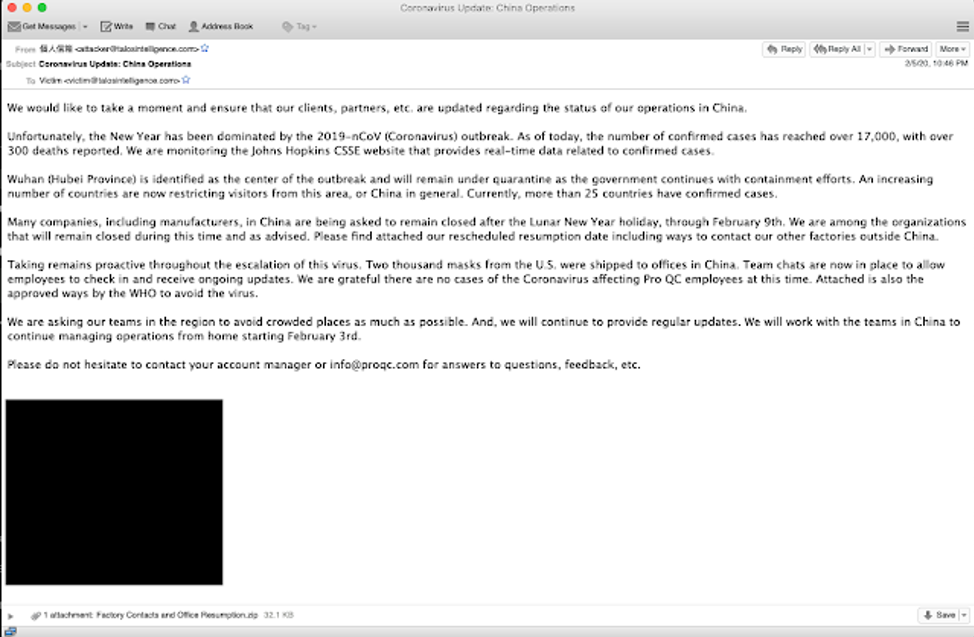
Image source: Cisco Talos blog
The malicious email subject read, “Coronavirus Update: China Operations” and the contents discuss the impact of COVID-19 on a company’s operations in China with a malicious attachment inside a ZIP file. The email references a company, but it is unclear whether the cybercriminals repurposed part of a genuine company email or wrote it themselves.
Lokibot trojan
On February 14, IBM X-Force researchers shared details about another coronavirus-themed malicious spam campaign, this time targeting users in China. According to IBM X-Force, the malicious spam campaign claimed to be from the Ministry of Health of the People’s Republic of China.
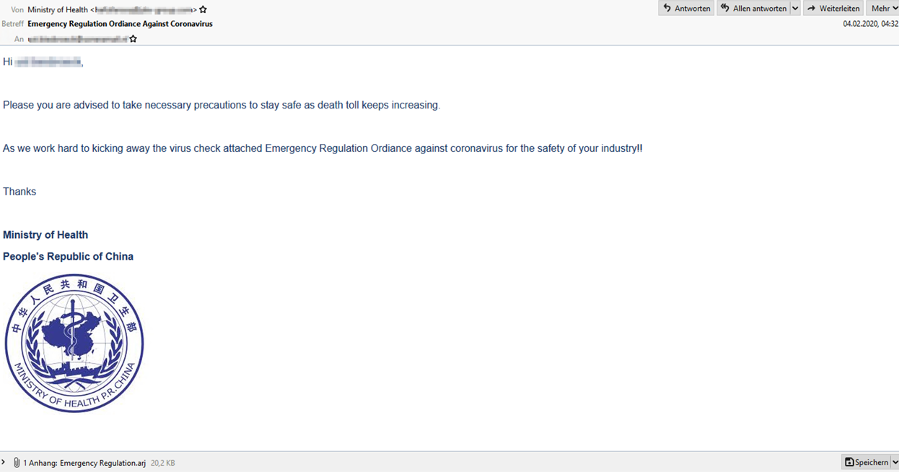
Image source: IBM X-Force Exchange
The email uses official imagery and addresses the user by the username component of their email address. The email provides so-called precautions to “stay safe as death toll keeps increasing” and contains a malicious attachment, referred to as an “Emergency Regulation Ordinance Against Coronavirus,” in the form of an .arj file, a Windows RAR archive file. Once the attachment is opened, it results in a Lokibot trojan infection. Lokibot trojan is an information stealer, keylogger and more that first appeared as a password and cryptocurrency wallet stealer in 2015 on hacker forums.
TrickBot trojan
On March 4, researchers at Sophos published a blog post about a malicious spam campaign targeting users in Italy with a list of precautions they can take to prevent the infection of COVID-19.

Image Source: SophosLabs blog
The email contains a malicious Word document that includes a Visual Basic for Applications script responsible for downloading the TrickBot trojan.
Coronavirus-themed phishing attacks
In addition to COVID-19 themed malware campaigns, cybercriminals are also leveraging the threat in traditional phishing campaigns.
On February 7, researchers at Kaspersky published a blog post detailing a phishing campaign that claimed to originate from the U.S. Centers for Disease Control and Prevention (CDC).
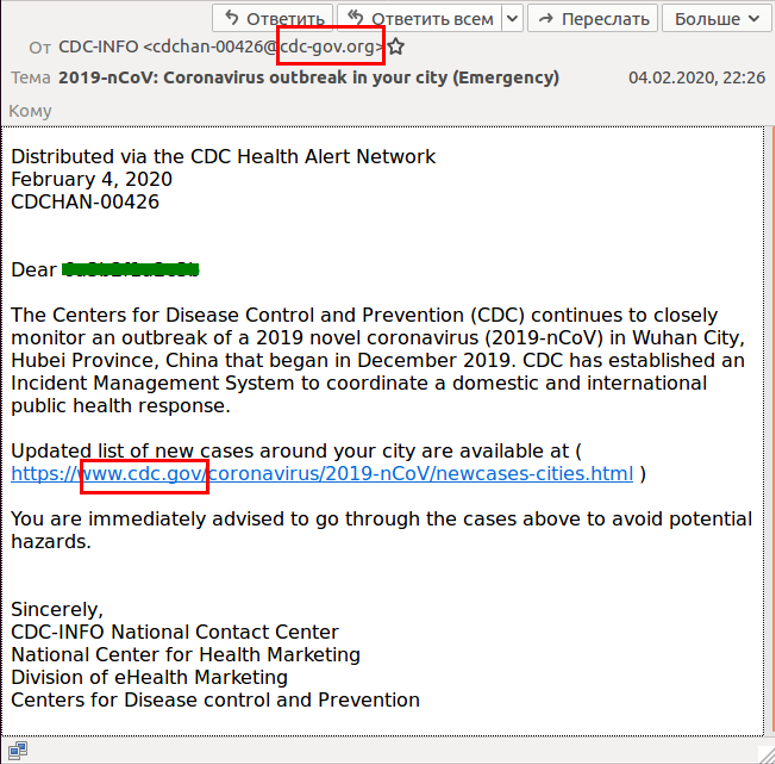
Image source: Kaspersky blog
This phishing email says the CDC is closely monitoring the COVID-19 outbreak and established an “Incident Management System'' for coordinating the public health response both domestically and internationally. It appears to include a link to a cdc.gov webpage. However, this link actually directs users to a website that looks like a Microsoft Outlook page. The page contains a username and password prompt for users to log in. It is an attempt by the cybercriminals to steal login credentials, as they hope to gain access to these accounts and start pouring through emails, looking for valuable information.
On March 5, researchers at Check Point Software Technologies published a blog post identifying newly registered domain names that included the word coronavirus in them. Since January 2020, Check Point researchers say they’ve identified over 4,000 of these so-called coronavirus domains. They found 3% of these domains were malicious, while 5% were suspicious. Check Point says these domains are “50% more likely to be malicious” than other domains registered during this time period.
Warnings from WHO, FTC and CISA
The WHO, the U.S. Federal Trade Commission (FTC) and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) have published advisories warning consumers about the threats posed by cybercriminals seeking to capitalize on the fear and uncertainty surrounding COVID-19. See below:
- WHO: Beware of criminals pretending to be WHO
- FTC: Coronavirus: Scammers follow the headlines
- CISA: Defending Against COVID-19 Cyber Scams
Stay informed about digital threats related to COVID-19
As we’re still in the earliest stages of the COVID-19 outbreak, it’s important to understand that these types of attacks will continue for the foreseeable future. Cybercriminals love to prey on the fears and uncertainty surrounding major global events, and as COVID-19 continues to pose a threat, cybercriminals will continue to leverage it as part of their campaigns.
The best way to protect yourself against digital threats leveraging the interest in COVID-19 is to stay informed. If you receive an email about COVID-19, be skeptical, especially if it contains an attachment. Visit your local government health organization’s or WHO’s website for the latest information about COVID-19.
Junte-se à equipe de resposta de segurança da Tenable na Tenable.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 30-day trial of Tenable.io Vulnerability Management.
- Threat Intelligence
- Threat Management
- Vulnerability Management


