Capture the Flag with Mr. Robot

The hacker-favorite TV show, Mr. Robot, is back on with a great season three opener that features a Capture-the-Flag contest. As the show begins, Elliot decides he needs to stop stage 2 from taking place. Needing a computer to close the backdoor he left in Season 2, Darlene and Elliot travel to the hackerspace in an attempt to find Internet access.
At the hacker space, Elliot talks to a contestant that proclaims he was a CyberPatriot finalist. Elliot and the contestant discuss how to poison the data collected by the Minesweeper game. Elliot is invited into the CTF and captures the final flag, thus securing the hacker space a spot at the CTF.
What is CyberPatriot?
CyberPatriot is a national youth cyber education program created by the Air Force Association (AFA) to inspire K-12 students to pursue careers in cybersecurity or other science, technology, engineering, and mathematics (STEM) disciplines critical to our nation's future. If you'd like to become involved with the CyberPatriot program, visit their website to learn more.
The Capture The Flag Hack
The CTF flag Elliot completed was an actual flag used in a CTF in 2012. Python's pickle command can do more than you might think. By crafting a special command string and tricking a service into unpickling that string, you can access files on the remote server. In this episode, Elliot tells a participant in the CTF challenge to do just that for the Python remote service running the classic Windows game Minesweeper. When the hacker protests that they thought of that, but they don't have the encryption key, Elliot tells him how to get the key: save an almost-finished game to get the encrypted version of the pickled field dictionary, and then XOR that with the pickled version of the reconstructed field dictionary to get the encryption key. More details about the hack can be found at 29C3 CTF.
The Back Door
In the episode, Elliot talks about the backdoor left when deploying the femtocell. A backdoor can often be hidden on a system and disguised as a regular service, other times the hacker may leave some random port opened up. In the example below, I am using Netcat to simulate an unauthorized backdoor.
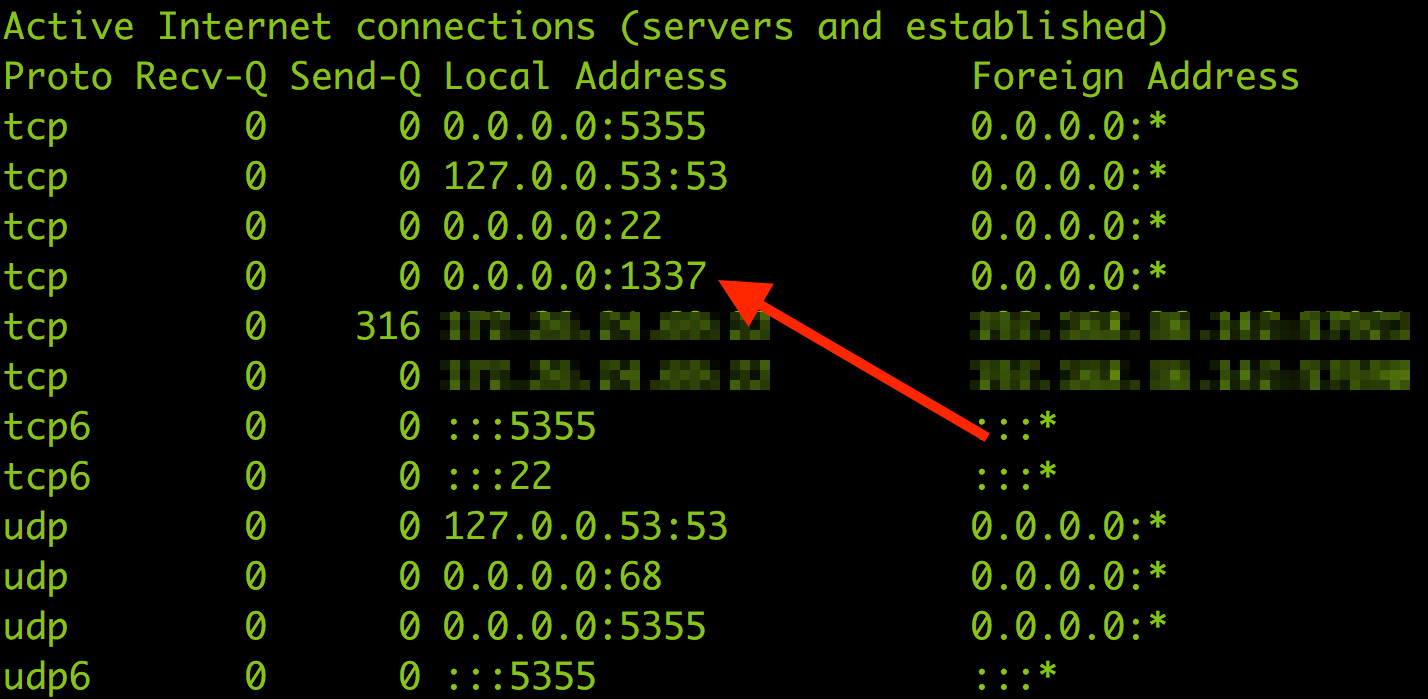
In this example, you can see how to use netstat to look for a port that doesn't seem correct. Port 1337 is a common port used throughout the industry and the one we'll be using as our example port. As you'll see below, port 1337 is not authorized.
While the netstat command is great and useful on a local host, running netstat commands on all computers in your network is not practical. Tenable.io™ has the ability to do port scans, techniques of which are discussed in this blog post. The results of a port scan using Tenable.io would show that port 1337 and port 22 are open.
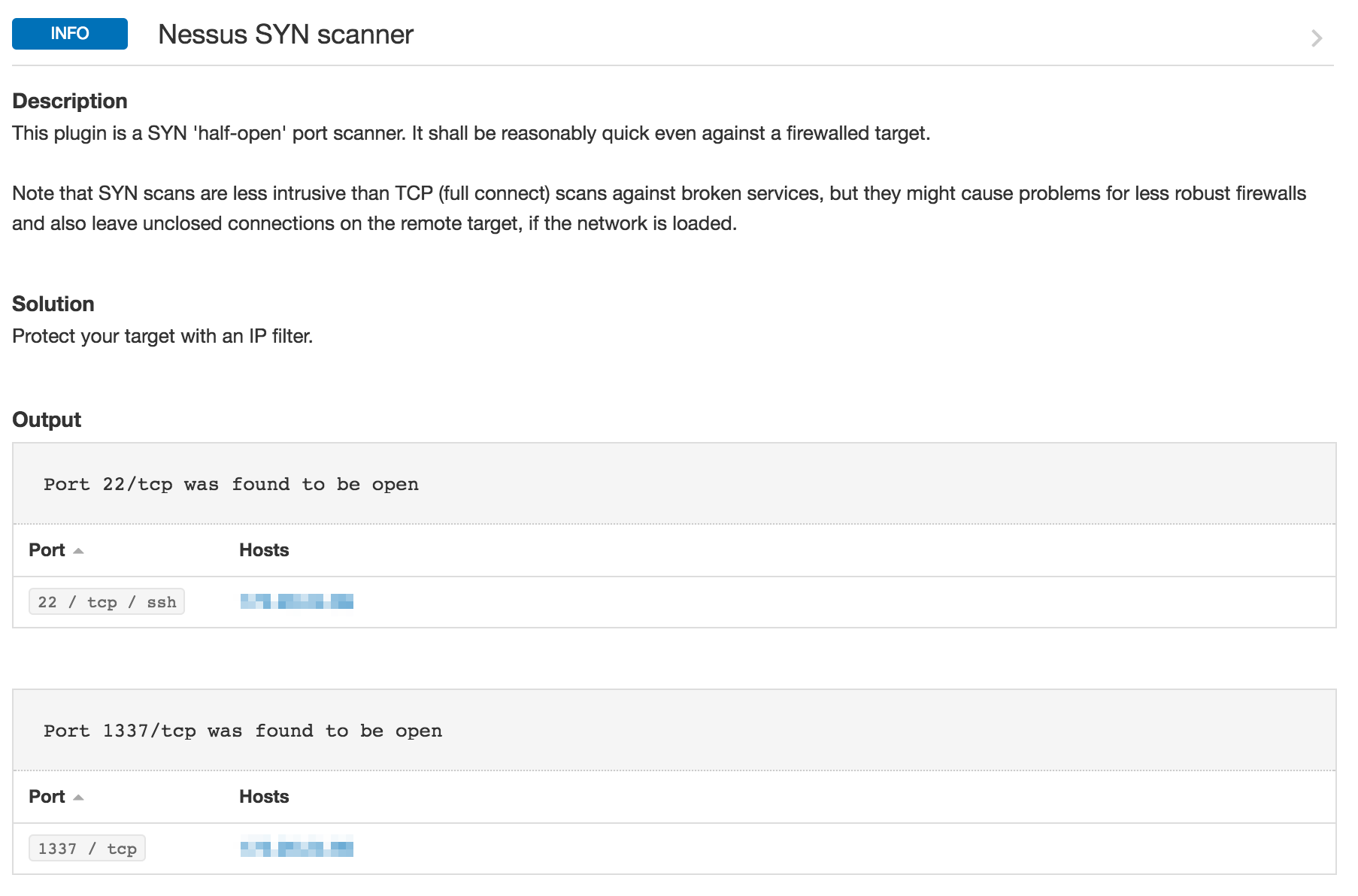
Wrapping Up
Using Tenable.io, you can perform different types of port scans within your network. The scans range from TCP, SYN Scans and netstat commands. By reviewing the results for anomalies, you are able to detect the outlying ports. With Tenable.io, customers are able to figure out whether Mr. Robot left any backdoors open in their network.
Tenable.io provides visibility into any asset on any computing platform and allows you to schedule scans on a regular basis, ensuring you always have the most useful, up-to-date information. Start a free 60-day trial of Tenable.io for your organization today.
- Tenable Vulnerability Management


