by Stephanie Dunn
March 1, 2017
Using patch management solutions, organizations can easily manage systems, install software, and deploy patches to systems automatically. Yet even with the best patch management solutions in place, organizations can easily miss vulnerabilities on systems and devices that only connect in between patch cycles. Tenable's Tenable.sc Continuous View (CV) provides organizations with the ability to track vulnerabilities on transient devices and stand-alone systems missed by patch management solutions. This dashboard presents a summary of vulnerabilities reported by Dell KACE, which can be used to determine whether vulnerabilities are being patched effectively.
Dell KACE K1000 provides organizations with a centralized console to manage and deploy patches to systems across the enterprise. As organizations continue to support mobile workforce requirements, an increasing number of devices may connect to networks outside of the organization and not be patched as frequently. Using Tenable's Tenable.sc CV, organizations will obtain a comprehensive summary from both KACE and Tenable Nessus that can be used to compare whether KACE is patching systems effectively. Installing Nessus Agents on stand-alone or transient systems will report vulnerabilities that may have been missed by patching solutions. By continuously monitoring and rescanning systems, organizations can establish an effective and repeatable process to maintain an acceptable patch level.
The Dell KACE Patch Management Overview dashboard provides a comprehensive look at vulnerabilities detected by Dell KACE K1000 appliances. Information obtained from KACE will report on detected vulnerabilities from the Windows Bulletin plugin family. Data collected from Nessus can be used to compare and identify hosts reporting potentially outdated or inaccurate data. Systems are scanned to identify managed clients and event data. Patch reports are collected from managed hosts that will provide analysts with a full summary of hotfixes, security advisories, and other patches that need to be applied. Data will also report on hosts not communicating properly or that may have fallen out of scope. Organizations can use this dashboard to proactively address and strengthen overall network security and patch management efforts across the network.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Discovery & Detection. The dashboard requirements are:
- Tenable.sc 5.4.2
- Nessus 8.6.0
- LCE 6.0.0
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution that will assist in monitoring patch management solutions. Tenable.sc CV is continuously updated to detect advanced threats and vulnerabilities. Active scanning periodically examines systems to determine vulnerabilities and compliance concerns on network assets. Agent scanning enables scanning and detection of vulnerabilities on transient and isolated devices. Host data and data from other security products is analyzed to monitor events captured from patch management solutions on the network. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to support proactive patch management efforts.
The following components are included within this dashboard:
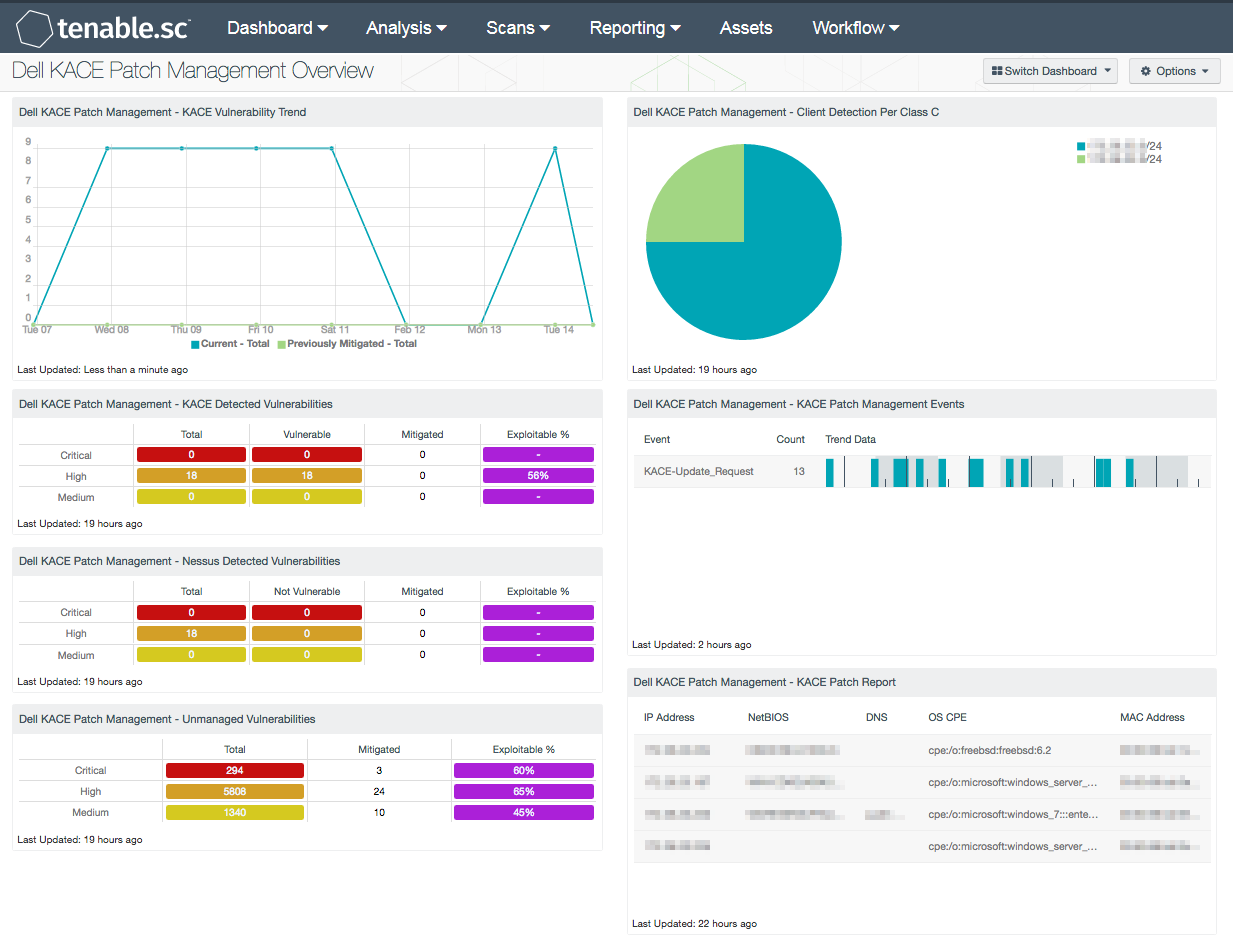
- Dell KACE Patch Management - KACE Vulnerability Trend: This chart presents a trend of both current and previously mitigated vulnerabilities reported by Dell KACE K1000 systems over the last seven days. Information presented within this component can provide organizations with a comprehensive view into how often systems are being scanned, patched, and rescanned. The “Current” trend line will report on the number of vulnerabilities collected from KACE using the “Never Mitigated” filter. The “Previously Mitigated” trend line includes the number of vulnerabilities that have moved from the mitigated section to the active section. Previously Mitigated or recurring vulnerabilities can be the result of systems not being restarted after a patch was applied, virtual systems reverting to previous snapshots, or services that were disabled or failed to restart. Organizations can use this component to focus efforts on remediating both current and previously mitigated vulnerabilities.
- Dell KACE Patch Management – KACE Detected Vulnerabilities: This component provides a summary of Microsoft vulnerabilities detected by Dell KACE K1000 servers. The rows include vulnerabilities at each severity level discovered within the Windows: Microsoft Bulletins Plugin Family. The columns include the total number of vulnerabilities discovered, number of vulnerabilities discovered by Nessus that KACE is reporting as vulnerable, number of mitigated vulnerabilities, and percentage of exploitable vulnerabilities. Information presented within this component can be used to discover whether vulnerabilities are being patched in a timely manner through KACE. This data can also be used to identify any systems reporting outdated vulnerability information.
- Dell KACE Patch Management – Nessus Detected Vulnerabilities: This component provides a summary of Microsoft vulnerabilities detected by Nessus that have been reported as not vulnerable by Dell KACE K1000 systems. The rows include vulnerabilities at each severity level discovered within the Windows: Microsoft Bulletins Plugin Family. The columns include the total number of vulnerabilities discovered by KACE, number of vulnerabilities discovered by Nessus that KACE is reporting as not vulnerable, number of mitigated vulnerabilities, and percentage of exploitable vulnerabilities. Information presented within this component can be used by the analyst to identify how often systems are being patched by KACE, and whether current security settings need to be modified.
- Dell KACE Patch Management – Unmanaged Vulnerabilities: This component provides a summary of vulnerabilities detected by Nessus on hosts not managed by patch management systems. The rows include vulnerabilities at each severity level discovered within the Windows: Microsoft Bulletins Plugin Family. The columns include the total number of vulnerabilities discovered on unmanaged systems, number of mitigated vulnerabilities, and percentage of exploitable vulnerabilities. This matrix provides targeted information analysts need to compare the effectiveness of patch management efforts, and whether current security settings need to be modified.
- Dell KACE Patch Management - Client Detection Per Class C: This chart presents a Class C summary of hosts managed by a Dell KACE K1000 system. Nessus actively scans hosts to determine whether KACE clients are installed. Using this component, analysts will be able to determine how much of the network is covered by the KACE patch management solution. Using Nessus plugin 19506, information is collected on hosts managed by KACE. By drilling down, analysts can obtain additional information on managed hosts, and can be used to identify hosts may not be fully patched or included in the patch management process.
- Dell KACE Patch Management – KACE Patch Management Events: This component includes a summary of events reported by Dell KACE K1000 over the last 72 hours. The list is ordered so that the events reported the highest number of times from KACE are at the top. Log events from KACE are forwarded to the LCE server. LCE can detect changes in patch management solutions that analysts can monitor to determine if further action is needed. Event data in this component may include information on update requests from managed systems. Analysts can modify this component to include specific normalized events per organizational requirements.
- Dell KACE Patch Management – KACE Patch Report: This table presents a list of hosts managed by Dell KACE K1000 where a patch report summary has been collected. Other components within this dashboard report on Microsoft Bulletin vulnerabilities on Windows hosts managed by KACE. Using Nessus plugin 76869, this component will provide a full summary of missing patches from managed systems. By clicking on the Browse Component Data icon and changing the tool to Vulnerability Detail List, analysts will obtain a full summary of hotfixes, security advisories, and other patches that need to be applied. Data will also report on hosts not communicating properly or that may have fallen out of scope. Using this information, analysts will obtain the critical context needed to strengthen remediation efforts within the organization.