by Cody Dumont
October 13, 2016
Organizations rely on robust authentication to protect critical systems and data. However, there are many factors that often contribute to weakened user authentication on an organization's network. Default credentials that have not been changed and are well known to attackers can allow systems to be exploited. Certain users may be members of groups that allow them too many privileges, leading to mistakes or malicious insider activity. Weak passwords, poor authentication practices, and vulnerable authentication mechanisms can put an organization at risk for network compromise and data theft. Use of shared accounts on the network makes tying network actions to specific users difficult, which makes network monitoring and incident response harder.
The French Network and Information Security Agency (Agence nationale de sécurité des systèmes d’information or ANSSI) developed the "40 Essential Measures for a Healthy Network" to assist organizations in safeguarding the security of information systems within a network. Following these measures, or rules, for a healthy network will provide basic protection for an organization's critical data. ANSSI states that the majority of IT attacks that have involved ANSSI stepping in could have been prevented had the IT measures set out in the guide been applied.
This dashboard aligns with Section IV of the ANSSI 40 Essential Measures for a Healthy Network: Authenticate the User. This section contains six rules:
- Rule 8 enables attributing actions to users more easily by eliminating generic and anonymous accounts. User accounts should be unique and not shared, so that actions from a specific user can be easily identified.
- Rule 9 emphasizes setting rules for the choice and length of passwords. This rule references the "Security recommendations for passwords" (Recommandations de sécurité relatives aux mots de passe) document, which provides best practice recommendations on password security.
- Rule 10 emphasizes putting technical methods in place so that authentication rules are followed. These methods include enforcing password changes on a regular basis and ensuring the use of strong passwords.
- Rule 11 advises not storing passwords in files, emailing passwords, or using features in applications such as browsers that offer to store passwords. Passwords stored "in plain sight" on computer systems could easily be found and misused.
- Rule 12 addresses updating default passwords and credentials on devices. Many systems arrive with default credentials that are well-known and frequently exploited by attackers. Any default credentials on a system must be changed before the system is put into the production environment.
- Rule 13 recommends using smart card authentication technology where possible. When implemented correctly, this type of two-factor authentication (smart card plus PIN code) is stronger than just the single-factor authentication of a password.
This dashboard helps organizations improve their network authentication by enabling more effective monitoring of users and identification of weaknesses in authentication mechanisms and practices. The information presented includes user account and group information, account and password vulnerabilities, and authentication compliance issues. Organizations can use this information to improve their authentication practices, ultimately safeguarding critical assets and data.
Components on this dashboard display the top most active network users, new users, and user account and group information. This data can be used to discover unauthorized users and users that are members of privileged groups that they should not be members of. Indicators for account and credentials vulnerabilities are displayed so that these vulnerabilities, which include default accounts and passwords, can be addressed as soon as possible. In addition, the top compliance concerns on the network dealing with authentication, passwords, and smart card settings are presented. Potential compliance concerns may include improper password length or complexity requirements, improperly allowing applications to store credentials, or failing to require smart cards when policy does require them. The information on this dashboard will help the organization strengthen user account management and improve network authentication practices.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.3.2
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.1
- Compliance data
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist an organization in monitoring and strengthening user authentication policy and procedures. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to find account and credentials vulnerabilities and enumerate system information. Audit files can be used to assess compliance with authentication policies. Passive listening provides real-time monitoring to collect information about systems and vulnerabilities. Host data and data from other security investments is analyzed to monitor user activity across the network. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to secure user authentication and safeguard critical assets and information.
Components
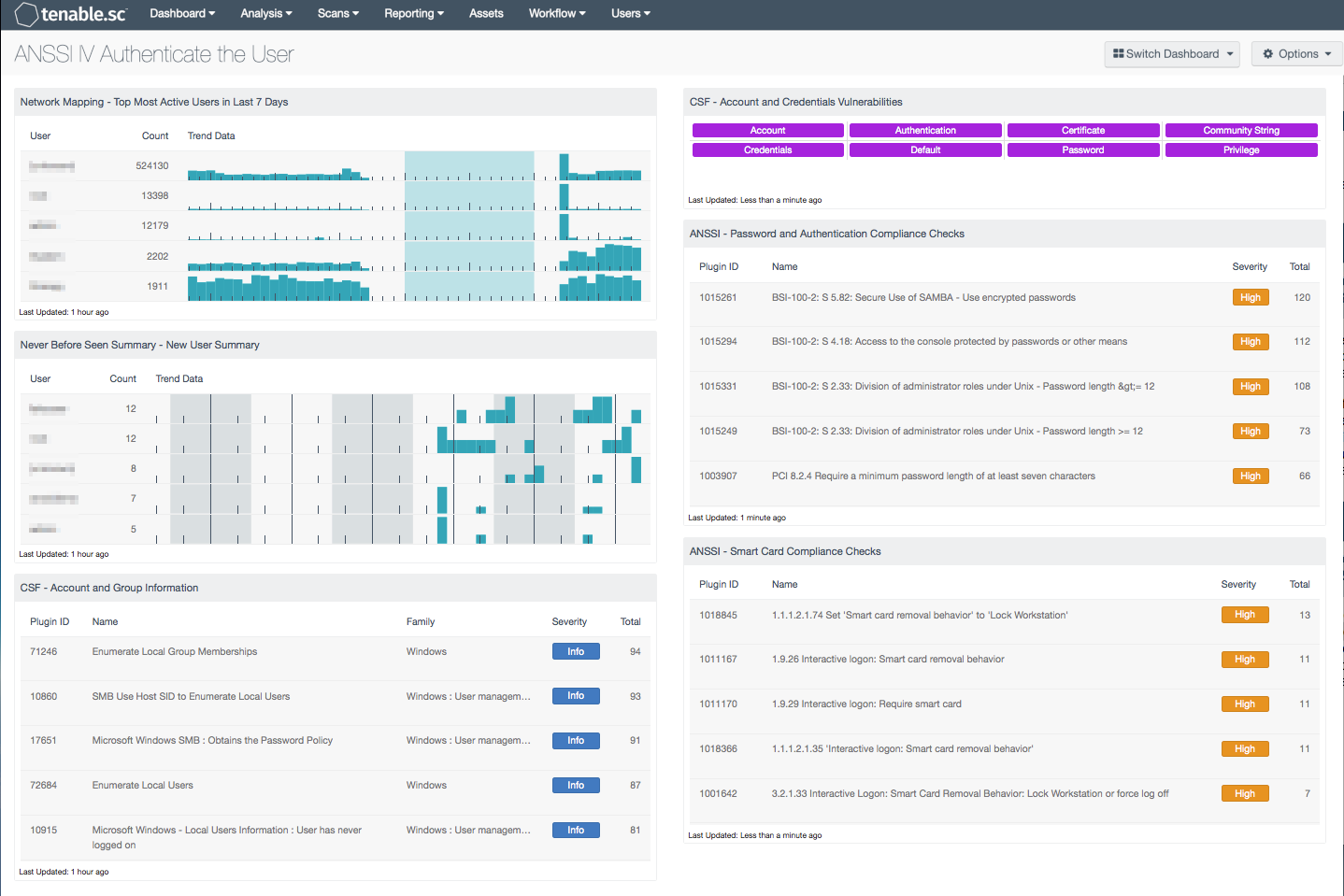
Network Mapping - Top Most Active Users in Last 7 Days: This table presents the most active users on the network in the last seven days based on the number of network user events generated. The table is sorted so that the user with the highest count of events is at the top. Trend lines of events per user over the last seven days are included. This information can assist an organization in tracking normal activity, as well as discovering any unusual activity. Note that the number of users that the table displays can be adjusted in the component based on the size of the organization, and should typically be 10-15% of the total users on the network.
Never Before Seen Summary - New User Summary: The New User Summary table presents a trend of new user events detected within the last 72 hours. The “New_User” event records the first time a user logs in to a new host and/or a new account type on a host. The “New network user” event records the first time a user is ever seen on the network. The “New_User_Source” event records the first time a user logs in from a new host. The “New_SSH_User” event records the first time that an SSH username is detected that has not been previously detected on the host. Analysts can drill down to obtain additional information on the user account, and IP address associated with the event. All of these new user accounts should be verified to determine whether the account is authorized on the network.
CSF - Account and Group Information: This table displays detections of account and group information, such as accounts that have never been logged into, disabled accounts, and group user lists. This information is obtained through Nessus credentialed scans. Most of these detections will contain lists of accounts in their output. The Obtains the Password Policy detection will contain the retrieved password policy in its output. Clicking on the Browse Component Data icon on the component will bring up the vulnerability analysis screen to display the detections and allow further investigation. In the analysis screen, setting the tool to Vulnerability Detail List will display the full details for each detection, including its description and output.
CSF - Account and Credentials Vulnerabilities: This component displays warning indicators for vulnerabilities actively and passively detected on the network related to accounts and credentials. A purple indicator means that one or more vulnerabilities contain the specified keyword. Clicking on a highlighted indicator will bring up the vulnerability analysis screen to display details on the vulnerabilities and allow further investigation. In the vulnerability analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities are present. Setting the tool to Vulnerability Detail List will display the full details on each vulnerability, including a description, the solution to fix the vulnerability, and in some cases, links to more information.
ANSSI - Password and Authentication Compliance Checks: This table displays the top compliance failures and warnings related to passwords, credentials, and authentication. Potential compliance issues may include improper password length, complexity, or age requirements, improper account lockout settings, or improperly allowing applications to store credentials.
ANSSI - Smart Card Compliance Checks: This table displays the top compliance failures and warnings related to smart cards. Potential compliance issues may include not requiring smart cards when policy does require them, or improper behavior when a smart card is removed.