Mr. Robot and the Insider

In Mr. Robot Episode 9 of Season 2, Angela starts to show her true intent; we learn that she is trying to expose a corporate cover-up that affected her family. While the details of the cover-up have not been revealed, her motives have come to light. For episode 6, our blog talked about a device called a Rubber Ducky. This device is a Human Interface Device (HID) that masquerades as a USB storage device. Along with good social engineering skills and a Rubber Ducky, as Angela demonstrates, most corporate security policies can be subverted and security controls bypassed. Insider threats are a real and serious concern to organizations, and are the common initial vector used with a data exfiltration attack.
The insider attack
An insider threat usually starts with some type of social engineering. Social engineering “refers to psychological manipulation of people into performing actions or divulging confidential information. A type of confidence trick for the purpose of information gathering, fraud, or system access.” Monica, Mr. Green’s assistant, is coerced by Angela to leave her desk and go to the foyer to get some documents, granting Angela access to Mr. Green’s office. Once in the office, Angela inserts the USB device (Rubber Ducky) into Mr. Green’s computer. The Rubber Ducky can be programmed to do all sort of attacks, basically anything a malicious person can do from a command line. In this case, the attack was to exfiltrate any cached credentials in hopes of gaining access to the network from a different location.
Tenable solutions
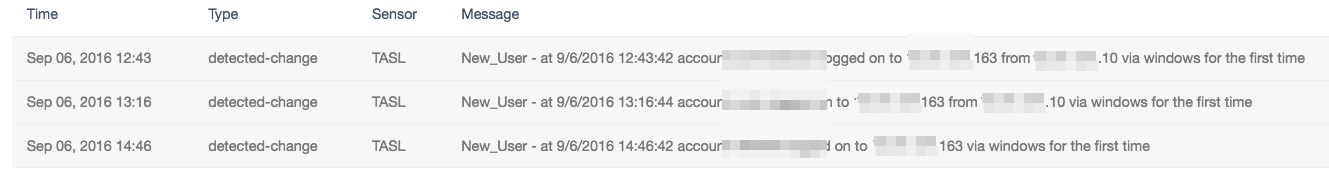
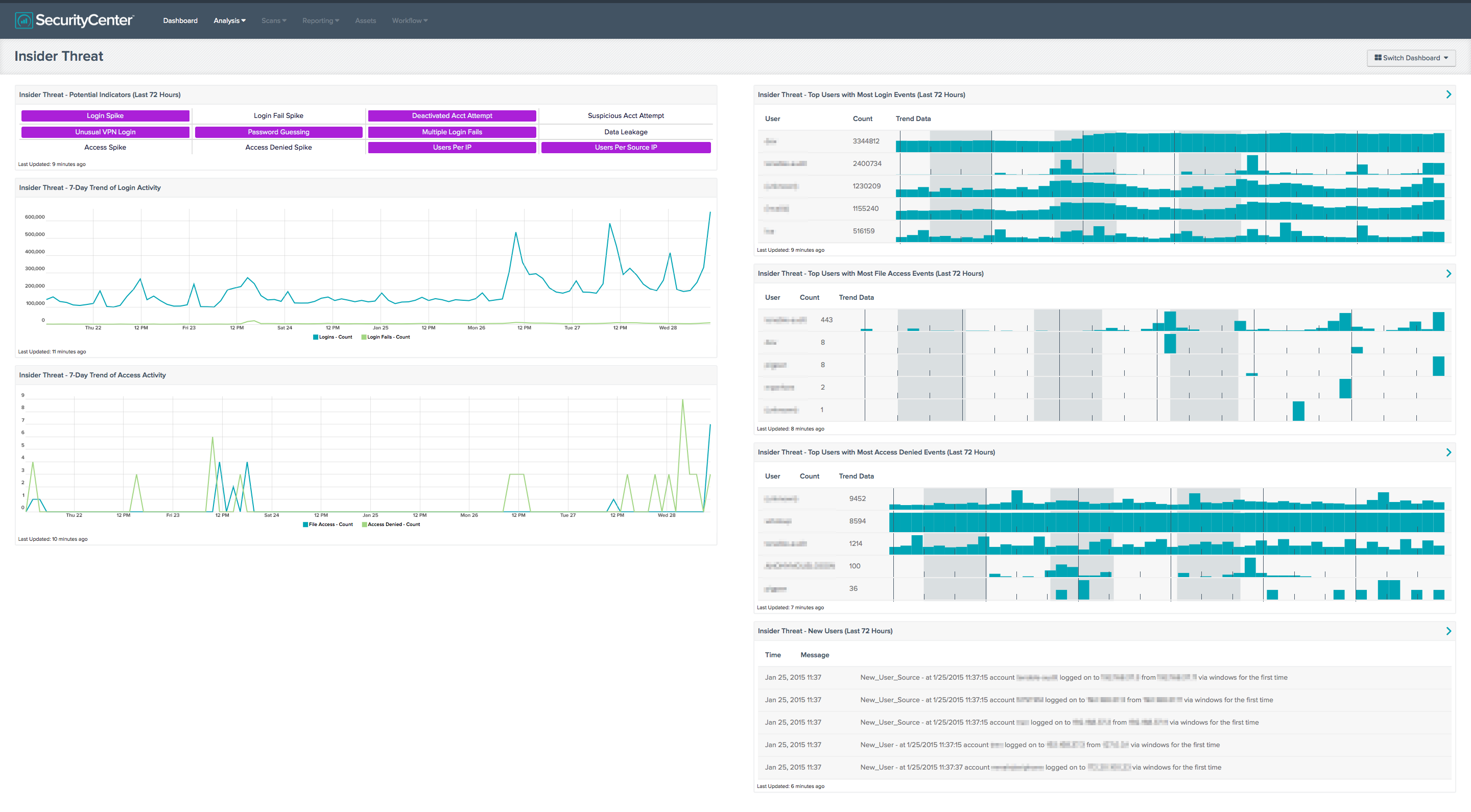
Tracking insider movements is key to good network security. Users often use only one or two computers during the work day; so if and when a user accesses a different computer, the security team should have a log ready to record the action. Organizations that run SecurityCenter Continuous View™ (SecurityCenter CV™) can use the Log Correlation Engine™ (LCE®) to monitor systems by collecting and correlating logs. LCE creates an event called “New-user” which tracks the time, date, username, and associated IP addresses used during authentication. Alerts can be configured in SecurityCenter to notify the Security Operations Center when such an event occurs. By creating a list of sensitive accounts, special alerts can be also be created to launch Nessus® scans and email key players of the possible breach:
Insiders can be employees, contractors, or partners who already have access to your organization's network and resources. Even as Angela is almost caught by an executive looking for Mr. Green, the fact that Angela and Monica look similar played to Angela’s advantage. The importance in this case is the application of physical security policies. For example, in highly sensitive areas where only one or two people should be present, having a picture on the wall or some other method of authentication could have prevented this attack.
The Insider Threat Dashboard brings together passive scanning and log correlation to assist with monitoring users on the network and combating the insider threat. Insider threats are different from external security threats in that they come from what would normally be considered a "trusted source." The threat is that insiders can either accidentally or intentionally exfiltrate data, change firewall rules or other configuration changes to further an exploit. Organizations trying to detect these threats face the challenge not only of differentiating attacks from "normal" traffic, but also of ensuring that security analysts and system administrators are not inundated with false positives from users performing legitimate tasks.
In this example, Angela eventually accesses file shares from her office using Mr. Green’s account. The Security Operations Center could have received email alerts and then contacted Monica to see if Mr. Green’s computer was changed or to find out where Mr. Green was currently located. SecurityCenter CV could have facilitated either of these scenarios using alerts and a properly deployed LCE and LCE clients.
Hacktivists
The episode closes with Angela revealing her true intent, acting as a whistleblower and reporting to the United States Nuclear Regulatory Commission. As the NRC analyst looks over the documents, he admits there are some clear violations and takes the documents to the director. Angela then meets the assistant director and as they talk, Angela realizes she made a mistake and tries to grab the USB drive and leave. Later that evening, Dominique comes to dinner at Angela’s house uninvited. Angela knows her time has come, and she has crossed the line from activist to hacktivist. Dominique mentions Angela has been under close surveillance for two months, and the game is up.
Is your organization at risk from a hacktivist or other insider threat? Is Mr. Robot working with an insider on your network; is data being exfiltrated? SecurityCenter CV can provide your security team with an accurate account of user activities and vulnerabilities, thereby reducing the effectiveness of such attacks.
- Insider Threats
- SecurityCenter